Ultimate Guide to I2p – How it differs from Tor/VPN + Setup Guide
If you have an interest in online privacy and security, then you might already have an understanding of the Dark Web and Tor, but that is just a tip of the iceberg.
There are other networks that offer more anonymity, and currently one of the most proficient is I2P; though it is yet to grow to the popularity of Tor.
The following guide addresses everything you need to know about I2P and explains how to start using the network.
Table of Content:
- 1 What is I2P?
- 2 How I2P Works
- 3 Garlic Routings vs. Onion Routing
- 4 How is I2P Different from Tor?
- 5 Does I2P do the same as a VPN?
- 6 How to set up the I2P Network
- 7 Configuring your I2p Network
- 8 How to Use I2P
- 9 Final Word
Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
What is I2P?
The Invisible Internet Project is a network that focuses on anonymizing users and providing secure internal connections between them. I2P operates online but is obscured from view unless dedicated software is used.
I2P differs from Tor as, while the latter allows you to browse the Dark Web and the internet anonymously, I2P was developed as self-contained software for the darknet, with a completely different architecture.
How I2P Works
The I2P network can only be accessed using specific software and is written in Java. The network relies on P2P participation to work, creating connections between users, referred to as tunnels, the complexity of which helping to facilitate anonymity. Every device in the network acts as a router, and so I2P is a decentralized network.
When data is sent over I2P, it is encrypted within layers end-to-end between the source and destination and is transferred via various tunnels. None of the nodes utilized can observe any data, and only the destination node can decrypt the final layer to receive the content.
What this means is that it’s difficult, or impossible, for any third-party to observe the complete circuit to determine either the source or the destination; which is referred to as Garlic Routing.
Garlic Routings vs. Onion Routing

Onion Routing
Tor network encrypts data in layers, with all data encoded in as many layers as nodes it passes through. It’s easier to grasp if you imagine a five-part circuit; the client, the Guard Node, the Middle Node, the Exit Node, and the destination.
Each exchange adds a layer of encryption except between the exit node and destination when it is unencrypted. In actuality, there can be hundreds of nodes, and therefore layers of encryption, and the destination can only ever discern the exit node.
However, it’s easy for organizations, like the NSA, to set up honeypot exit nodes to monitor traffic. A technique that measures the time taken for any computer operation to be executed in order to trace a source, known as end-end timing attacks, reveals the susceptibility of Tor.
Garlic Routing
As I2P, along with others like Freenet, has been developed specifically for purpose as a darknet, it offers more anonymity than Tor, with a method of routing that ensures maximum anonymity.
Rather than encrypt a single data packet, Garlic Routing involves grouping and encrypting multiple packets simultaneously. Each of the packets is usually independent and does not affect the state of others, with singular delivery instructions, and it breaks off upon reaching the correct destination. Tracking a single packet is more difficult than tracking a single computer in a network.
How is I2P Different from Tor?
The software differs entirely in how they operate, as well as what they offer.
- Onion Routing vs. Garlic Routing
- Tor is based on a central directory, while I2P is decentralized and relies on network users to store available content on their systems and to share P2P.
- Tor traffic is bi-directional; the nodes used for outgoing traffic are the same used for incoming traffic. With I2P, traffic is uni-directional, so traffic uses different tunnels every time, which improves anonymity, privacy, and security.
- While Tor uses SOCKS, I2P uses its API protocol, and is, therefore, more secure.
- Tor offers both internet and darknet connectivity. I2P, on the other hand, was developed specifically for the darknet, and it provides limited options for connectivity to the internet.
Does I2P do the same as a VPN?
I2P and a VPN share some similarities, but both are different and can be used together for maximum privacy and security.
How a VPN Works

Unlike I2P and Tor, the level of privacy with a VPN depends on the service provider. To achieve maximum privacy, you need to use a premium VPN service with sophisticated protocols, adheres to a zero logs policy, and is based somewhere outside of government jurisdiction.
If based in a country like the US, the law requires some user or connectivity logs.
The VPN service that you can trust with maximum privacy and anonymity is ExpressVPN, which is based in the British Virgin Islands, and does not keep any logs.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
I2P vs. VPN
While I2P offers anonymous access to the dark web, a VPN focuses on providing security and privacy on the internet.
Combining I2P or Tor with a VPN can ensure maximum security and absolute anonymity, though it will have a considerable impact on connection speeds.
Nevertheless, solely using a reliable VPN like ExpressVPN can still be sufficient for security, and providing other benefits.
