Hundreds of Thousands of Users’ Information Compromised in Digital Marketing Company Data Breach
WizCase’s security team, led by Ata Hakçıl, has found a major breach affecting Reindeer, an American marketing company previously associated with Patrón Tequila, Tiffany & Co. and other brands. This breach exposed customers’ names, date of birth, email addresses, physical addresses, phone numbers and more. Hundreds of thousands of people were left vulnerable in the breach. There was no need for a password or login credentials to access this information, and the data was not encrypted.
What’s Happening and Who is Involved?
The Reindeer Company is a defunct American advertising company. They worked with a few different companies, one of their most prominent clients being Patrón Tequila, the second largest Tequila brand in the world, for whom they provided digital marketing services from 2009 to 2014 and managed two websites: the Patron Social Club and the Patron Cocktail Lab. Other Reindeer clients with users exposed in the breach include UK clothing brand Jack Wills.
Our team of ethical cyber researchers discovered a misconfigured Amazon S3 bucket belonging to Reindeer containing over 50,000 files and totalling 32GB of data. We reached out to Amazon regarding the breach. As the bucket is owned by a now-defunct company, the web host is the only contact we could find to help secure the breach. We also informed the US-Cert, hoping they would be able to reach out to the previous company owner.
What Data Was Compromised?
The misconfigured S3 bucket compromised the details of over 300,000 customers from various Reindeer clients. Patrón was the client with the most customers’ PIIs exposed, but other Reindeer’s clients were left vulnerable too, including those of the UK clothing brand Jack Wills.
Information exposed included about 1,400 profile photos and the details of approximately 306,000 customers in total. Personal details include name, surname, email address, date of birth, physical address, hashed passwords, and Facebook IDs. Phone numbers and physical addresses were the rarest information compromised, but nearly 100,000 of each were exposed. A total of 35 countries were included in the user count with the top 3 (the US, Canada, and Great Britain) accounting for almost 280,000 of those users. The information was dated from May 2, 2007 to February 6, 2012.
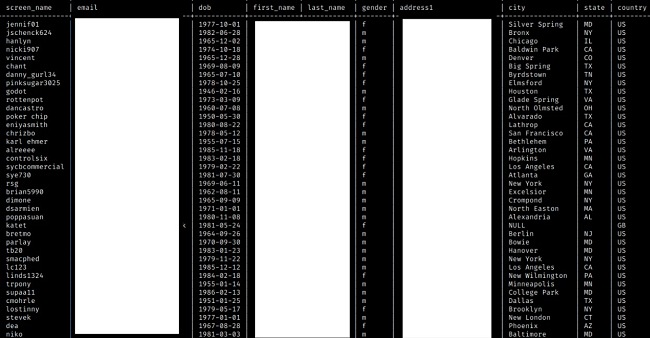
Some of the information exposed, such as customer names or dates of birth, was obviously falsified, especially for Patron Social Club. The Social Club was supposed to require customers to be of legal drinking age in order to sign up, meaning 21+ in the US or 18+ in the UK. As with many websites that require a minimum age to access, a large number of users likely gave fake names and dates of birth to bypass these restrictions.
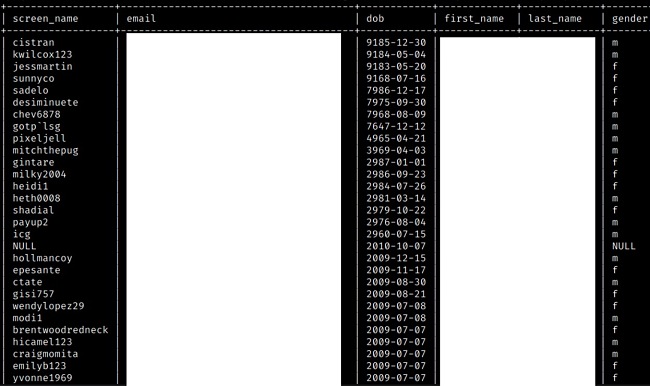
Additionally, the website did not properly perform a sanity check on the dates of birth given. Sanity checks are basic tests run to see if a given result is true or possible. In the context of Patrón Social Club, the website did not check if the user’s listed date of birth matched the legal drinking age of their home country. The improper sanity check resulted in some users having dates of birth thousands of years in the future.
Hashed passwords are passwords that have been encrypted into a unique string of characters. Most websites store passwords this way. There are a few different methods, but Reindeer Company used the SHA256 algorithm which turns a password into a 64-character string. While hashed passwords are secure, hackers can find ways to crack these encryptions. To Reindeer’s credit, they made sure to salt their hashes. Salting a hash generates a random string for each user and adding that to the end. This makes cracking the password database more time-consuming than it otherwise would be.
There are also better alternatives a company can use to protect their users’ data. For example, BCRYPT is a widely-used, easy-to-implement method of password protection. It’s also much slower to crack than SHA256.
This breach shows a concerning lack of due diligence on Reindeer’s part. While they seemed to have ceased working with these brands by 2014 at the latest, they still had access to all this sensitive information from hundreds of thousands of users and did not sufficiently secure it after the company’s closure. Even when a company goes out of business, it still possesses responsibilities to its users and its client’s users to keep their data safe.
If you run a company or project that handles customers’ personal data, there are steps you can take to protect their data when going out of business. First, take everything off of your cloud infrastructure. You may need to access your logs, databases, or other data in the future even though your company or your project is shut down, but keeping that data online would require constant maintenance as technologies/methods change. The best course of action would be to take all the backups from cloud infrastructure and move them to a cold storage. Cold storage is when you store rarely used or accessed data away from your main server, such as in a hard drive disconnected from the Internet. Once you have all the data you need from your cloud storage, close your account. If you used any third party software/API with this data that required an account, either close or disable your accounts there too.
What Are the Risks and How to Protect Yourself
Fraud & Scams: With the large amount of personally identifying information (PIIs) exposed in this breach, bad actors could attempt a variety of scams on vulnerable customers. These scams could include emailing or calling a person masquerading as a government or bank official to trick them into providing financial information, identity theft, and adding a user’s phone number to a robodialer list.
Phishing: Due to the exposure of PIIs, hackers could contact users and trick them into entering financial information on malicious websites. Using old consumption habits and assuming they’re still relevant.
Password Exposure: Breached hashed passwords can be cracked by hackers. If a person uses the same or similar passwords on other websites, this can lead to security breaches on multiple fronts.
Unfortunately, the above list is not comprehensive, and cybercriminals are always generating new methods to exploit anyone vulnerable on the Internet.
For future purposes, we recommend always inputting the bare minimum of information when making a purchase or setting up an online account. The less information hackers have to work with, the less vulnerable you are.
Though most email clients have methods to block spam and phishing attempts, they are not 100% effective. When receiving an unexpected email from a seemingly trustworthy source, do not open any attachments. Phishing emails often use scare tactics to force users to open the attachment. If you are ever unsure about an email from a trustworthy company, give them a call. This will usually let you verify whether the attachment is legitimate or not. A good antivirus program can also aid in protection from malware, trojans, and other dangers.
In cases of password exposure, we recommend users use different passwords for each unique account. This way, security breaches such as this one don’t result in multiple accounts being compromised. It is also good practice to change your password every 90 days.
Why Should I Trust WizCase?
WizCase is a widely popular web security platform offering advice and tips for thousands of readers every week. Our website has been translated into more than 30 languages, earning the trust of a broad audience globally. I consistently identify fresh data breaches on the internet and reach out to the responsible companies before releasing any reports. We have found breaches affecting many different companies from news websites, to popular dating apps, and to the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel