The Ultimate Guide to Online Privacy for Journalists
As a journalist, you likely spend a lot of time online doing research. With ever-increasing rates of cybercrime, the dangers you face in the digital world are innumerable. Without the proper protection from online threats, you risk hackers stealing confidential information, exposing your personal details and that of your sources, breaking anonymity, and getting hold of your unpublished stories. You’d be a prime victim for blackmail—or worse.

Some of these events can even be extreme and life-threatening. According to UNESCO, over 1,700 journalists have been killed since 1993. A large portion of these journalists have been murdered in non-conflict zones rather than within conflict zones.
Being based in a non-conflict zone no longer assures your safety like it used to. Working online from behind a screen can’t guarantee you’ll be protected either. Out of all the journalists killed since 2018, those working in online media make up a significant 21% of deaths.
As the journalism industry continues to move from print to digital platforms, it’s imperative to your well-being—and that of your colleagues and sources—that you put the appropriate online privacy safeguards in place.
Securing your software and hardware with the right encryption tools can help you keep your confidential files and sensitive information from falling into the wrong hands. It’s also vital to utilize privacy-enhancing software to protect your anonymity and that of all your contacts.
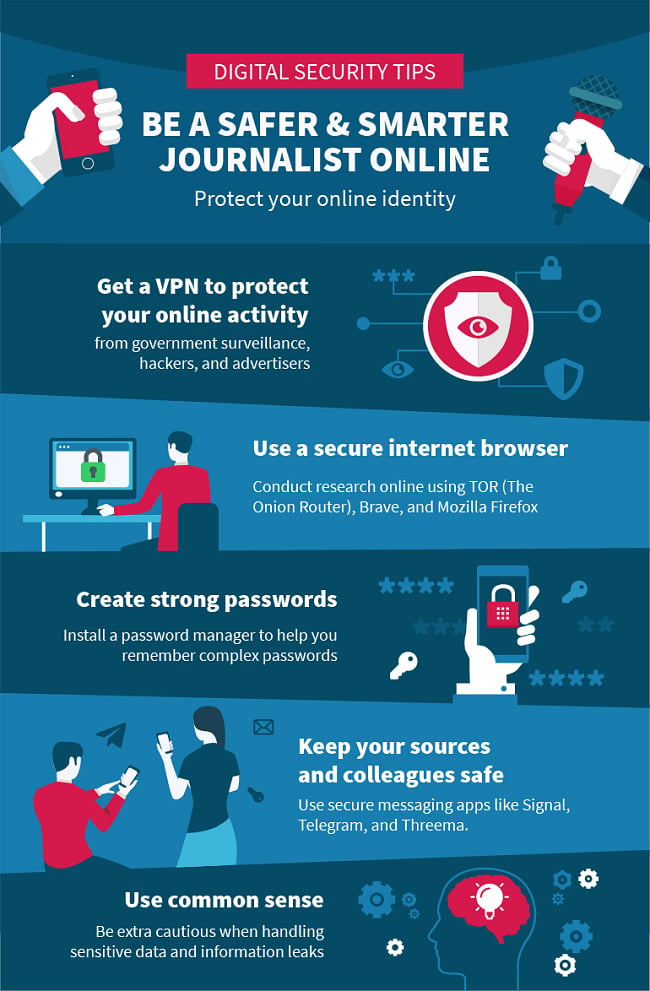
In this online privacy guide for journalists, I’ll outline the 12 ways you can protect your work, your sources, and yourself in 2024.
Quick Guide: 12 Ways to Protect Your Online Privacy as a Journalist
- Use Secure Apps to Send Messages to Sources: Ensure your messages have end-to-end encryption.
- Secure Your Emails to Protect Confidential Files: Prevent your emails being exposed in data breaches driven by hackers or the government.
- Encrypt All Your Devices: Protect your private information being intercepted by outsiders.
- Only Visit Websites with HTTPS in the Address: Choose this secure protocol that encrypts information sent between your web browser and a website.
- Protect Your Online Privacy With a Private Internet Browser: Use a browser that doesn’t track and store your browsing habits.
- Stay Anonymous Online with a VPN: Avoid exposing yourself and protect your online identity from prying third-parties, including the government, hackers, and spies.
- Use a Zero-Knowledge Cloud Provider: Upload confidential files only to trusted cloud providers.
- Create Strong Passwords: Use strong passwords that make it difficult for others to guess.
- Use Two-Factor Authentication (2FA): Add an extra layer of protection to your online accounts by requiring more than one piece of information to prove your identity.
- Watch out for Basic Online Dangers to Journalists: Be aware of common online dangers like phishing and tracking.
- Use an Alternative to Slack for Newsroom Communications: Secure your workplace communications.
- Educate Your Sources and Colleagues: Protect people you work with by sharing our online privacy guide for journalists.
Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
1. Use Secure Apps to Send Messages to Sources
Whenever you contact someone by text or voice call, there’s a chance your messages can be intercepted or that a third-party could listen in. By using a messaging app with strong encryption, you no longer need to worry about unwanted eavesdropping and exposing who you or your sources are.
Even though many messaging apps have basic encryption—and some even promise end-to-end encryption—you need to be careful which apps you choose. For example, WhatsApp claims to have end-to-end encryption, but its parent company Facebook has an extremely poor reputation for protecting its users’ privacy.
Thankfully, there are secure messaging apps available. These apps will ensure safe and private communication between you and your sources or colleagues.
3 Secure Messaging Apps You Can Use to Secure Your Communications
- Signal: Strong combination of end-to-end encryption and extremely limited logs. This was confirmed in a court case, when all the company could produce was the time of account creation and the last log on.
- Telegram: Provides encryption, self-destructing messages, and two-factor authentication.
- Threema: Threema doesn’t use your phone number but instead creates an anonymous ID for you. This is great for talking to someone whom you don’t want to give your number to.
All of the apps above offer end-to-end encryption and other security features, but Signal and Telegram require your phone number. While the number is hashed and anonymized, I recommend using a new number that isn’t linked to you to sign up.
2. Secure Your Email to Protect Confidential Files
Emails are likely one of your main points of communication. Unfortunately, major email providers still fail to provide standard encryption options. This means your emails can be intercepted and read, especially at the recipient’s end.
If you’re planning to send or receive potentially sensitive data, it’s best to sign up to a secure email service. Tutanota is one of the best options available as it encrypts everything—including the subject line, text, attachments, and even your address book. It has a free and paid version, with storage space ranging from 1GB to 1TB.
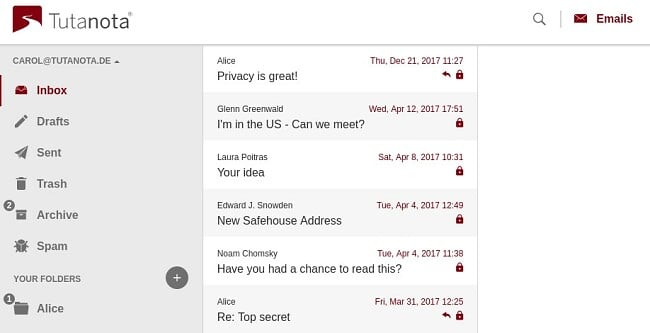
Tutanota has a free and paid version, with storage space ranging from 1GB to 1TB.
When emailing someone using a mainstream email provider, Tutanota will send them a message with a link to enter a password and unlock your message. This keeps your emails anonymous in all circumstances. I like Tutanota as it’s constantly being improved by developers and privacy experts, and includes a free mobile client.
Other popular email services like ProtonMail and Hushmail offer many of the same features. However, Tutanota is the only one to encrypt the entirety of an email.
3. Encrypt All Your Devices
You need to ensure that the devices you and your sources use are encrypted. This includes your computers, tablets, phones, and external hard drives.