- Obscuring online activity
- Securing public hotspots
- Circumventing geo-restrictions
- Streaming on Netflix, Hulu, BBC iPlayer, Spotify, etc.
- Safer P2P and torrenting
- Evading censorship in countries like Iran and China
- Avoiding bandwidth throttling
How to set up the I2P Network
The first thing you have to do is install Java if you haven’t already. The software can be downloaded from the official Java website.
Next, you need to download and install the I2P software, which is available for the following platforms.
- Windows
- Mac OS X
- GNU/ Linus/ BSD/ Solaris
- Debian/ Ubuntu
- Android
Significantly, there is no current iOS-compatible version of I2P.
This tutorial is focused on Windows 10, which is the most popular desktop operating system.
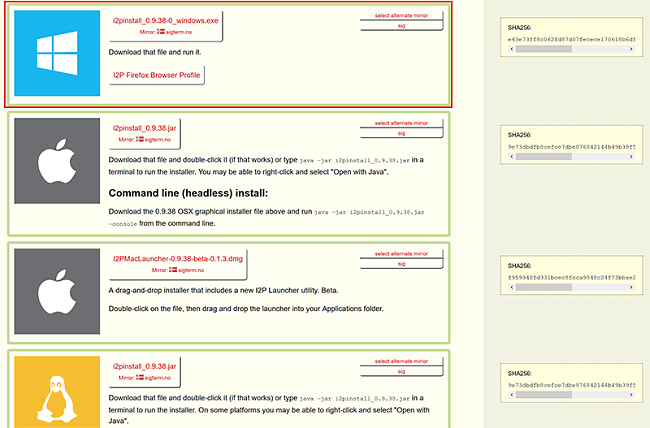
- Visit I2P site and download installation package and run it.
![I2p network setup]()
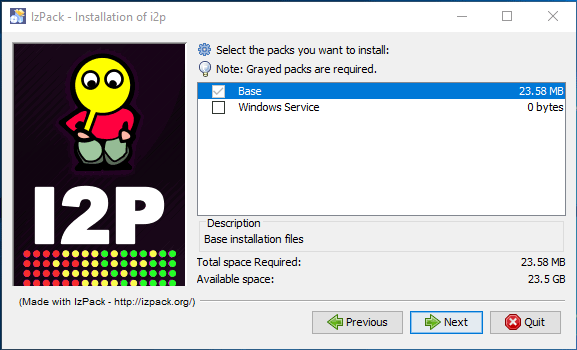
- During the installation of I2P, you’ll be required to establish some setting preferences. If you wish to have I2P running from Windows startup, you can tick the “Windows Service” box. Otherwise, leave it unselected and click “Next” to allow the default settings to complete the installation. Make sure you allow the creation of a shortcut on the start menu.
![I2p network packs install]()
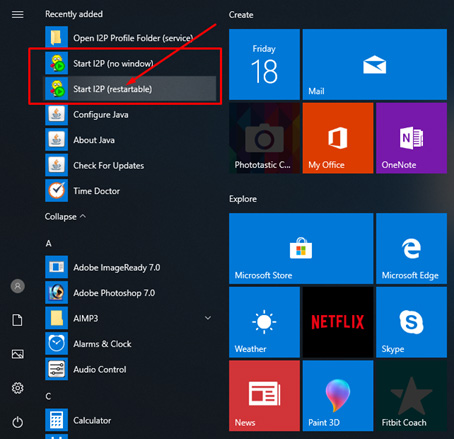
- Once the installation is complete, click “Done.” You should now see the start I2P option on the Start menu.
![I2P option on the Start menu]()
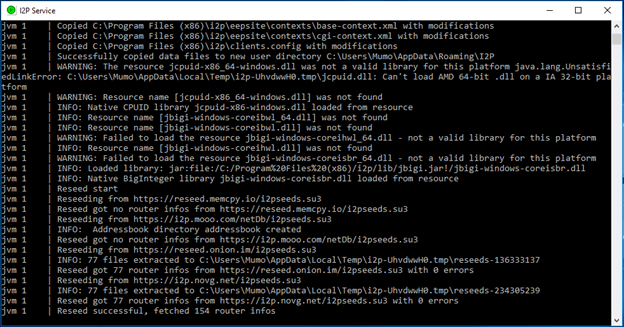
- After starting I2P, a console window will open; do not close it. If you need assistance, you can copy and paste log files from here.
