Beginner’s Guide to Tor: What It Is and How to Safely Use It 2025
The Tor Browser is the best tool to access the dark web, but it’s not without its shortcomings. Tor alone doesn’t protect all of your data from leaking and renders it vulnerable to surveillance. Compromised Tor exit nodes reveal user traffic to operators mostly known to trace Tor users’ identities. To protect myself, I needed true end-to-end security.
A VPN is the only tool that fully encrypts your data while it passes through the Tor network. This complete guide reveals all the important details about Tor and how to use it with a VPN for the highest level of security.
After putting 30+ VPNs through rigorous testing, ExpressVPN topped the list. ExpressVPN’s audited TrustedServer technology doesn’t store any data, ensuring users stay anonymous. You can even use ExpressVPN with Tor risk-free — it’s backed by a 30*-day money-back guarantee. If you’re not satisfied, you can request a refund. Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Stay safe on Tor with ExpressVPN
Note: Tor isn’t legal in every country, so please check your local laws. My team and I don’t condone participation in any illegal activities.
What Is the Tor Browser? (Also Known as The Onion Router)
Tor, short for “The Onion Router,” is a free browser that allows users to anonymously access the dark web. It looks just like a normal browser, but it routes your traffic through various servers located all over the globe. Your traffic is wrapped in layers upon layers of encryption (like an onion).
When using Tor, your information goes through a three-stage procedure that includes an entry node, middle node, and exit node. At first, your information gets encrypted. As it moves through a random set of nodes, a layer of encryption is gradually removed, exposing the route to the next node. The goal is for none of these nodes to have the capacity to view the entire relay, encompassing both the content of the request and the requester’s identity. This guarantees that your information stays unidentified throughout the entire process.
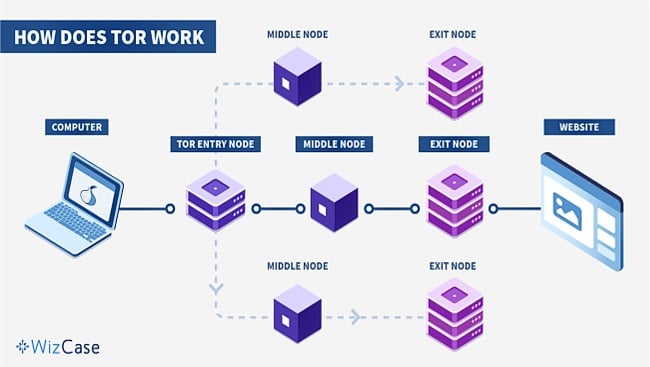
Tor’s core purpose is clear: defend internet users from tracking, surveillance, and censorship. It provides easy access to private communication and information to:
- Everyday people who want to ensure that their internet activities stay free from third-party access.
- Journalists looking to maintain the anonymity of their sources.
- Activists who need to protect themselves on the job.
- Whistleblowers who need to share sensitive information without endangering their life and/or livelihood.
- Law enforcement agents conducting intelligence gathering and monitoring.
- Security engineers and IT professionals performing security tests.
- Citizens of high-censorship countries who want access to the free web.
In the realm of Tor data flow, it’s important to acknowledge two weak spots: the entry and exit nodes. The entry node possesses knowledge of your true IP address, while the exit node holds insight into your unencrypted requests. It is only when both are compromised that your whereabouts, identity, or intended website can be exposed. Unfortunately, these nodes can be susceptible to manipulation by malicious entities, jeopardizing the security of the entire setup.
The easiest way to protect yourself is to use a trusted VPN to disguise your actual IP address while on Tor. After testing more than 30 VPNs, I can attest to the security features employed by ExpressVPN. I ran 40+ servers through extensive leak tests, and ExpressVPN never revealed my actual IP address. Don’t take my word for it — test ExpressVPN with Tor yourself. It’s backed by a reliable 30*-day money-back guarantee, so you can claim a refund if you decide it’s not for you.
Is Tor Actually Safe to Use?
While Tor is effective at keeping users’ identities anonymous, it is not fully secure. If you’re using Tor, you should make note of the following vulnerabilities (and take the necessary precautions):
- Surveillance related to Tor use. Some agencies, like the NSA, are known to pay extra attention to traffic coming from Tor users.
- Fake Tor websites. Some hackers set up fake mirror copies of the Tor website. Users that download the Tor bundle from one of these fake sites get a malware-infested version of the browser.
- Unsecured device traffic. Tor only protects the traffic coming to and from the browser, not all traffic coming from your device. iOS users should especially beware: iOS requires all browsers to use WebKit, which impairs the Onion Browser’s (Tor’s native Android and iOS apps) capability to keep you anonymous.
- Compromised exit nodes. All information transferred in an unencrypted protocol (e.g., HTTP, SMTP) can be seen by Tor exit node operators. What they can see, they can theoretically use: some malicious exit node operators spy on people’s traffic and session cookies in order to steal passwords and other personal information. The most common case of exit node compromise is when an attacker detected traffic headed for cryptocurrency sites and switched the addresses to one of their own. Users unwittingly sent these hackers cryptocurrency, resulting in massive losses.
- Bad threat actors are known to operate entry and middle nodes. Since 2017, a researcher from Columbia University has been able to trace Tor users’ identities with 81.4% accuracy, according to a Vice report. One high-level bad actor also known as KAX17 owns a total of around 900 servers. In a study quoted in The Record, “there was a 16% chance that a Tor user would connect to the Tor network through one of KAX17’s servers, a 35% chance they would pass through one of its middle relays, and up to 5% chance to exit through one.” Anyone with enough resources can make a business out of intercepting Tor user traffic.
- User oversight. Users sometimes misuse the Tor browser by installing unauthorized add-ons, leaving Javascript enabled, or torrenting. Worse, some users use Tor to access accounts tied to their real-life identities, or post personal information on websites and forums.
However, the biggest threat are the users themselves, as many don’t understand that Tor isn’t a silver bullet. The good news is a trusted VPN like ExpressVPN hides your Tor usage from your internet service provider, and your IP address from Tor’s entry node.
What’s Better: Tor or VPN?
Tor is designed to keep users anonymous while a VPN keeps user information private. In a nutshell: if you don’t want anyone to know who you are, use Tor. If you don’t want anyone to know what you’re doing online, use a premium VPN. Let’s dive deep into the details.
The Tor Browser is a free, downloadable software that looks and functions like a typical browser. There are several reasons why you’d want to use Tor instead of a VPN:
- You need access to dark web sites (also known as .onion sites).
- You prefer your set-up to be 100% trustless and are knowledgeable about, or willing to do the research involved in Tor installation, configuration, and safety best practices.
- You’re not planning on accessing accounts and platforms tied to your real-life identity.
- You don’t mind slow loading times.
- You have the tools and the knowledge required to detect and avoid malware, phishing, and scams rampant in the dark web.
- You are not planning to use Tor while torrenting.
- You understand and accept the risks involved in Tor use and are willing to take full responsibility should anything go wrong.
A VPN is a separate software that hides your identity by routing your traffic through its global server network. There are several reasons why you’d want to use a VPN instead of Tor:
- You want to access websites and apps that are tied to your real-life identity, but you want to do so privately and securely, even from an unsecured WiFi hotspot.
- You want an intuitive, easy-to-install app that you can use on any device.
- You don’t need to access dark web sites.
- You value accountability: you’re willing to trust another entity to protect your privacy, as long as they are reputable, audited, and have demonstrated a clear history of protecting user privacy even in situations involving law enforcement.
- If there’s any issue, you’d like the assurance that a company is there to help you resolve it.
- You need unimpeded access to clear websites.
- You don’t want slow speeds to downgrade your user experience. ExpressVPN has the fastest speeds out of any VPN in this article — fast enough to browse the internet without interruptions and even stream video in 4k.
- You’re looking for a tool to help you torrent safely without exposing yourself to malware, hackers, and trackers.
Technically, you can also be anonymous while using a VPN, especially if you choose a VPN with a cryptocurrency payment option. While you might be tempted to do so, it’s not recommended to use a free VPN, especially if your priority is anonymity. Most free VPNs don’t have the capability to protect your data while on Tor.
Even if your particular use case requires Tor, a VPN can help protect you from compromised nodes and other Tor-associated risks. There are 2 ways to use a VPN with Tor.
Tor Over VPN
The safest way is to connect to a VPN and then launch Tor. Tor over VPN adds another layer of encryption to your entire traffic, and prevents Tor’s entry node from seeing your real IP address. This protects you from any deanonymizing attacks from a compromised entry or middle node. On the other hand, you’ll still be vulnerable to SSL attacks and other phishing scams from compromised exit nodes, so you have to be on guard.
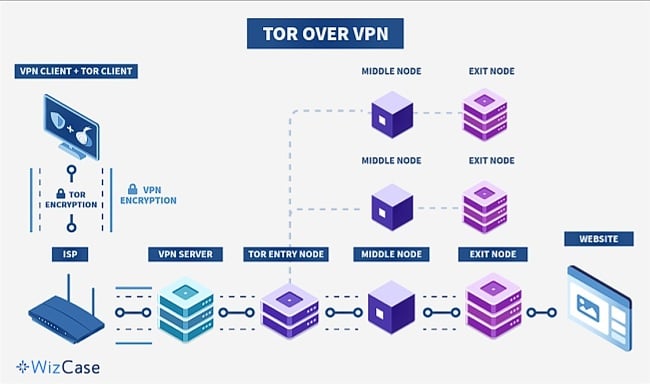
Since your data is protected by the VPN, your ISP or any other third-party who might be surveilling your internet traffic won’t know that you’re using Tor. However, as your traffic passes through the exit node, you’ll be getting a Tor IP address, so websites can see that you’re a Tor user. Some clear web websites (e.g., banking websites, Airbnb, Doordash, Apple) might block you because of this.
The Tor over VPN setup is private, but it’s not fully anonymous since your VPN provider knows your actual IP address (maybe even your name and address, through your payment method). You can subscribe to a VPN to minimize the information that you give to your VPN provider, but keep in mind that you might not be eligible for any money-back guarantees.
The security level you receive relies on the VPN you select. If your internet connection suddenly disconnects and your VPN lacks a kill switch, data may inadvertently leak to Tor nodes. This could pose a risk, especially if you’re connected to a harmful exit node. Additionally, employing an ineffective VPN can further slow your internet due to Tor’s inherent connection slowdown.
To reap the security benefits of a Tor over VPN setup, you need a high-speed VPN with a verified no-logs policy. One good example is ExpressVPN — its no-logs policy is both third-party audited and has been tested in real-life settings. It’s backed by a 30*-day money-back guarantee so you can test ExpressVPN with Tor risk-free. If you decide it’s not for you, you can easily claim a refund.
VPN Over Tor
You can also connect to Tor and then to your VPN. VPN over Tor is more complicated than Tor over VPN because you first need to find a good VPN that supports Tor connections and OpenVPN, and then manually configure that VPN for use.
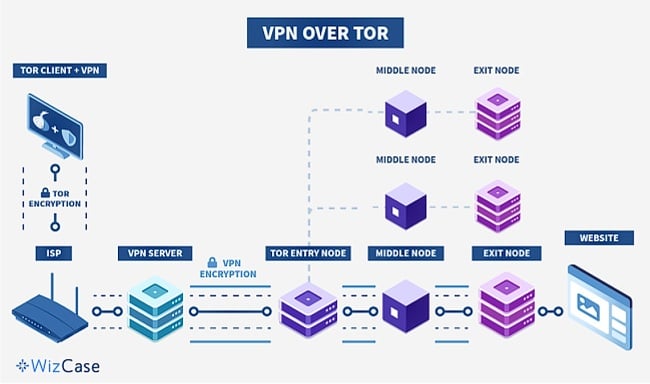
Connecting to a VPN while using Tor allows you to visit sites on the clear web that normally block Tor addresses. This approach will also hide your browsing activity from the exit node. However, you cannot access “.onion” sites on a VPN over Tor setup. Connecting to Tor before a VPN also means that your ISP can see that you’re connecting to Tor.
Tor’s entry node will also be able to see your actual IP address, and, while your VPN might only see a Tor IP, it will know that you are using Tor. To prevent this, you’ll need to choose a reputable VPN with a strong no-logs policy. This is especially tricky since only a handful of VPNs support the VPN over Tor setup. Since the VPN over Tor setup is more complicated (and thus more prone to mistakes that can actually reveal your IP address), I recommend using it only when necessary.
If the VPN over Tor setup is required for your particular use case, PrivateVPN is one of the few reputable VPNs that support connections from Tor servers. The PrivateVPN website has a detailed guide on how to set up VPN over Tor through OpenVPN and every subscription is backed by a 30-day money-back guarantee. This way, you don’t have to worry about losing money if you end up changing your mind.
The Best VPNs for Tor — Tested in 2025
1. ExpressVPN — Audited TrustServers Enforce No-Logs Policy for Close-to-Anonymous Tor Use
Key Features:
- 3,300+ servers in 105 countries to access Tor safely from anywhere
- TrustedServers ensure that user data is wiped after every shutdown
- Simultaneously connects up to 8 devices so you can access Tor from any device
- Audited no-logs policy guarantees 100% anonymity, AES-258 encryption and leak protection ensures full privacy while on Tor
- 30*-day money-back guarantee so you can try it with Tor for yourself, risk-free
ExpressVPN’s entire server network is secured with TrustedServer technology — it runs only on random access memory (RAM), so no data is ever written onto a hard drive. This means no data that passes through the company’s servers is vulnerable to theft, hacking, or government seizure. ExpressVPN’s privacy policies are even audited by an authoritative third party, PricewaterhouseCoopers (PWC), ensuring its no-logs policy is legitimate.
