RISK: Is This Your Webcam? You’re Being Watched
Wizcase has uncovered a significant amount of private web-connected cameras worldwide that are readily accessible to the general public. From these exposed webcams, a plethora of identifying and compromising information and media can be gathered at any time by cyber criminals.
What’s Going On?
Our white hat hacktivist, Avishai Efrat, found over 15,000 potentially accessible webcams, many located inside people’s homes.
Not only do they all potentially have the ability to be viewed by anyone around the globe with an internet connection, many of them can be manipulated, including by editing settings and other privileges. There are also quite a few webcams that have only easily predictable and standard default credentials to bypass to obtain admin-level access.
The device types we found include, among others:
- AXIS net cameras
- Cisco Linksys webcam
- IP Camera Logo Server
- IP WebCam
- IQ Invision web camera
- Mega-Pixel IP Camera
- Mobotix
- WebCamXP 5
- Yawcam
These devices seem to be prone to being accessed remotely if no additional security measures are taken after installation. There are many thousands of such devices exposed around the world.
Whose Data is Available?
Individuals and families, businesses, private institutions, places of worship, and more.
The most popular countries where these vulnerable devices are located:
- Argentina
- Australia
- Austria
- Brazil
- Canada
- France
- Germany
- Italy
- Japan
- Pakistan
- Russia
- Spain
- Switzerland
- UK
- USA
- Vietnam
Some examples of camera that were accessible include those at shops, inside the kitchens/living rooms/offices of private family homes – including a live feed of people on the phone and children peeking at the camera directly, tennis courts, storage units, hotels, museum security feeds, churches, mosques, parking lots, gyms, and more.
Can we know who, exactly, owns each device? It depends. From the technical information alone, it is difficult to pinpoint this information. However, using context from the videos, and also in the cases where we have admin access, we could find both user information and approximate the device’s geolocation based on various factors, and, more rarely, to whom it belongs.
can see children at home alone
With the information made available by these unsecured webcams, the potential impact includes:
- Unknown viewers or even people in their own houses indecently exposed and taking indecent pictures;
- Settings and admin credentials are available to be changed by anyone;
- Personally Identifying Information (PII) can provide the details needed for hackers to access bank accounts and steal identities;
- Criminals can better strategize their plan of attack;
- Illegal or morally questionable activities can be viewed by authorities;
- Government agencies have an additional window into the private lives of citizens they’re monitoring;
- Intergovernmental espionage;
- Modifying feeds so criminals can enter without being seen;
- Competitors have a window to the inside of stores and other businesses to better understand customer flow, preparations for special events, and the like;
- Hate groups are able to target and time their activities better;
- The lives of ordinary folks are on display for all to see.
Is it possible that the devices are intentionally broadcasting? We can only determine this for on certain webcams that we’re able to access the admin panel for. They’re not necessarily broadcasting, but some may be open in order to function properly with apps and GUIs (interfaces) for the users, for example. Also included with some measure of frequency are specifically designated security cameras at places of business, both open and closed to the public – which begs the question, just how much privacy can we realistically expect, even inside an allegedly secure building.
In almost every case, we know the device model, software version, etc. Depending on the camera type and version, it’s also possible to control the ones that we have admin access for – and for others, it’s even possible without. This varies from webcam to webcam – and even can allow an authorized person to control the camera angle or view.
How did it happen & how can it be prevented?
Initially, we might think that the only devices which should be exposed like this are routers, since they are the gateways connecting the different devices in each internal network to the internet (they are the ‘default gateways,’ in technical terms). Also, it’d be reasonable to expect web servers and APIs to be available, since they are meant to be reached publicly. Nonetheless, there are a few reasons why these are not the only cases …
The reasons are related to the fact the web cameras need to be accessed remotely – either by the users (e.g. from a mobile app) or by the manufacturer’s servers. The 2 network protocols which are commonly used to support these kinds of communication are port forwarding and P2P (peer to peer).
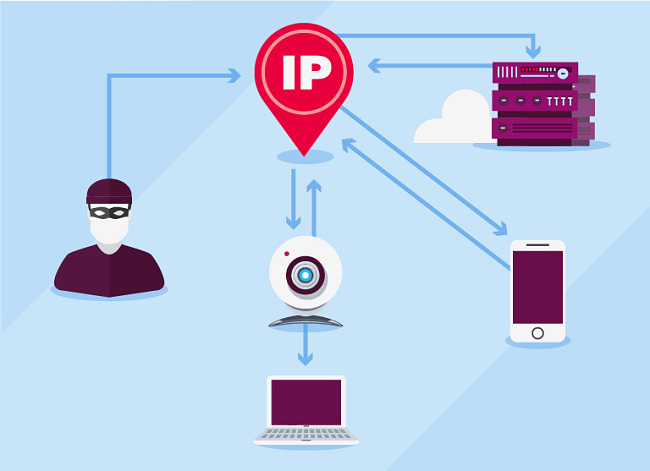
In basic terms, using port forwarding means making the camera accessible through your computer’s external IP (your router). This is usually done automatically using a set of network protocols called UPnP in order to avoid technical manual configurations. This is the step which basically makes the device accessible from the external network using a defined port on the external IP (a number which signifies a communication endpoint for a specific service for an IP, e.g. 10.10.10.10:1234) and it’s required in order for users to connect to the device remotely. Without further precautions such as password authentication and IP/MAC address whitelisting, this is insecure.
Some Internet of Things (IoT) devices and web cameras have Peer to Peer (P2P) networking enabled. In broad terms, this means that the device initiates communication directly to the provider’s servers for broadcasting, device data collection and controlling app to connect to the device. In other words, there’s no need to define port forwarding to control the app and open the device to the world since the communication is initiated independently with the device manufacturer’s servers. P2P is much easier to set up with a connected app, broadcast, or connect to a network without going into more technical configurations than manual port forwarding is.
Although this is potentially more secure than port forwarding, there are also a few problems here:
- This is only as secure as the manufacturer makes it. For example, P2P can still be used with UPnP enabled.
- P2P can cause large traffic on your network for “call home” traffic from the device which usually sends details about the device usage as well.
Web cameras manufacturers strive to use technologies which make the device installation as seamless as possible but this sometimes results in open ports with no authentication mechanism set up. Many devices aren’t put behind firewalls, VPNs, or whitelisted IP access – any of which would deny scanners and arbitrary connections. If these devices have open network services, then they could be exposed. The device’s security posture might depend on different things but a recommended way to set up a secure web camera would be to use a local VPN network, so that any open port would remain within the limits of the encrypted communication of the VPN. The app would connect to the VPN which would then access the port using an internal IP, thus avoiding the open port & call home potential problems and removing accessible ports from your external IP. Moreover, a unique password should be set up for the device.
Even when servers & devices are intentionally made public, the data available about them should be reduced to the minimum necessary in order to not be used for exploits.
Tools like shodan.io, censys.io, and others scan the internet’s devices with public addresses. They perform banner grabbing, which isn’t only checking whether or not the device is up, but also what available services it has (represented by the different ports), the operation system, and more. This kind of information can also be scanned manually, but these online tools are like giant scanners – they constantly go over available IP addresses and map them into a database.
The best way to prevent your webcam or other at-home IoT devices from being exposed is to change the default configuration to settings that make it more difficult to be discovered and accessed.
- Whitelist specific IP & MAC addresses to access the web camera – this should filter only authorized devices to connect to it;
- Add password authentication and change the default password;
- Configure a home VPN network so you will connect to it when you connect to the web camera remotely, and so the device will be only accessible within the VPN;
- Research web cameras made with security in mind;
- Make sure that UPnP is disabled on your web camera if you are using P2P.
If a user isn’t a tech savvy person, they might want to consult with someone who can assist. If you are, you can search your device’s external IP via online scanners, such as Shodan.io, in order to understand if you are exposed.
Manufacturers are also morally responsible for ensuring the safety of their products and should include stronger, individualized default security settings for each device that they sell.
Who is Wizcase? Why should I trust you?
Wizcase is the international favorite source for security news and real VPN reviews and tutorials. I lead a security research team comprised of skilled white hat hackers. They discover significant data breaches worldwide and promptly disclose these findings to both companies and the public, ultimately contributing to a safer and more secure digital experience for everyone.










Leave a Comment
Cancel