3 Ways to Protect Sensitive Data on Your Devices
- Full-disk encryption (FDE): This is the most secure way to encrypt your device and is vital if you have unfinished reporting and other sensitive files on your harddrive. You can use BitLocker if you’re a Windows user or FileVault if you’re a macOS user. You can also use BitLocker to encrypt your external drives, such as USB drives and memory cards, on Windows while macOS users do this via Disk Utility. With these programs, your disk will only be accessible with a password or PIN.
- Encrypting specific files or folders: You can use open-source software, like VeraCrypt, to encrypt individual files and folders.
- Air gapping: This is a basic form of protection where you keep your device disconnected at all times. However, this method is only effective if your system is perpetually offline—which means no Bluetooth or NFC either.
4. Only Visit Websites with HTTPS in the Address
What’s the difference between HTTP and HTTPS? HTTP doesn’t encrypt data sent between your browser and a website — but HTTPS does. This is essential if you’re interacting with sensitive data, need to log in with private credentials, or are making financial transactions.
An easy way to check if you’re on a secure page is to look at the address bar. Is the site you’re on using “http://” or “https://”? You should also pay attention to the small padlock symbol to the left of the address bar. This can show you if a connection isn’t secure, even if you appear to be on an HTTPS page.

5. Protect Your Online Privacy with a Private Internet Browser
It’s no secret that many web browsers store your personal, private, and financial information. If you are reporting on a sensitive case, this data could be intercepted by hackers, the government, or other unwanted third-parties.
Don’t forget that it’s not just about securing your work, but ensuring you won’t be silenced in other ways. If you have particular online interests that you don’t want others knowing about, such as your porn viewing habits, these could be used against you as blackmail.
Using your browser’s private or incognito mode won’t ensure your privacy, as your ISP and other parties can still track what you’re doing. I recommend combining a private browser with a VPN, or using a more private browser.
Here are my recommended private browsers:
TOR (The Onion Router)
TOR is the most private option on this list. It was originally developed by the US Navy for anonymous communication.
TOR encrypts your data and “bounces” it randomly around the world via a network of volunteer relays. Additionally, all your requests are routed via HTTPS (a more secure protocol), no scripts are loaded (making you harder to track), and you’re permanently in incognito mode (so none of your browsing data is stored).
This way, you can research and communicate freely without worrying about being tracked, and even navigate the dark web.
Firefox
Run by the non-profit Mozilla organization, Firefox has an built-in tracker blocking and is monetized almost entirely by royalties from partnerships and distribution deals. This means none of your browsing data is sold to third-party companies to make money.
I highly recommend using the DuckDuckGo search engine, which doesn’t store any data or track your activities, with Firefox. While DuckDuckGo doesn’t present as many search results as Google, it’s still a much safer option for performing anonymous research.
You can also use Firefox’s “Containers” add-on to separate your browsing activity without having to clear your history, log in and out, or use multiple browsers.
Brave Browser
Brave is based on Chromium, the open-source code powering Chrome. However, aside from the core code, the two browsers are very different. Unlike Chrome, Brave automatically blocks cross-site trackers, adverts, and upgrades your connection to HTTPS. This helps you remain more anonymous online.
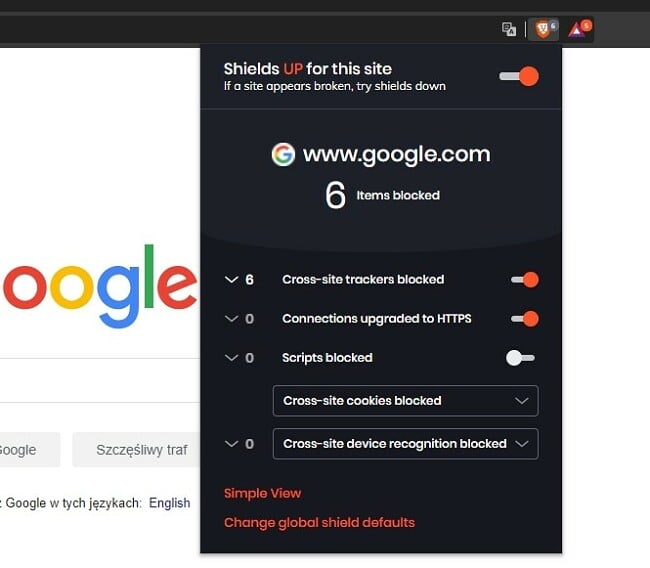
Warning! Avoid Chrome as Your Internet Browser
Google’s business model relies on collecting vast quantities of personal data and monetizing it. While this isn’t inherently dangerous, the data stored can be obtained by malicious third-parties or law enforcement officials. In fact, you should avoid all of Google’s services to avoid your data being leaked.