My tests also showed that ExpressVPN’s speeds are consistently fast, which is important since Tor connections tend to be pretty slow. I could access Tor securely, without any significant decline in connection speed.
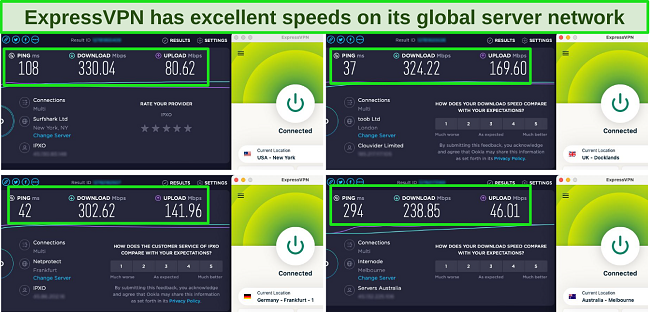
Even when my connection was unstable, I felt safer knowing that I was protected by Network Lock, ExpressVPN’s kill switch. This is designed to keep your IP address private even if the VPN or internet connection drops. It does this by blocking all internet traffic until the VPN connection is re-established.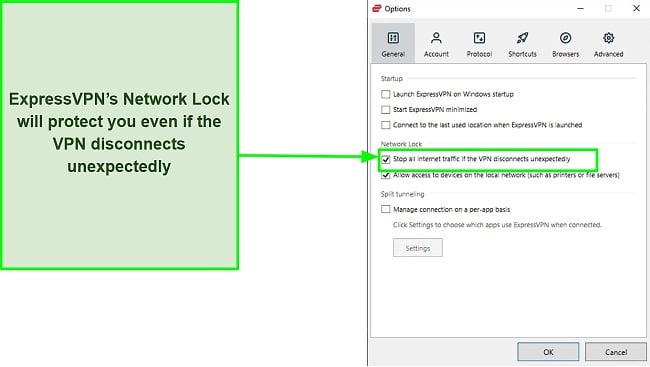
Tor users can access the ExpressVPN .onion site for complete privacy starting from set-up. It’s possible to download ExpressVPN through its dedicated Tor site, making it the perfect choice for those who might be living in high-censorship jurisdictions. The dedicated .onion service also makes all the practical information on the ExpressVPN site available over Tor.
ExpressVPN is based in the British Virgin Islands, which is known for its strict, no-data retention laws, and for being free from international intelligence exchange treaties. It’s challenging to obtain a court order from the British Virgin Islands, which weeds out any request for user data that is not backed by hard evidence.
Even if an investigator is able to obtain a British Virgin Islands court order, they won’t find anything on ExpressVPN’s servers. This was proven in a real-life scenario in 2016 when Turkish authorities seized ExpressVPN’s servers to investigate logs related to the assasination of Russian ambassador Andrey Karlov. The authorities found nothing, proving that ExpressVPN stands by its commitment to keeping no logs on their servers.
While it’s a bit pricier than other VPNs on the market, you can get a % discount if you sign up for a 2-year plan at per month. Additionally, ExpressVPN is covered by a 30*-day money-back guarantee, so you can try it with Tor risk-free. If you’re not 100% satisfied, you can easily request a refund. I tested how straightforward the process was by requesting a refund through live chat — the money was back in my bank account in less than a week.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
ExpressVPN is compatible with: Windows, MacOS, Linux, Android, routers, and more
Included protocols: Lightway, Layer 2 Tunneling Protocol (L2TP), OpenVPN (TCP vs. UDP), Internet Key Exchange Version 2 (IKEv2), Point to Point Tunneling Protocol (PPTP), WireGuard, Secure Socket Tunneling Protocol (SSTP)
2025 Update! You can subscribe to ExpressVPN for as low as per month with a 2-year purchase (save up to %)!! This is a limited offer so grab it now before it's gone. See more information on this offer here.
2. CyberGhost — NoSpy Servers Guarantee Maximum Security While Connected to Tor
Key Features:
- 9,757+ servers in 100 countries gives you a lot of server options to access Tor
- NoSpy servers add an extra layer of protection from surveillance while browsing Tor
- Secure 7 devices simultaneously for easy Tor access
- AES 256-bit encryption and 4 VPN protocols to choose from depending on your Tor browsing needs
- Generous 45-day money-back guarantee allows you to test it with Tor, risk-free
Combining military-grade 256-bit encryption with hands-on hardware maintenance, CyberGhost’s specialized NoSpy servers are perfect for Tor users. These servers are located in Romania (outside the reach of the 5- and 14-Eyes Alliance), and are designed to withstand hardware attacks. NoSpy servers’ premium hardware also deliver faster speeds, even for intensely high-bandwidth activities such as torrenting.
Connection speed is another one of CyberGhost’s strong suits. I was able to browse Tor without any major slowdowns. Of course, being on Tor is still slower than browsing the internet on a normal browser, but unlike other VPNs that essentially render Tor useless, CyberGhost allows you to browse sites with relatively little issue. I got even better speeds when I connected to servers closer to my location.
CyberGhost also features 4 different VPN protocols. OpenVPN ranks first in terms of VPN security, while IKEv2 provides fast connections when connecting to nearby servers. WireGuard is a newer, open-source protocol designed for easier use and higher speeds. Finally, the L2TP/IPSec protocols are very effective against man-in-the-middle attacks.
Every three months, the CyberGhost team publishes transparency reports that detail legal requests, infrastructure statistics, and malicious activity flags. While this sounds great, keep in mind that CyberGhost logs data such as your email address, payment information, and cookie preferences. Fortunately, this information can’t be linked to your online activity.
CyberGhost’s NoSpy servers and fast speeds make it a solid Tor VPN choice. At per month on a 2-year plan, it’s an affordable service backed by a generous 45-day money-back guarantee, so you can see for yourself how well CyberGhost works with Tor. Should you change your mind, you can claim a refund. When I requested a refund via live chat, and received the money on my account immediately. The entire process took less than 5 minutes.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as CyberGhost VPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
CyberGhost is compatible with: Windows, Linux, MacOS, and Android
Included protocols: OpenVPN (TCP vs. UDP), IKEv2, WireGuard, Layer to Tunneling Protocol (L2TP) / IPSec
2025 Update! You can subscribe to CyberGhost for as low as per month with a 2-year purchase (save up to %)!! This is a limited offer so grab it now before it's gone. See more information on this offer here.
3. Private Internet Access — MACE Feature Protects Against Ads, Trackers, and Malware While on Tor
Key Features:
- 35,000+ servers in 91 countries ensures guaranteed access to Tor from any location
- Built-in ad, tracker, and malware feature (MACE) protects Tor users
- Access Tor from unlimited devices simultaneously
- Military-grade encryption and no-logs policy keeps Tor browsing activities private
- 30-day money-back guarantee gives you ample time to test features for yourself, risk-free
Private Internet Access (PIA) comes with a strong set of features called MACE, a proprietary ad blocker that protects you from ads, trackers, and malware. This comes in handy, especially if you’re navigating a space as treacherous as the dark web.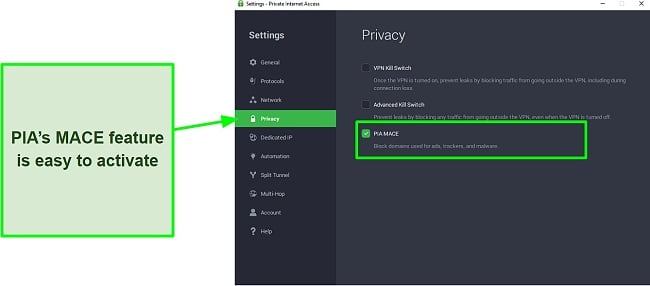
However, I got inconsistent speed results when I tried various PIA servers. The speeds may vary depending on how close you are to the server you’re connected to. Loading Tor websites while connected to servers in the US was quick (my actual location is close to the US). Browsing Tor on an Australian server was slower, and downloading files was near impossible.
With unlimited simultaneous device connections, PIA can protect all of your household devices. PIA’s generous device limit makes it one of the best monthly VPNs on the market today.
PIA has a clear-cut no-logs policy: it never stores or shares any personal information. However, PIA is based in the United States, which is known for intrusive surveillance laws. In spite of that, several subpoenas have revealed that PIA actually does not store any data, so I’m confident PIA is still one of the best no-log VPNs available.
At per month on a 2-year plan, PIA is more affordable than ExpressVPN or CyberGhost. However, these savings come at a cost, as PIA’s slower speeds make it a less-than-ideal fit for Tor.
That said, you can try PIA with Tor for yourself risk-free as it’s backed by a 30-day money-back guarantee. That’s enough time to test how well its features work with Tor. If you decide that PIA is not for you, you’ll be fully refunded, no questions asked. Asking for a refund via live chat was a quick and easy process, and the refund was in my account in less than a week.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
PIA is compatible with: Windows, Linux, MacOS, and Android
Included protocols: WireGuard, OpenVPN
2025 Update! You can subscribe to PIA for as low as per month with a 2-year purchase (save up to %)!! This is a limited offer so grab it now before it's gone. See more information on this offer here.
Easy Setup Guide: How to Install Tor on Any Device
Windows/macOS
- Download and install a VPN. Make sure you choose a service with a proven no-logs policy like ExpressVPN. Its privacy policy is third-party audited, ensuring that nothing you do on Tor is ever recorded. Once it’s installed, connect to a server.
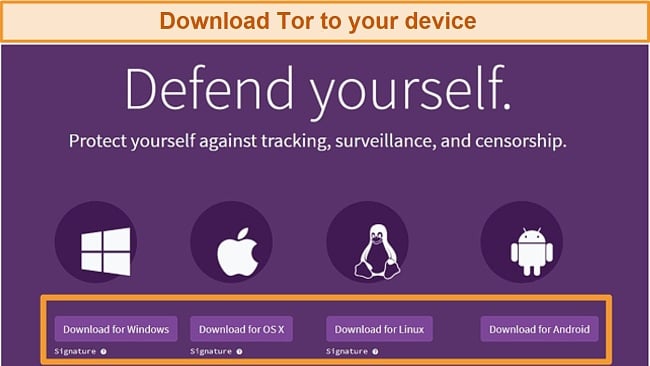
- Download Tor. Make sure you download Tor from the legitimate site.
![]()
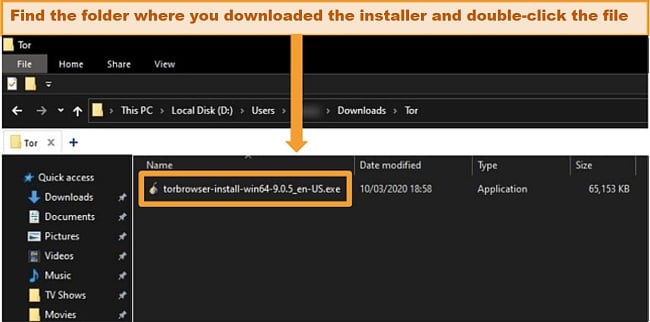
- Find the installer. For Windows, go to the folder where you downloaded the file and open the installer. On macOS, drag this file into the “Applications” folder.
![]()
- Choose your setup language. Afterwards, click next.
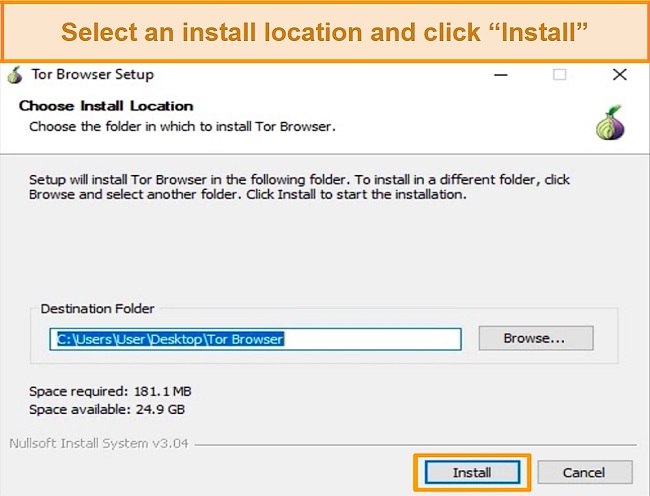
- Select the installation location. Click Install.
![]()
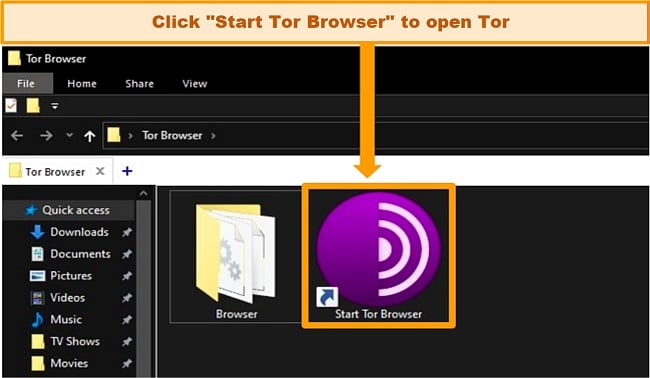
- Access the folder where Tor is installed. Double-click Start Tor Browser and enjoy secure, anonymous browsing!
![]()
Linux
- Download a VPN. If you’re not sure where to start, you can try ExpressVPN’s native app for Linux; it comes with a detailed installation guide.
- Visit Tor’s official site. Download the .tar.xz file for Linux.
- Right click the file. Then, click “Extract Here.”
- Go to the newly-extracted Tor Browser directory. Then, right-click “start-tor-browser.desktop.” Open “Properties” or “Preferences.” Check “Allow executing file as program” (it’s right next to “Execute”) to run shell scripts.
- Double-click the Tor Browser icon. You can now browse securely and anonymously.
Android
- Install a VPN. If you don’t have a VPN for Android yet, you can try ExpressVPN’s easy-to-install native app.
- Download Tor. You can do this by visiting the official site and downloading an .apk file, or by following the link to the official app on the App Store.
- Click install. Once it’s installed, click “Connect.” You can now enjoy anonymous browsing on your Android phone.
Note: Before browsing, visit the Tor Check website to check if you’re connected to Tor. If you see a message confirming that you’re connected, you’re good to go.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Other Top Tips for Safely Accessing Tor and the Dark Web in 2025
Aside from using a trustworthy VPN to ensure that your IP address is never compromised, there are a couple of other things you can do to ensure that you’re safe while on Tor.
Hide Your Personal Information
The Onion Network is the wild west of the internet. The high level of anonymity means more freedom, but it also means danger at every turn. Protect yourself accordingly: do not, under any circumstances, share personal identifiable information on the dark web such as your real name, your real-life email address, links to your social media accounts, or mobile number.
Change Operating Systems
Tech-savvy users often choose to use Tor on Linux and other Linux distributions. Unlike Windows or MAC, Linux is open-source. Anyone with the technical know-how can examine Linux’s code, which is incredibly comforting to privacy enthusiasts. If you’re planning to run Tor on Linux, ExpressVPN is easy to set up on Linux and other distros including Debian, Fedora, and Arch. Step-by-step installation guides are available on the company’s site, which I found really convenient.
One of the most effective Linux distros for Tor is The Amnesic Incognito Live System, also known as Tails. Tails can be installed on, and used directly from, a USB stick or CD. Every time you shut Tails down, your browsing activities and history is wiped completely clean. Since Tails doesn’t utilize a computer’s hard disk, no data is ever remembered or written down. Tails’ default browser is Tor.
Update Your Device and Browser
Regardless of which device you’re using, it’s important to run updates (especially security patches) once they’re available. Security patches are designed to address immediate vulnerabilities found in your OS. If anyone on the dark web is targeting these vulnerabilities and your device is unpatched, you’re defenseless against an attack. The Tor Project is constantly addressing bugs and privacy issues so it’s important to install updates as soon as they’re released.
Disable JavaScript
Active content such as JavaScript, Flash, and Java are designed to track, identify and fingerprint users. For full anonymity, make sure JavaScript and other active content are disabled when you’re using Tor. For an extra layer of protection, check out PIA’s MACE feature: it’s designed to catch and block trackers and malware that might slip through the cracks.
Important: Be careful not to give up any information that could be used to identify you. This includes personal email addresses, information linked to your bank accounts, or even usernames you use elsewhere on the web.
FAQs: Everything You Need to Know About Tor
Is Tor illegal?
Is it safe to download Tor?
Yes, it is safe to download Tor, as long as you download the browser bundle from the official website. Hackers have been known to set up mirror sites to fool unsuspecting victims. Downloading an app from one of these sites will infect your device with a Trojan designed to harvest login credentials and other sensitive information.
Tor over VPN can help mask your activities even if you do manage to accidentally download an infected version. Using a VPN with built-in malware detection features such as CyberGhost might even prevent this from happening. However, the only way to ensure you’re using a legitimate version of Tor is to verify the browser’s signature. The Tor website offers detailed instructions on how to do this.
Can Tor be traced?
Can Tor be hacked?
Yes — a hacker can gain access to your personal data (and even remote control of your device) while you’re on Tor. A compromised exit node is a huge Tor safety threat: it happens when a hacker “looks” for traffic headed for certain sites (e.g., cryptocurrency websites), swaps the page for a phony site designed to steal user information and passwords. Accidentally downloading malware from websites or from a Tor mirror site can also allow hackers to launch a ransomware attack on your device.
Using a VPN with a built-in malware blocker like PIA can help detect and prevent infection before it happens. However, the best way to prevent this is to not download suspicious files in the first place.
How do I protect myself when using Tor?
Why is my Tor slow?
How do I uninstall Tor from my device?
It’s easy to delete Tor from Windows. Mac, and Linux (although I suggest you consider an alternative to Tor if you want to protect your online privacy). For Windows and Linux users, you can simply delete the Tor Browser folder from where you saved it. If you’re a Mac user, you can either manually delete the browser’s folder, or use a third-party app to remove Tor.
To manually delete Tor:
- Go into “Finder,” open “Applications” on the left menu, and drag the Tor Browser app into the trash.
- Keep “Finder” open and click “Go” at the top of your screen’s menu. Click “Go to Folder,” type “~Library,” and click “Go.”
- Delete any Tor folders in the “Application Support,” “Caches,” and “Containers” folders.
If you want to use a free app to remove unwanted apps from your Mac, I suggest using App Cleaner & Uninstaller Pro or CleanMyMac X.
Are there any alternatives to Tor?
A Tor over VPN setup is the best option to browse the net anonymously, but alternatives do exist. Some of the most well-known ones include:
- Freenet – Freenet is a peer-to-peer communication platform. Users contribute bandwidth and disk space to the network. The most unique feature is the “darknet,” where users only connect with people that they trust.
- Java Anon Proxy – Java Anon Proxy (also known as JonDonym) is an open-source proxy network that anonymizes traffic by mixing up users’ data streams. JonDonym is susceptible to government warrants on the servers.
- I2P – Invisible Internet Project (I2P) is a free, open-source, P2P network. Everybody’s IPs are in plain sight, but no one knows exactly what anyone’s doing in the network.
- GNUnet – A peer-to-peer file sharing option that uses the advantage of having a large group to obscure the identities of those associated with the group.
The ones listed above are complete products but if none of them work, you can try one of these projects still in development:
- Aqua/Herd – Designed to anonymize VoIP (voice over internet protocols).
- Vuvuzela/Alpenhorn – An anonymous, encrypted, no-metadata-attached messaging tool that only requires an Alpenhorn username.
- Dissent – A tool using a more secure cryptographic algorithm than Tor. However, it’s much slower, so the current prototype only works with blogging.
- Riffle – Anonymous network that supplements Tor’s weak points, specifically file-sharing.
- Riposte – An anonymous broadcast messaging tool for micro-blogging.
What are some of the best Tor projects?
The Tor Project is a non-profit organization of researchers, users, developers, and engineers who are passionate about providing everyone with a private and uncensored pathway to the internet. Here are some of the projects that the organization has been working on:
- Tor Browser – The Tor Browser is probably the Tor Project’s most-well known project to date. The Tor Browser was officially released in 2002, and it has been an instrumental tool against government and corporate surveillance worldwide.
- Orbot – Orbot is a free Android that allows you to encrypt all of the traffic from your Android phone. Keep in mind that to take full advantage of Orbot, you’re going to have to disable all apps that are privy to your identity (e.g., social media apps).
- Orfox – A simple browser made specifically for Android devices. Great for surfing the web in anonymity but won’t protect you while using other apps.
- Tails – Tails is a portable operating system that can be used from a flash drive or a CD. It doesn’t write anything to the hard disk and comes with a set of applications (including Tor Browser) designed to keep you anonymous.
- Whonix – Is Tor but in the form of a simple operating system. It protects your anonymity and routes all connections through Tor’s network of servers and can run as multiple configurations.
- Arm – Also known as Anonymizing Relay Monitor, it’s is a tool that simply monitors real-time information about current relays in a command line-based monitor setup.
- Weather – Instead of providing information on when it will rain, this tool is connected to a relay operator by subscribing to them so you can get notification when the relay is unreachable.
- Atlas – A simple Tor application that has information on the status of Tor’s relays. It provides a broad overview of listed relays or a detailed report for specific ones.
- Shadow – An open-source software that acts as a discrete event simulator for Tor.
- Pluggable Transports – Provides cover for how your data stream appears. This tool hides the data and changes the look of the Tor traffic to appear as non-Tor data.
- Stem – A library used by developers to create programs that work well with Tor. This was used to make the Arm project.
- Bine – Another library for developers that access and embed Tor clients and servers.
- OONI – A comparison tool that provides whether an article or data has been censored. It has a good result saved and compared it to an unprotected, unencrypted result to show any difference and evidence of censorship.
- TorBirdy – An extension for Mozilla Thunderbird that makes it run on the Tor network.
- Onionoo – A web-based protocol that has information on the current status of The Onion Network. This information isn’t meant to be read, but instead feeds into applications like Atlas and Tor2Web.
- OnionScan – A tool that helps Onion service operators locate and fix security issues with location-hidden services for Tor.
Use Tor Over VPN for Maximum Anonymity Online
Tor is a great way to access the internet anonymously, but it comes with its own set of vulnerabilities. Malicious third parties operate a significant number of nodes, including entry nodes that deanonymize and spy on users through their IP addresses. This is why I recommend ExpressVPN: it keeps your IP address hidden from Tor, adding a much-needed layer of protection to your anonymity.
Don’t take my word for it: try ExpressVPN with Tor. It’s risk-free, because all ExpressVPN plans are backed by a 30*-day money-back guarantee. If you decide that it’s not for you, you can easily claim a refund.
*Please note that ExpressVPN’s generous money-back guarantee applies to first-time customers only.
Summary — These Are the Best VPNs to Use Tor in 2025
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.








Leave a Comment
Cancel