![starting I2P console window]()
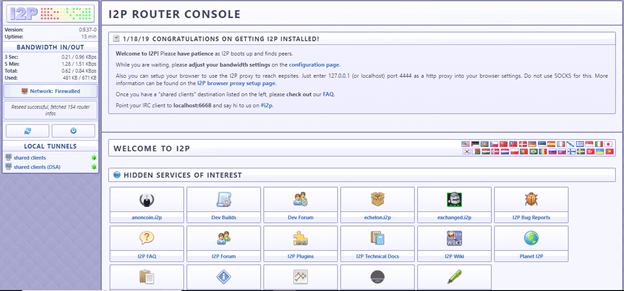
- I2P will open a new window on your default internet browser. This browser will act as your dashboard, and it will also show you when you get connected.
![I2P dashboard]()
Configuring your I2p Network
We recommend Mozilla Firefox in conjunction with I2P, as it is more secure than Internet Explorer, and more private than Google Chrome, due to their extensive prying.
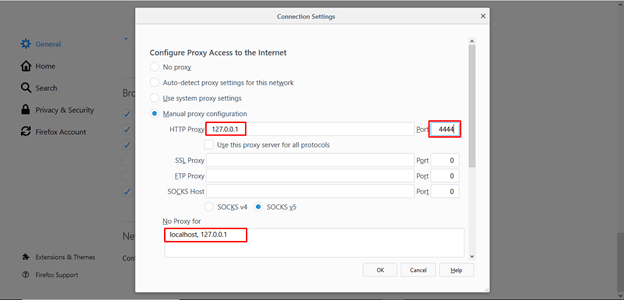
- Run Firefox and click “Options.”
- Scroll down to the Network Settings category and click “Settings.”
- Check the “Manual proxy configuration” box, and enter the following values: HTTP Proxy: 127.0.0.1, Port: 4444, and leave the No proxy box as “localhost, 127.0.0.1.”
![I2P manual proxy configuration]()
- Click “OK” to exit settings and you are done!
- If you’d like to use I2P frequently, it’s recommended that you install the FoxyProxy extension on your browser, as this will help you change proxy settings quickly.
- You should now be connected to the I2P network.
![I2P dashboard done]()
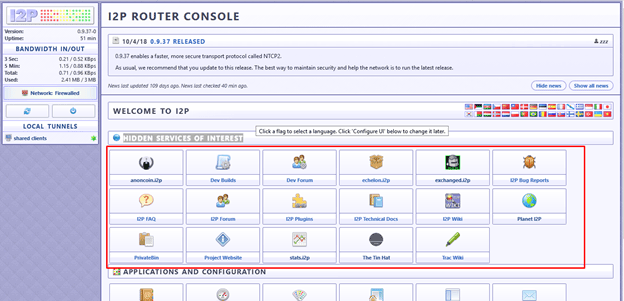
You can check your connectivity by clicking one of the listed “Hidden Services of Interest” in the router console. If one doesn’t work, you can try another.
![I2p network setup done]()
How to Use I2P
If you’re new to the technology, you won’t be aware of all of the benefits of the network. Below are some of the primary services you can use with I2P.
1Email / Messaging
I2P has a mail service known as I2P Bote, which is a fully decentralized and distributed anonymous email system which keeps you secure and anonymous. All email is encrypted, and no one will be able to intercept them.
Susimail is an available web-based email service, run and hosted by an individual known as Postman. It’s an excellent service for privacy and security.
2Eepsites
The titles assigned to websites within the I2P network typically carry the .i2p extension. Accessible solely within I2P, these websites collectively constitute the I2P darknet.
Some specific eepsites can only be accessed when the owner is online, which is the main drawback of a distributed network.
3Torrents
I2P offers the capacity to torrent safely, and they highly encourage it, and you can access I2P’s inbuilt Torrent client, called I2PSnark, from the router console.
You can install an I2P add-on on Vuze to facilitate anonymous torrenting over the internet.
4IRC (Internet Relay Chart)
Once familiar with I2P, you can also try accessing IRC, which has I2P chat rooms. You will, however, require to have a client already installed on your system, and you can check out its documentation here.
Final Word
I2P offers you connectivity to a whole new level of the internet that is hidden to regular internet users. Just like its name suggests (Invisible Internet Project), it’s aim is to offer users privacy and security, especially at this day and age when ISPs, governments, and other organizations, are monitoring how people use the internet.
To obscure your activities, you will have to use I2P, Tor, or a reliable VPN. The latter is the easiest, and though you will have to part with a few bucks, a VPN like ExpressVPN will offer you excellent security.




Leave a Comment
Cancel