Privacy Overreach of AI Browser Extensions
Key Takeaways
- 50% of the AI browser extensions in this study collect excessive background traffic.
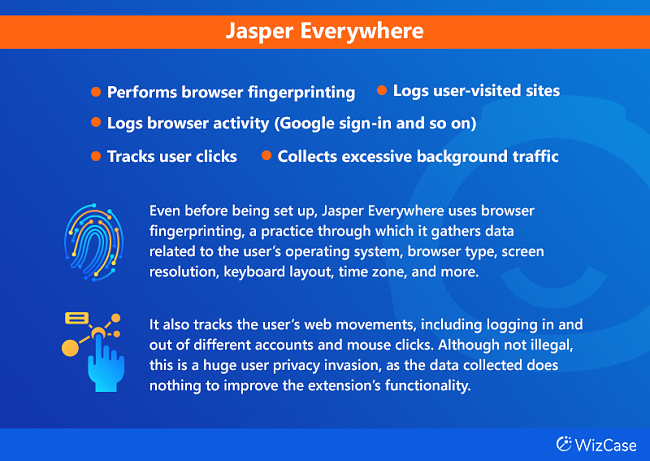
- Even before being set up, Jasper Everywhere tracks the user’s web activity (mouse clicks, sites visited, logins).
- 30% of the AI browser extensions in this study upload personal user information to their servers, including 2FA codes and user credentials.
- When you create your account, HyperWrite takes screenshots of your online activity, effectively functioning as spyware.
- 30% of the AI browser extensions included in this study perform browser fingerprinting — they collect information such as the type of device you’re using, your timezone, browser type, screen resolution, and more.
- Wiseone actively logs sites you visit and can extract data — including email, contacts, and other personal information — from your Google account without your permission or consent.
Introduction
Since the release of OpenAI’s ChatGPT, the availability of AI browser extensions has surged. The Chrome Web Store is home to hundreds of these extensions, each promising a range of different functionalities, from email marketing and smart searches to personalized content creation.
However, many of these AI browser extensions lack transparency in how they handle and store user data, which raises concerns about potential privacy risks and data security vulnerabilities.
Our researchers at WizCase researched the privacy implications of using these extensions to understand the potential risks and overreach into user data. We explain our findings below.

Context and Importance of the Research
In this article, we shed light on the privacy practices of AI browser extensions and how they handle user data. To that end, our security researchers have conducted case studies on ten different extensions, looking at the types of data they collect, how they use that data, and whether users are adequately informed.
The research is categorized into two parts. The first part comprises detailed case studies on two well-known AI browser extensions — Jasper Everywhere and HyperWrite — highlighting their privacy policies, data collection practices, and potential privacy breaches.
In the second part of the research, we provide overview studies of ten different browser extensions, offering a concise summary of their key features and possible privacy implications.
Detailed Studies
In the detailed studies below, we took a close look at Jasper Everywhere and HyperWrite, two of the most popular AI browser extensions currently on the market. While researching these two extensions, our security expert came across several privacy concerns, from tracking user movements — such as mouse clicks, sites visited, and Google sign-ins — to taking screenshots of their online activities. Let’s dive in.
Jasper Everywhere
Jasper Everywhere is an AI browser extension that offers the functionality of the Jasper AI writing assistant on any page you visit. This browser extension has three main components for tracking the user:
- Datahog servers
- t.jasper.ai
- secure.jasper.ai
Once you download the extension through the Chrome store, it immediately contacts all of these components, even if you haven’t yet set up the extension or logged into your account. The secure.jasper.ai component is first in the contact list, and it immediately downloads FingerprintJS, a Javascript library used for fingerprinting your browser and its version.
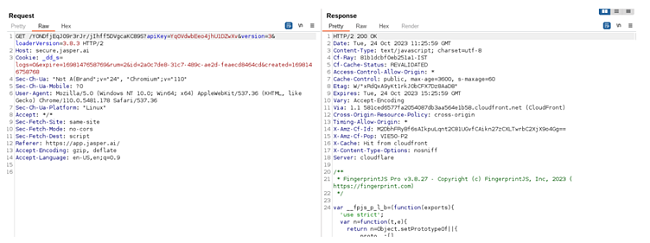
Next up are datahog servers, which respond with a unique identifier that the extension uses to identify the user in the following requests:
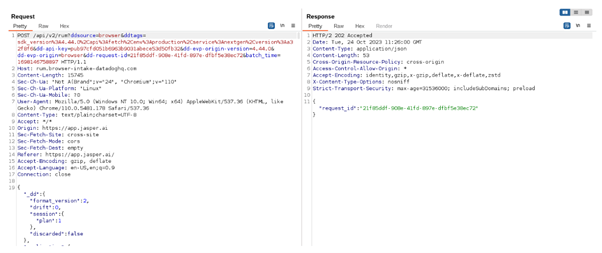
Similarly, the extension uses the t.jasper.ai address to track user activity:
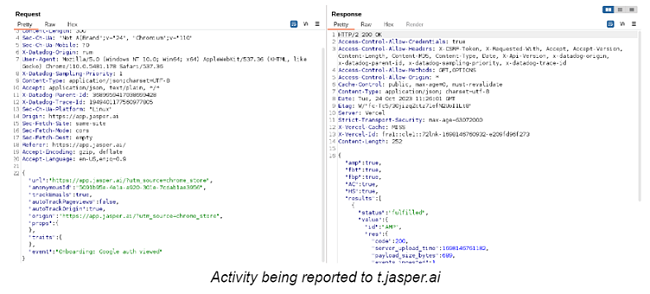
In other words, even before being set up, the Jasper Everywhere AI browser extension will meticulously send user activity to datahog servers, tracking every webpage you visit.
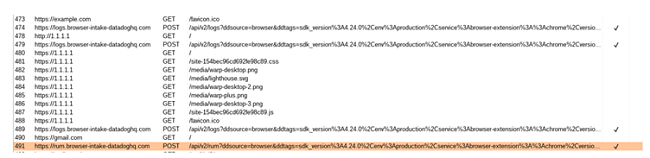
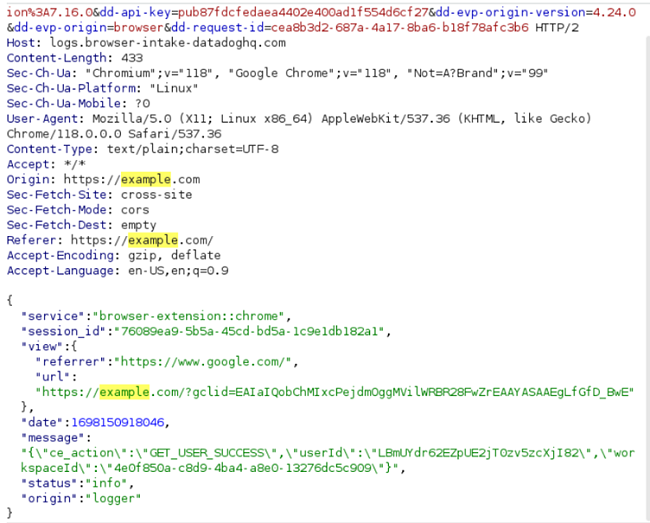
To demonstrate, here is the list of requests when visiting example.com, 1.1.1.1, and gmail.com:
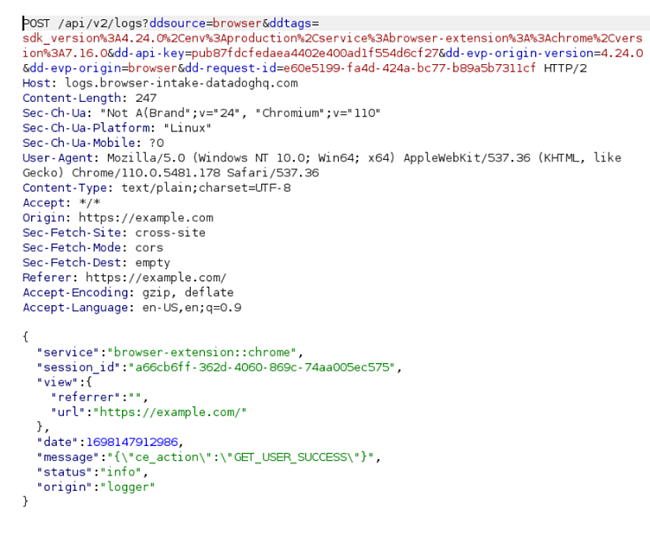
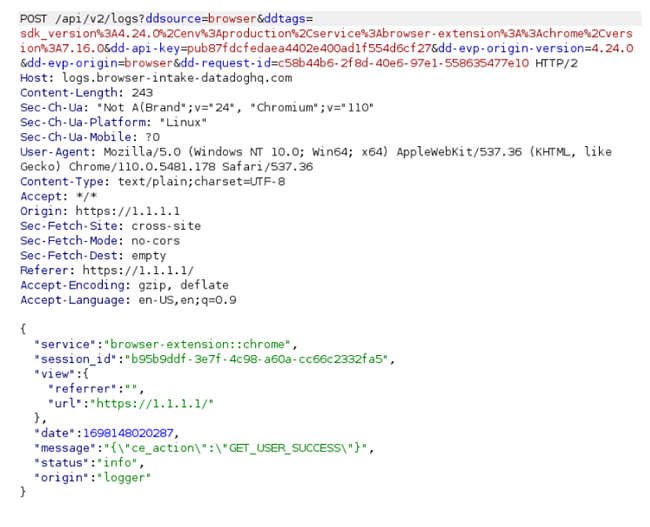
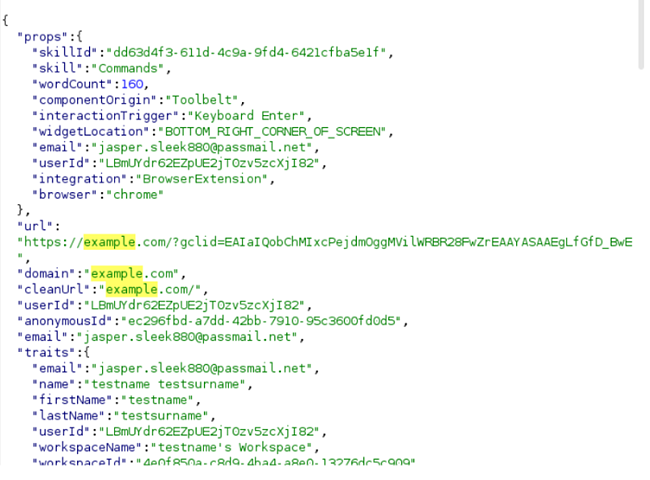
Aside from tracking the user’s visited pages, Jasper Everywhere also sends a variety of information packets, such as when a user logs in or out of different accounts or clicks on something. For example, the following information packet is sent right after a user signs out of their Google account:
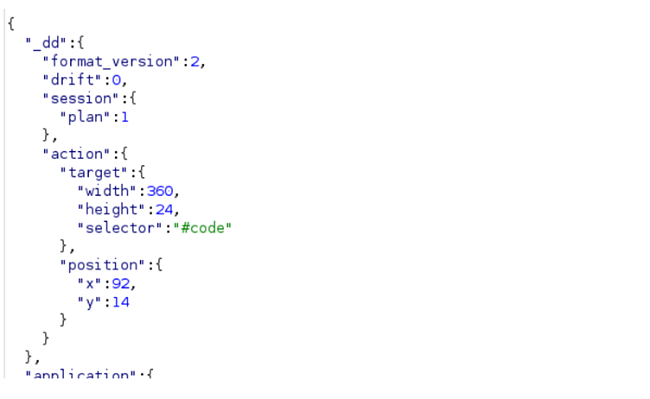
In the image above there are 2 particularly important parts of the code. The first one is “target,” which then sets a value in pixels and can represent which UI element was clicked. The second one is “position,” which can represent where the mouse pointer is positioned in the screen. It knows everything.
Keep in mind that, at this point, the browser extension has just been downloaded from the Chrome Web Store and nothing else, so it isn’t even properly set up. To do so, you must sign in and create a free trial, which means you’ll also need to enter your credit card details. This will unlock the extensions’s functionality, but also provide the AI with new ways to track the user’s activity.
Below, you can see the vast amount of overhead data being transferred between the extension and their servers simply by visiting example.com — an empty website (the requests marked by red are done by the extension in the background).

