What is an IP Address & How Does it Work? 2025 Explanation
“IP address” is a term you’ve probably heard often, but what does it mean? Simply put, an IP address is a unique identifier given to every device on the internet, like a digital address. Whenever you’re online — browsing the web, streaming a video, or sending an email — your device uses an IP address to communicate with other devices and servers.
In this article, I’ll explain how an IP address works, how to check yours, and why keeping it secure is essential. Whether you’re concerned about privacy or simply curious, I’ll highlight everything you need to know to understand what an IP address is and how you can use this knowledge to protect your digital footprint. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
Quick Summary: What is an IP Address?
An IP (Internet Protocol) address is a unique number assigned to every device communicating over a network, such as the internet. Think of it as your device’s unique digital address, which lets other devices on a network know who you are and ensures web traffic is directed to the correct destination.
IP Addresses and Their Types: Detailed Explanation
Every device that uses the Internet Protocol for communication gets a unique IP address, ensuring all devices can identify and communicate with each other or over the internet. IP addresses are split into the following main categories:
- Public IP address. This is the IP address that’s accessible over the internet. It’s usually assigned to routers and other devices that communicate directly with the internet, and no two devices have the same public IP address.
- Private IP address. A private IP address is used for communication within a local network and isn’t accessible directly through the internet. It’s reserved for devices like home computers, phones, and printers to communicate with one another.
- Static IP address. Static IP addresses are manually assigned to devices and don’t ever change. They’re commonly used by devices that need a fixed address to ensure uninterrupted access, like web servers.
- Dynamic IP address. A dynamic IP address is temporary and assigned by DHCP (Dynamic Host Configuration Protocol), which allocates it from a pool of available options. It’s used for home devices like smartphones and computers, which don’t require a fixed IP address.
- Shared IP address. Shared IP addresses are those that multiple devices and users use simultaneously. They’re commonly seen in web hosting when multiple websites are hosted on the same server.
- Loopback IP address. A loopback IP address, also referred to as localhost, is a special IP address that loops traffic back to the local machine. The most common example of this is 127.0.0.1.
IPv4 vs IPv6: What’s the Difference?
IPv4 and IPv6 are terms you might have frequently seen across the internet. They’re both versions of the Internet Protocol, with IPv4 being the older and more common and IPv6 being the latest standard that surpasses the limitations of IPv4.
IPv4 uses 32-bit addresses, written as 4 decimal numbers ranging from 0 to 255, separated by periods, like 192.168.1.1. Since it’s a 32-bit address, there can only be 4.3 billion unique IPv4 addresses (2^32). This wasn’t an issue initially, but it’s a problem that must be addressed because most unique IPv4 addresses are being allocated as more devices use the internet.
On the other hand, IPv6 uses 128-bit addresses, written as 8 groups of 4 hexadecimal values separated by colons, like 2001:0db8:85a3:0000:0000:8a2e:0370:7334. Since it’s a 128-bit address, there can be 340 undecillion (3.4 x 10^38) unique IPv6 addresses (2^128), ensuring every device can have a unique IP address without any allocation issues.
How to Check Your IP Address
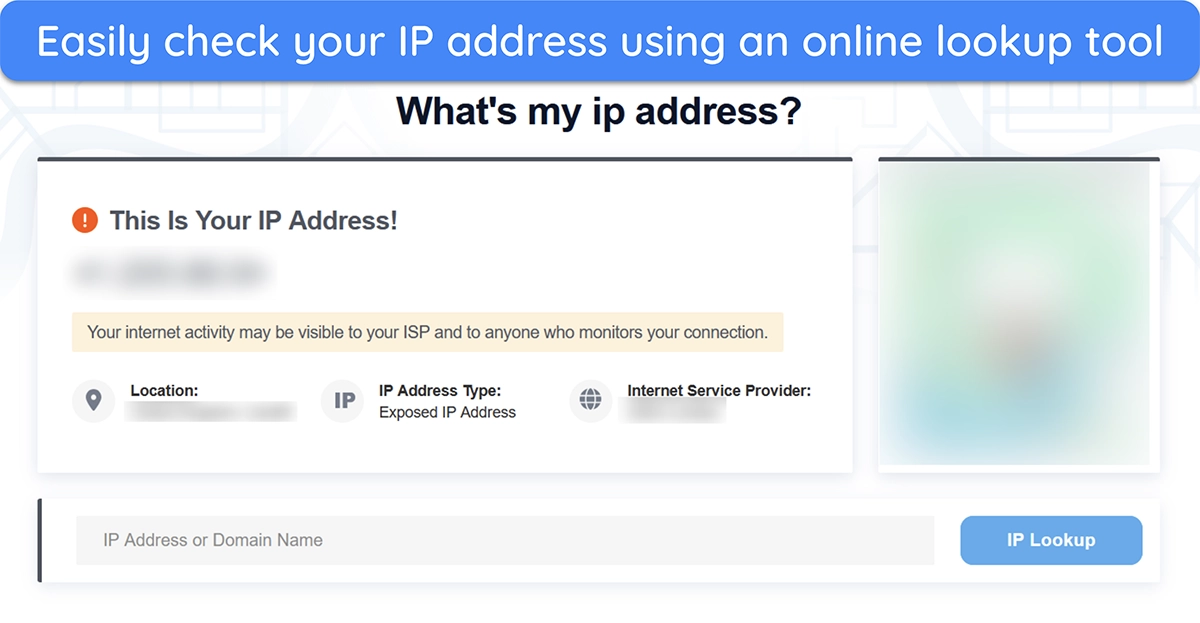
There are multiple ways to check your IP address. The easiest way is to use a reliable online IP lookup tool, which will instantly inform you what your IP address is and highlight whether you need to secure it.
There are also various platform-specific methods to check your IP address.
Windows
- Open Command Prompt. Access the Command Prompt by searching for it in the Start menu or typing “cmd” in the Run window (accessed by pressing Win + R).
- Use the ipconfig command. Type “ipconfig” and hit the enter key to see all your network details, including the IP address.
macOS
- Open the terminal. Access the Mac terminal through Spotlight Search or under the Utilities menu.
- Type the ipconfig command. Type “ipconfig getifaddr en0” for WiFi connections or “ipconfig getifaddr en1” for wired connections to get your local IP address. Also, you can type “curl ifconfig.me” to get your public IP address.
Android
- Access the settings menu. Access your Android device’s settings menu through the app drawer.
- Open WiFi settings. Tap the “WiFi” option to bring up your device’s WiFi settings.
- Tap the gear icon. Tap the gear icon next to the connected WiFi network to bring up all connection details, including your IP address.
iOS
- Access the WiFi settings. Open your iOS WiFi settings by navigating to the Settings menu and tapping “WiFi.”
- Tap the information icon. Tap the information icon “i” next to the connected WiFi network to reveal connection details, such as your IP address.
IP Address Threats and Risks
Securing it is essential because it’s your online identity. You’ll expose yourself to various risks and threats if your IP address gets compromised, some of which include the following:
- Direct attacks. Hackers can attack and potentially crash your network using DDoS (Distributed Denial of Service) attacks and other sophisticated methods if they learn your IP address.
- Location tracking. If your IP address is leaked online, attackers can use geolocation technologies to track down your real location.
- Network access. A compromised IP address gives hackers an entry point to breach your network and access sensitive data on your devices.
- IP misuse. Hackers could spoof your leaked IP address to download copyrighted content or engage in other illegal activities that will be traced back to you instead of them.
Ways to Secure Your IP Address
Considering the threats associated with a compromised IP address, it’s crucial to use the following methods to ensure your IP address is always secure:
- Ensure your apps and OS are up-to-date. Install all the latest operating system and app updates to patch any vulnerabilities that hackers could exploit to get your IP address.
- Use a top antivirus. The best antivirus programs prevent malware and other threats from infiltrating your system and compromising sensitive information.
- Keep your firewall active. Ensure your device’s firewall is always running to block network intrusions.
- Secure your network. Use a strong WiFi password to keep hackers from easily guessing it and gaining access to your network.
- Enable multi-factor authentication. Activate multi-factor authentication methods on all your online accounts to stop hackers from infiltrating them and learning your information.
- Use a VPN. The top VPNs mask your IP address and encrypt your online activity, preventing hackers from knowing what you’re doing and who you are.
How to Change Your IP Address
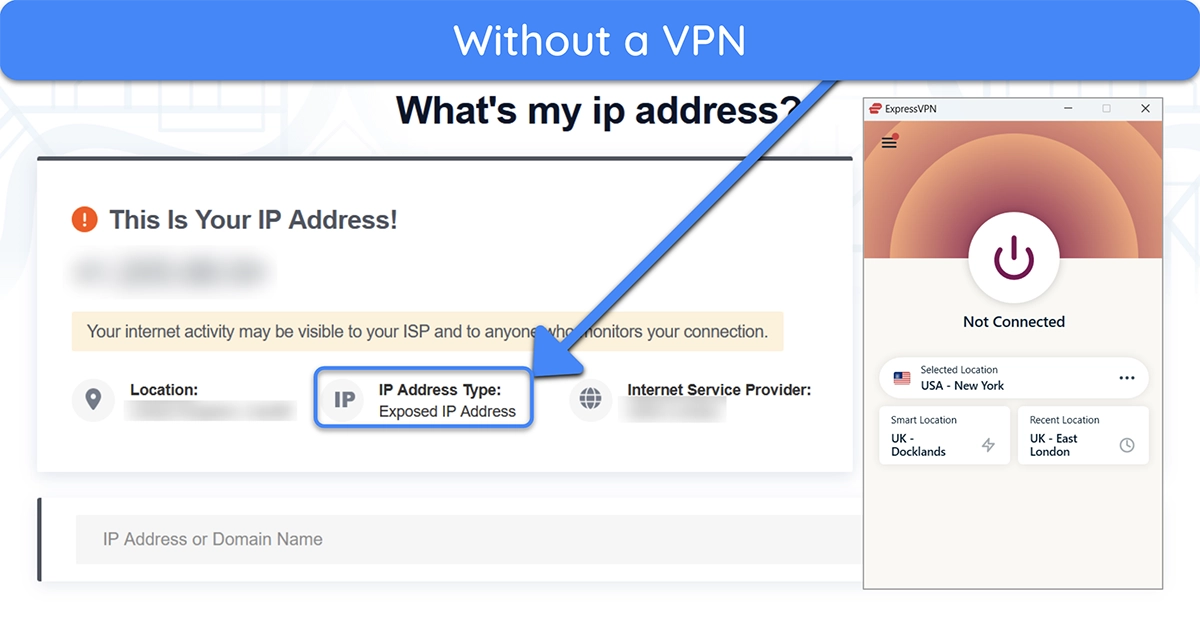
Using a VPN is the best way to change your IP address. VPNs also encrypt your traffic, adding an extra layer of security. If you don’t use a VPN, your IP address and location are visible to every site you visit. Plus, hackers spying on your traffic can see what you do online.
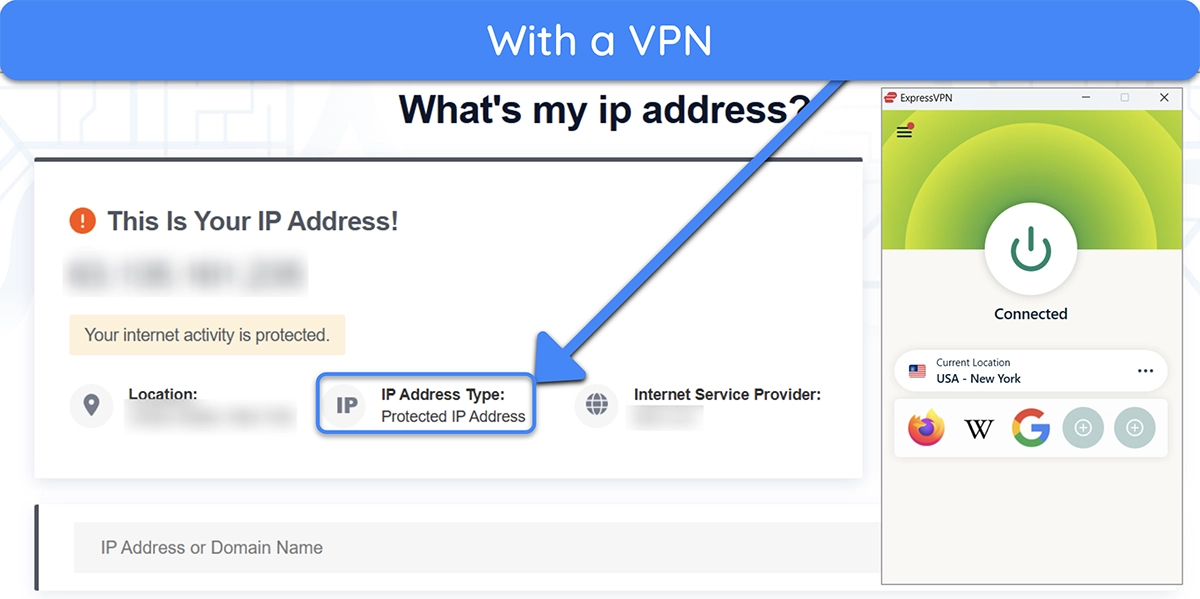
Changing your IP address with a VPN is easy. Simply download a top VPN and connect to your preferred server. Once connected, your IP address will be masked, and no one can spy on your activity, as all traffic will be encrypted.
You can try this yourself by checking your IP address with and without a VPN connection. You’ll see that your location and IP address both change after connecting to a VPN, meaning your original details aren’t revealed over the internet.
FAQs on IP Addresses
What are IP addresses used for?
Can someone trace my IP address?
What happens if someone gets my IP address?
There can be various security concerns if someone gets your IP address. Some of these include the following:
- Location tracking. Hackers could trace your location using your IP address.
- Network disruption. If attackers have your IP, they can attack your network with DDoS attacks and potentially crash it.
- IP misuse. Third parties could spoof your IP address and engage in illegal activities like downloading copyrighted files, which would be traced back to you.
Can I change my IP address?
IP address vs MAC address — what’s the difference?
IP (Internet Protocol) addresses and MAC (Media Access Control) both identify devices on a network, but they work differently. IP addresses identify devices globally across the internet, while MAC addresses identify devices locally on a LAN (Local Area Network).
MAC addresses are 48 bits long and have 12 hexadecimal values, like 0F-B0-C1-54-D2-63. On the other hand, IP addresses are 32 bits (numerical values) or 128 bits (hexadecimal values), depending on whether you’re using IPv4 or IPv6.
Bottom Line
Your IP address is a vital part of connecting to the internet. However, it’s also a potential gateway for those who want to track your online activity or gain access to your personal information. So, keeping your IP address private is crucial to reduce the risk of being targeted by hackers or other malicious third parties.






Leave a Comment
Cancel