Instead, you should consider signing up to their Advanced Protection scheme. This adds more defenses and restrictions to your Google account and associated apps. It was specifically created by Google for journalists, activists, business leaders, and political campaign teams.
6. Stay Anonymous Online with a VPN
A VPN, or virtual private network, is a global network of servers that offer an anonymous and encrypted internet connection. The encryption hides all your online activities so that they’re unidentifiable and no one can trace them back to you.
A VPN is extremely useful if you’re reporting from countries where government surveillance is a threat. It helps you work under the radar of the country’s surveillance technology, keeping your traffic and online activities private.
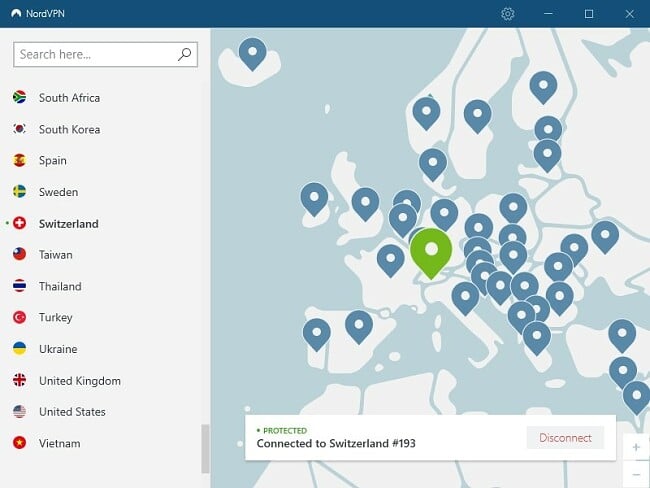
Before connecting to a VPN server, you should first check if the server is hosted in a country that is part of any intelligence-sharing alliances. These agreements may result in VPN providers being forced to hand over your online information to the government.
There are currently three significant alliances involving a total of 14 countries, with some potential third-party contributors.
- 5 Eyes — USA, UK, Canada, Australia, and New Zealand
- 9 Eyes — 5 Eyes Countries plus Denmark, France, The Netherlands, and Norway
- 14 Eyes — 9 Eyes Countries plus Germany, Belgium, Italy, Sweden, and Spain
- Potential 3rd-Party Contributors — Israel, Japan, Singapore, and South Korea
You should also be careful not to connect to servers in countries with potentially hostile governments. For instance, if you’re reporting on a sensitive issue in Russia, you could be targeted by Russian intelligence. If you connect to a server that is physically in Russia, it’s possible that the local authorities could be monitoring this server—and hence your online activities.
It’s especially important for journalists to get a VPN with a no-log policy. These providers will not store any information about your online activity. Highly recommended no-log VPNs for journalists are NordVPN, ExpressVPN, and Surfshark.
Don’t trust free VPNs! Free VPNs are not trustworthy enough for secure journalistic needs. To make profit, free VPNs are even known to sell user data and give network access to third parties. Make sure you thoroughly research any free services you use before entrusting them with your own valuable data.
For an in-depth look at how VPNs work, check out our complete beginner’s guide to VPNs.
7. Use a Zero-Knowledge Cloud Provider
You can use cloud services to send large files to your colleagues or sources. However, it’s important to make sure you use a zero-knowledge cloud provider—this ensures your files will be encrypted before they’re uploaded. A unique password will then be issued to your recipient so that they can decrypt the files.
Sync and pCloud are 2 zero-knowledge cloud services that provide secure end-to-end encryption, even with their free plans.
8. Create Strong Passwords
It’s extremely important to use strong passwords, especially for your email accounts. If a hacker gets access to your primary email account, they could quickly use the same password to break into more of your online accounts.
However, contrary to popular belief, a password with a random combination of uppercase and lowercase letters, numbers, and symbols isn’t the strongest option. It’s also not the easiest to remember.
How to Create a Strong Password
- Make a long password: Make sure it’s at least 11 characters long.
- Use random words: You could flick randomly through a dictionary until you have 4+ words and link them together.
- Ensure it’s easy to remember: Choose several words that have no connection but that you are able to remember.
- Use a unique password for each account: Don’t use the same password twice.
People use weak passwords because they can’t remember more complex — and therefore stronger — passwords.
Luckily, you can use a password manager to store your login credentials. You’ll only have to remember one “master password” that has the ability to unlock the whole vault. I recommend using KeePass, LastPass, or Dashlane—all of these password managers are secure and user-friendly, with free and paid plans available.
9. Use Two-Factor Authentication (2FA)
If you’re storing sensitive material on one or more of your online accounts, 2FA is vital.
2FA requires two types of authentication before giving you access to your online account. First, you enter your normal account login details. Then a randomized token is sent to your physical device and you use that to verify your identify.
The necessity for a physical device adds a strong extra layer of security. Even if someone gains access to your credentials, they will need this device to actually log in.
3 Ways to Set Up 2FA
- On your phone. For Android users, you can use andOTP or Google Authenticator. For iOS users, you can use OTP Auth or Yubico Authenticator. Authy is a good choice if you use both operating systems.
- Via a physical device like YubiKey or Google Titan. It needs to be physically plugged in or tapped against your phone (if NFC is supported) for verification.
- Via SMS or email. This is the least-secure method, but you should still set it up if it’s the only type of 2FA on offer.
While app-based 2FA is the easiest and most widely-supported method, physical 2FA is the safer choice.
10. Watch out for Basic Online Dangers to Journalists
There are some common online privacy and security threats that can cause major issues if you fall victim to them. Fortunately, they’re easy to avoid if you’re aware of them and follow our online privacy guide. Let’s take a closer look at a few of them.
Phishing
Phishing is a cyber attack that tricks victims into believing they are being contacted by a trusted company or service. These attacks cause you to expose yourself and compromise your online security.
Here’s an example: You’ve received an email, which looks like it’s from FedEx, asking you to verify something by clicking on a link. When you click the link and go to the ‘FedEx’ site, a hacker tracks your keystrokes and steals your login credentials. Even if you’re using 2FA and enter your code on the phishing website, hackers can use this information to immediately log in to your real account.
You can see an example of a phishing email below:

While it looks semi-official, you can see that it isn’t addressed to anyone in particular, and the formatting and punctuation are strange. However, the main red flag is the email address, which is clearly not related to FedEx.
You still need to be vigilant about what you open and click when receiving emails. Cyber attackers can still appear to use a company’s domain to impersonate a company or one of its employees.
If this were to happen with your Google account, the hacker would be able to gain access to everything you’ve stored on Google—including Gmail and Google Drive. It could also potentially give them access to your bank accounts and a variety of sensitive information.
Malware
Be careful of accidentally infecting your device with malware when browsing the internet. Journalists should be especially concerned about ransomware, which encrypts your whole hard drive and often requires you to pay a monetary ransom in exchange for regaining access to your files.
Make sure you use your common sense and avoid visiting potentially malicious websites. Don’t browse non-secure websites and avoid websites inundated with adverts, especially pop-ups. Bookmark sites you regularly return to so you know you’re visiting the real version.
You can use Malwarebyte’s anti-malware software to regularly scan your computer for threats. The free version is enough to detect malware, but the premium version offers useful extras, including ransomware protection and real-time protection.
You should also be aware of “malvertising”, which quietly deliver malware via adverts without you even realizing it. Use an adblocker such as uBlock Origin on Chrome or Firefox to protect yourself against this threat.
Keep Your Devices Updated
Keeping your devices updated ensures you’ll be protected from the latest security threats. This advice applies to the operating system on your laptop or computer, mobile devices, and programs or apps you use.
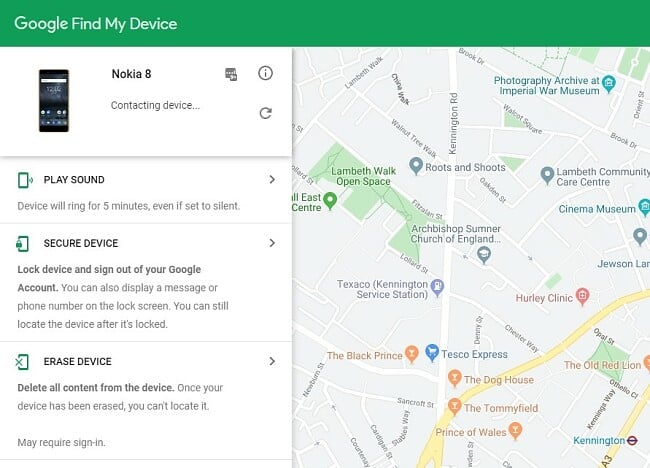
Lock Your Devices and Set up Tracking
Make sure you have some form of lock on your mobile device and computer. Passwords are more secure than fingerprints or facial unlocking.
In case you ever need to recover a lost device, you can set up device tracking on Android and iOS devices. You can also activate the option to remotely wipe your devices, in the event that the confidential information contained on it falls into the hands of unauthorized third parties.
11. Use an Alternative to Slack for Newsroom Communications
Instant messengers and collaborative tools, such as Slack and Skype for Business, have made their way into workplaces around the world. As journalists, you may be sending sensitive data and files to your colleagues via these channels. You need to make sure they can’t be accessed by unauthorized third parties.
Slack is one of the most widely-used collaboration tools, thanks to its user-friendliness. However, Slack does not employ security features such as end-to-end encryption or self-destructing messages.
4 More Secure Options for Newsroom Communications
- Keybase Teams: Similar to Slack, but with end-to-end encryption and a self-destruct feature that completely removes messages from the conversation.
- Element: Built on the open-source Matrix protocol, Element offers the best implementation of end-to-end encryption plus a user-friendly interface.
- Wickr: Includes end-to-end encryption, auto-deletion of messages, and forensic deleting of content from your device.
- Semaphor: A zero-knowledge messenger protected with end-to-end encryption and blockchain technology.
12. Educate Your Sources and Colleagues
The average person doesn’t know how to share confidential information in a secure way—and this includes your sources.
It’s important that you show your contacts how they can protect any confidential files and communicate privately with encrypted messages and emails. Even if they already know, it’s in both of your best interests to discuss a standard operating procedure (SOP) before cooperating.
Explain to them that under no circumstances should they deviate from your SOP. It’s best to meet in person to avoid leaving any digital footprints — even if it’s just to set up their online privacy safeguards.
Keep in mind, even when your online security measures are robust, you could still face vulnerability if your data is exposed by others. Your online privacy and security is only as strong as those in your circle of communication.
Aside from helping to ensure you don’t expose yourself, a guide to online privacy like this one can equip your colleagues with the tools that they need to stay safe online.
Lazy Security Exposes Journalists — Protect Your Online Privacy and Safety Now
Every journalist needs to protect themselves online with strong security and privacy tools—from hackers, state-sponsored operatives, and others who actively work to prevent damning stories from being published.
Some of the fastest and easiest ways to secure your digital presence immediately include using a secure internet browser with a VPN as well as creating strong passwords to protect your device’s online accounts.
It’s also important to use common sense—like not clicking on links in emails from unknown senders—to avoid common cyberattacks.
Attention: WizCase owns the visual and written content on this site. If our cybersecurity insights resonate with you and you wish to share our content or visuals, we ask that you credit WizCase with a link to the source in recognition of our copyrights and the diligent work of our expert cybersecurity researchers.




Leave a Comment
Cancel