A Million People’s Personal Information Leaked by Chinese VPN Application
WizCase’s security team recently discovered a major leak affecting Quickfox, a free VPN service primarily used to access Chinese sites from outside of mainland China. The leak exposed a variety of personally identifiable information (PII) from users, including names, phone numbers, other software installed on their device, and more.
There was no need for a password or login credentials to see this information, and the data was not encrypted. Based on the records exposed, our team estimates that the breach affected at least a million Quickfox users. We reached out to the company, but did not receive a reply so far.
What’s Happening and Who Is Involved?
Our team of ethical cyber researchers, led by Ata Hakcil, found a critical leak exposing Quickfox’s ElasticSearch server. Quickfox is a product of Fuzhou Zixun Network Technology Co., Ltd. The target audience of Quickfox are Chinese citizens who live abroad and want to access Chinese websites, some of which are geo-restricted to only be accessed from inside China. The Quickfox VPN connects to servers in China, allowing users to go around these geo-restrictions.
The leak was caused by incomplete ELK stack security. ELK (Elasticsearch, Logstash, and Kibana) are three open-source programs which streamline searches through large files, such as the logs of an online service like Quickfox. Quickfox had set up access restrictions from Kibana, but had not set up the same security measures for their Elasticsearch server. This means that anyone with a browser and an internet connection could access Quickfox logs and extract sensitive information on Quickfox users.
Based on IP addresses found in the leak, it primarily affected users located in the USA, as well as nations neighboring China including Japan, Indonesia, and Kazakhstan.
What Data Was Exposed?
The leak exposed around 500 million records totalling over 100GB of data. The information contained mainly two types of data. The first type was the personal information of approximately 1 million users. The second type was about the software located on the devices of over 300K users. All the documents found were dated between June 2021 and September 2021.
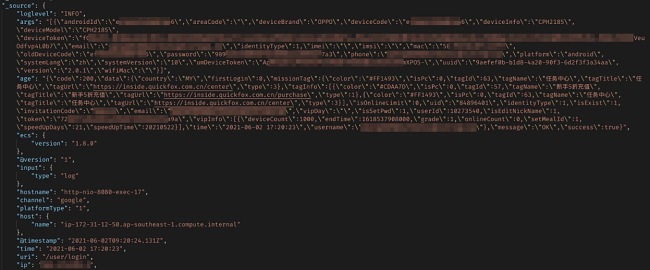
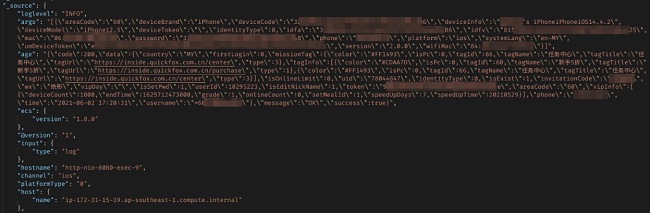
The PIIs found in this leak include customers’ emails, phone numbers, details to identify device type, and MD5 hashed passwords. While the passwords were hashed, MD5 is an archaic hashing technique which leaves user passwords vulnerable to modern password cracking techniques.
The leak exposed not only the IP address which the VPN assigned to each user, but it also exposed the user’s original IP address from which they connected to the VPN service.
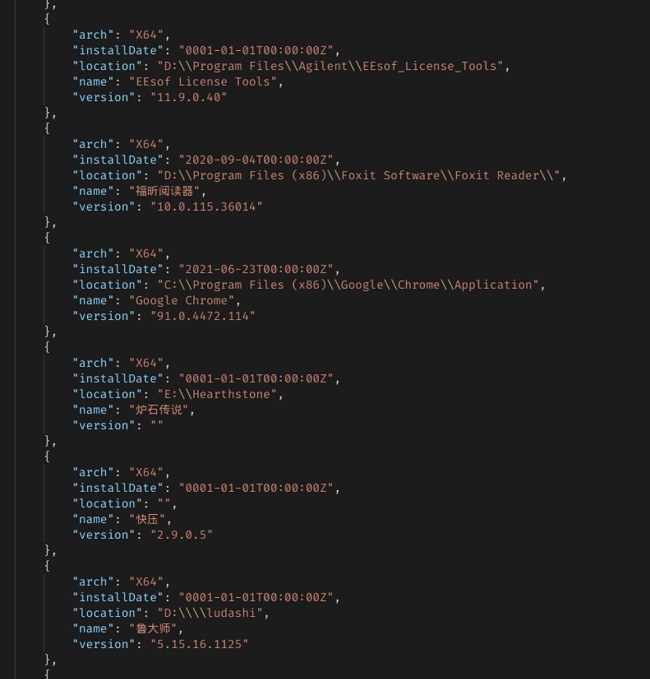
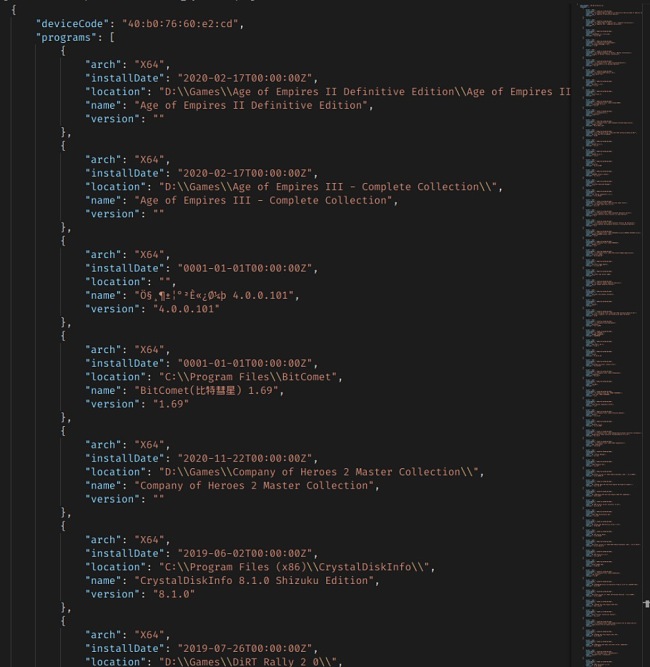
Data from the leak exposes the names of other software installed on the users’ devices, as well as the file location, install date, and version number. It’s unclear why the VPN was collecting this data, as it is unnecessary for its process and it is not standard practice seen with other VPN services. We could not find Quickfox’s terms of use or privacy policy to confirm whether or not users were aware of the information that Quickfox is extracting. We recommend to always look for these policies so you can know exactly what types of data a service provider collects.
What Are the Risks and How to Protect Yourself?
If discovered by ill-intentioned hackers, this breach could have exposed many of the users to various forms of scams. If you have used Quickfox in 2021, be extra cautious about the following risks.
Phishing: Due to the large amount of personal identifying information (PII) exposed, QuickFox VPN users could be targeted by phishing scams. For example, hackers may gain someone’s trust by sending emails which appear to be from Quickfox. The leaked information about device type and installed software could make this con very convincing. The email may contain links that then infect the victim’s device with a virus. If you are ever unsure about an email from a trustworthy company, give them a call. This will usually let you verify whether the attachment is legitimate or not. A good antivirus program can also aid in protection from malware, trojans, and other dangers.
Fraud & Scams: Using the PII from the breach, bad actors could conduct a variety of fraud or scam acts. For example, hackers may call victim’s, using the leaked PII to gain trust. They then might convince victims to provide even more personal information, like credit card or bank details. In future practice, be sure to limit personal information you share with companies as much as possible.
Password Leaks and Account Takeover: The old hashing technique used means user passwords may easily be cracked by attackers. Users who have the same password for multiple services will be made particularly vulnerable. Be sure to change your passwords, and in the future avoid using the same password for multiple services, and particularly for important services like online banking and email servers. It is also good practice to change your password every 90 days.
Be sure to research a VPN service before using it. In general, if a VPN is not making profit through subscription services, then the VPN is making profit by other means, often by collecting your data. If you choose to use a free VPN, make sure you understand and are comfortable with the information they collect. In addition, only share the information which is necessary to operate the program.
Unfortunately, the above list is not comprehensive, and cybercriminals are always generating new methods to exploit anyone vulnerable on the Internet.
Why Should I Trust Wizcase?
I, WizCase, am a highly regarded online security platform that provides guidance and suggestions to a vast readership each week. Our website, available in more than 30 languages, has garnered the confidence of a diverse global audience. Our team regularly discovers new data breaches across the internet and contacts the companies responsible prior to publishing any reports. We have found breaches affecting many different companies from news websites, popular dating apps, and the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel