
RockYou2024: How I Might Have (Accidentally) Been the Source of a 10 Billion Password Leak
The recent “RockYou2024” leak is the latest major data breach that has the world of cybersecurity talking. A huge 155GB file containing 10 billion supposed plaintext passwords – the largest compilation of passwords ever recorded – was posted on a forum on July 4th, 2024.
As someone who previously worked on password-generation tools, I couldn’t help but notice some curious patterns within the leak that warranted a closer look. Buckle up. This story dives into the surprising intersection of password leaks and the tools that might inadvertently (and, hopefully, not maliciously) contribute to them.
RockYou Revisited
For those unfamiliar with the history of password leaks, “RockYou” refers to a notorious data breach from 2009 that exposed millions of usernames and passwords.
Fast forward to 2024, and a file titled “RockYou2024” emerged on a hacking forum, courtesy of a user with the, shall we say, interesting moniker of “ObamaCare.” This digital Pandora’s box supposedly contains a mind-boggling 10 billion entries, clocking in at a hefty 155 GB in size.
After filtering out unreadable lines and passwords shorter than six characters, the actual count dipped to a still-unthinkable 9,929,667,762. So, what exactly is a password wordlist, and why would anyone compile such a massive index?
The Role of Password Wordlists
Password wordlists are like giant dictionaries, but instead of words, they contain potential passwords. Security teams and others might use them for legitimate purposes, like penetration testing, where security professionals try to crack weak passwords to identify an organization’s system’s vulnerabilities.
Unfortunately, password lists can also fall into the wrong hands. Hackers can use them for brute-force attacks, where they try millions of password combinations systematically to gain unauthorized access.
The Grunt Work: Cracking Passwords with Consumer Hardware
You might be wondering, “how can hackers possibly test millions of passwords in a second?”
The answer lies in harnessing the power of readily available technology. Believe it or not, even consumer-grade graphics cards (the kind you might find in a high-end gaming PC) can be used to crack passwords at an alarming rate. Graphics cards are designed to handle complex calculations quickly, and hackers have figured out how to exploit their processing power for nefarious purposes.
However, brute-force attacks only work under specific circumstances. Hackers can’t simply unleash this processing power on a website and magically crack everyone’s password – they need stolen data to do so.
Brute-force attacks become a possibility when a website suffers a data breach and user credentials are leaked, often in a hashed format. Hashed passwords are passwords that’ve been encrypted and turned into strings of letters and numbers to make them unreadable. Passwords are usually stored this way for extra security. Using their powerful hardware, hackers can attempt to crack lists of leaked password hashes to reveal the original passwords.
Fighting Back: Security Measures and Common Sense
Thankfully, there are two lines of defense against brute-force attacks. Firstly, websites can implement strong password hashing algorithms that make cracking significantly more difficult. Secondly, users can take basic security measures to help make their passwords harder to crack.
Using strong, unique passwords for your accounts and enabling two-factor authentication are crucial security steps. While brute-force attacks remain a concern, it’s highly unlikely that a hacker would specifically target you with such a method. Bandwidth limitations also help safeguard users from remote attacks. Websites can easily detect and thwart attacks where hackers bombard a website with millions of password attempts per second.
So, while the “RockYou2024” leak raises eyebrows, it’s not an immediate cause for panic. We can keep our accounts safe by understanding the mechanics of brute-force attacks and taking basic precautions.
The “RockYou2024” Leak: A Mixed Bag of Nothing
The sheer size of “RockYou2024” might suggest it’s a goldmine for attackers. However, a closer look reveals a collection of questionable quality. In response to my tweet about the leak, several other notable security researchers mentioned that the database contains a lot of junk.
I just downloaded rockyou2024 and the content is absolute markovian generated bullshit????
This wordlist is just a worthless 155 gb generated blob, come on guys, absolute bonkers that anyone could be excited about this…
If you want actual useful markovian wordlist extensions,… pic.twitter.com/dTCy6fPzg6
— Ignis (@ahakcil) July 12, 2024
maybe for padding, but not entirely. I'm matching data to two alleged dumps at the moment. still a ton of useless data in it. 200mil practical creds after filtering. ok for local cracking and not much else.
if I had to guess they just took everything they could find for free… pic.twitter.com/Yc0rMnry9t
— dreadnaught (@dr3dn0t) July 13, 2024
The one I snagged was crap. It even had a call to python crypt:
$6$rounds=63816$G^d6RptGiW#1=$VKfJ9Pa9JVDZrNNVkg.onF8EGsne03M0O60jaToigJd1hXRjiSb2LsSDbCa6CBs204GXKpp47VyMScRESflsA/
a python command to encrypt *(crypt)- the number of rounds/iterations then the salt and the…— Vap0rz (@Vap0rz) July 14, 2024
So, why is the leak’s data seemingly useless? Here’s what I found after sifting through the data:
- Abnormal Peaks in the Distribution of Contents: Under normal circumstances, it should be a single smooth bump with its peak on ~9-10. Larger lengths and the presence of abnormal peaks are an immediate red flag that leads me to believe the majority of the content in “Rockyou2024” is not actual password data, people definitely don’t use 200+ character long passwords.
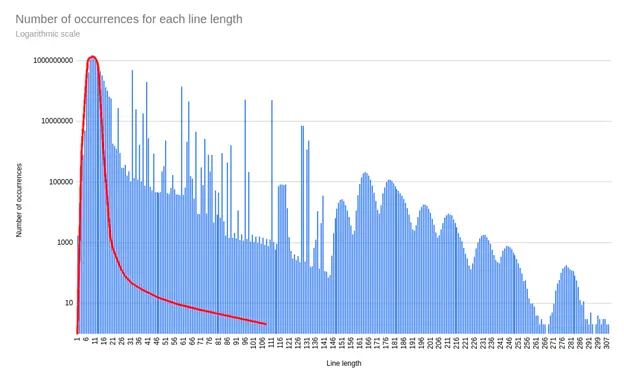
Distribution of contents based on line lengths. The sketched red line is what we would expect from a legitimate password leak, and anything that falls above this line is unlikely to be real password data.
- 70 Million Lines of Junk: After removing the bare minimum of digital clutter, such as lines that contain unreadable characters and lines that are too short to be passwords, the password count dipped to 9,929,667,762.
- Filtering to Find the “Real” Count: After a more thorough round of filtering, and after only filtering for 6-12 character strings (which is where the majority of real passwords reside), the count dropped to 5.9 billion. This is still a significant number, but a far cry from the initial claim of 10 billion passwords.
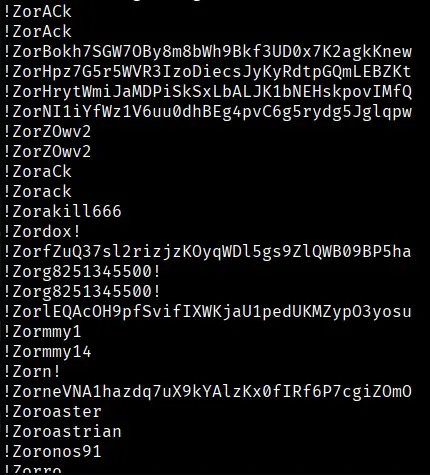
- A Generation Game? Spotting the Artificial: The most intriguing (and frankly, concerning) aspect was the abundance of entries that resembled what password generation tools might produce. Many entries looked suspiciously similar to those my own wordlist generation tool would create. The majority of the file’s data is filled with these passwords, which are like “generated junk” because they’ve likely been scraped from password generators. As such, most of these passwords probably aren’t being used. We should all be concerned about low-quality AI content muddying datasets like wordlists and making them less useful, especially when the intention is to use that dataset for good.
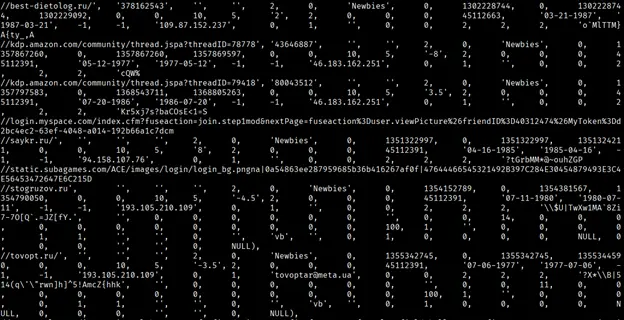
- Rainbow Table Traces: I also found snippets of “rainbow tables” – huge indexes that contain both hashed and plaintext versions of passwords. Password cracking tools usually read these precomputed databases to uncover passwords. However, passwords and hashes are formatted on single lines in entries within “RockYou2024,” meaning password crackers wouldn’t be able to read them. Even if these entries were properly structured, the plaintext passwords are complete gibberish and therefore useless. This suggests they’re junk that was added to pad the leak and make it seem bigger.
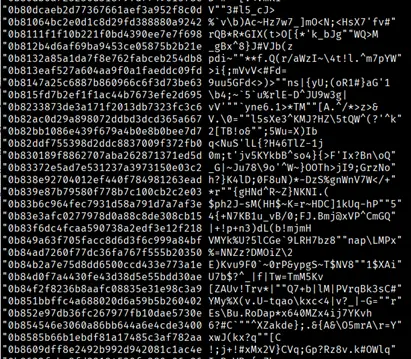
Example of lines containing hashes and their unhashed counterparts (which happen to be completely useless)
A Generated Case of Déjà Vu
The prevalence of generated-looking strings in the “RockYou2024” leak piqued my curiosity. Here’s the thing: in the early days of developing my password generation tool, admittedly, I took a few shortcuts. Think of my approach to creating this tool as like a novice plumber who, in their eagerness to learn, tackles a few early projects without the full repertoire of skills. Maybe they use a specific technique to get the job done, not realizing a more efficient or standard approach exists.
Fast forward to this leak, and I’m seeing a massive collection of passwords exhibiting the exact same “shortcut” I used. The generated passwords contain a recurring string pattern and a lack of commas. It’s like visiting a house, only to find another plumber used the same (slightly unorthodox) method I did in the past. Now, this doesn’t definitively prove my tool was involved in creating the “RockYou2024” leak, but the similarities are certainly striking to me.
Adding another layer to the mystery is the fact that many of these longer generated-looking passwords come to a specific length: 41 characters. Fans of The Hitchhiker’s Guide to the Galaxy will be aware of the significance of the number “42,” cited as the answer to “Life, the Universe and Everything.” Among hackers and geeks, picking the number 42 when in need of a random figure has become a kind of inside joke.
But why would the hackers pick 41, and not 42, as their character limit? Coincidentally, one of the mistakes my early tool made was counting the “null terminator” (a technical character used to mark the end of a string) as part of the password length. This little oversight meant the maximum generated password would always fall one character short – precisely at 41 characters if the number picked was 42. Is this a smoking gun? Absolutely not. But it does add another amusingly specific detail to this whole password generator whodunit.
Conclusion & Takeaways
The prevalence of generated-looking strings in the “RockYou2024” leak is undeniably interesting, especially considering some specific quirks like the missing commas. As the developer of a password-generation tool, I can’t help but notice these similarities.
However, it’s important to be clear: this doesn’t confirm that my tool, or any specific tool, was involved in creating the leak.
The leak itself may be a collection from various sources, and there are many password-generation tools available. That being said, my old tool’s low-quality content seems to match perfectly with what we can see in the “RockYou2024” database.
This incident does, however, highlight a crucial point. Password generation tools are powerful tools, but like any tool, they can be used for good or bad purposes. Ethical hackers and security professionals use these tools for penetration testing, and to help identify weak passwords and improve overall system security.
The key takeaway here is that everyone should prioritize creating strong, unique passwords for each of their online accounts. Resist the urge to reuse passwords, and consider using a password manager to store your collection of complex passwords. By following these basic security practices, you can significantly reduce the risk of falling victim to a brute-force attack, even if your hashed passwords are leaked.
So, while the “RockYou24” leak might be a strange case of digital déjà vu, it serves as a valuable reminder for everyone to prioritize good cybersecurity habits. Stay vigilant and use strong passwords.
After all, unless your password looks like it was generated by a malfunctioning fortune cookie machine, you’re probably safe. But if you’re password reads like “ĶI…NßÛ¡yÃÁalÁÝ” or “!07iprOIfLIQpX8FkJMBnASIbASXetQAJYStMplrF,” you might’ve been leaked in “RockYou2024”. Time to change those passwords!
I’m only joking, of course. I highly doubt that you’re in danger from “RockYou2024” and there’s no need to panic! But, if you really suspect your passwords have been compromised by any leak, act swiftly; change all passwords you believe have been compromised immediately and enable two-factor authentication where possible. Consider using a reputable password manager to enhance security and monitor your accounts for any suspicious activity regularly.


 Previous Story
Previous Story

 Latest articles
Latest articles 

Leave a Comment
Cancel