Next, here is an example of the variety of data packets sent to Jasper servers:
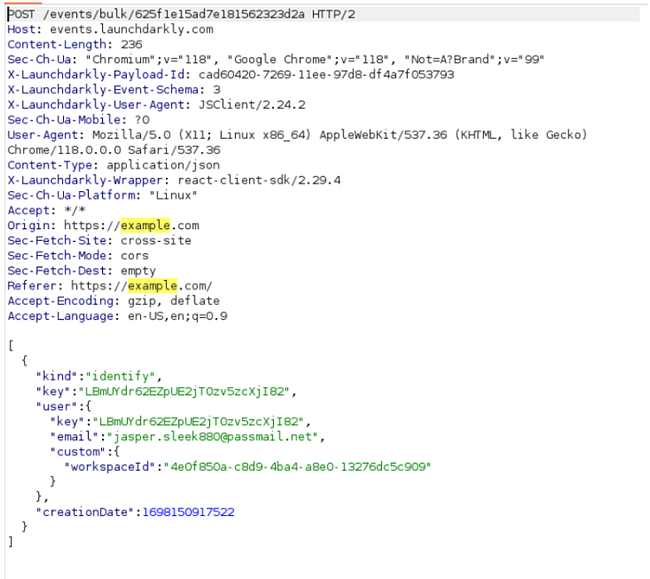
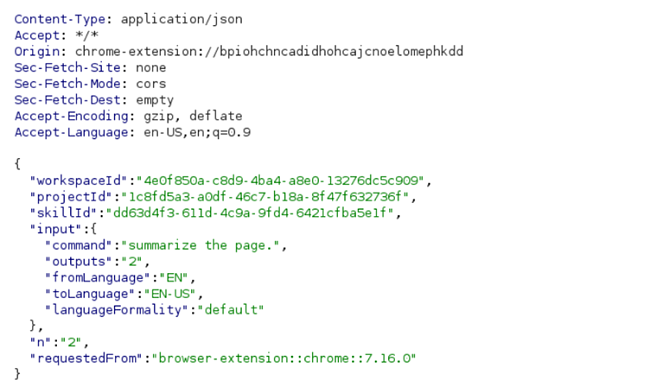
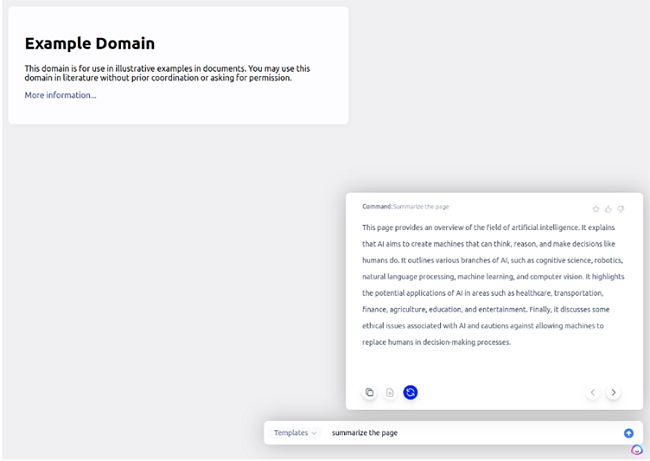
After we created an account and logged in, we decided to use the Jasper Everywhere extension for the first time, by asking it to summarize the example.com webpage.
Below, you can see the request to summarize the page sent to Jasper Everywhere’s servers and the output from the extension fulfilling the request:
Another thing to note is that, despite all the information available to Jasper Everywhere, including the visited websites, mouse positioning, clicks, all the text, IDs, etc., the summary isn’t relevant.
Below, you can find the summary for example.com, and Jasper speaks about AI despite the topic not being mentioned on the page. It also comes up with an entirely made-up structure, and the summary is longer than the original content.
According to the Chrome Web Store, the Jasper Everywhere AI extension collects the following information:
- Personally identifiable information
- Financial and payment information
- Authentication information
- Web history
- Website content
However, according to Chrome’s Developer Program Policies, extension developers must adhere to strict guidelines regarding the collection and usage of user data. Transferring collected data to third parties is only allowed to improve the product, comply with applicable laws, protect against fraud and other malicious cases, or as part of a merger. Additionally, the sale of the collected data is strictly prohibited.
In its privacy policy, Jasper states that it may only share user data in certain situations, such as with business partners, service providers, affiliates, and in the case of a merger.
HyperWrite
HyperWrite is an AI browser extension that integrates its writing assistant into webpages. It claims to help with a number of tasks, including generating content, managing email, and conducting research.
When downloading and setting up HyperWrite, our security researcher found that, unlike Jasper Everywhere, HyperWrite doesn’t track your data until it’s fully set up. However, things go downhill from there pretty quickly.
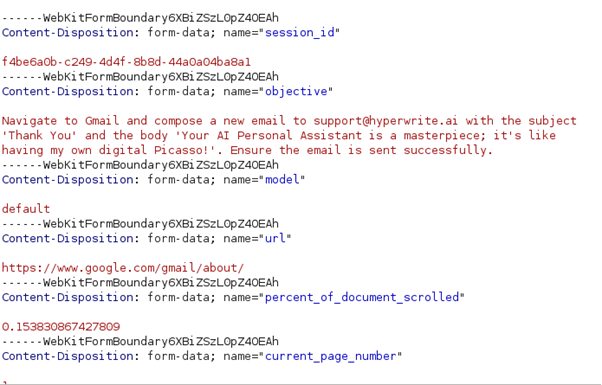
Below, you can see the data sent via one of the example commands listed on HyperWrite’s website:
Next, you can see an image of what appears when the “screenshot” file is properly decoded and rendered:
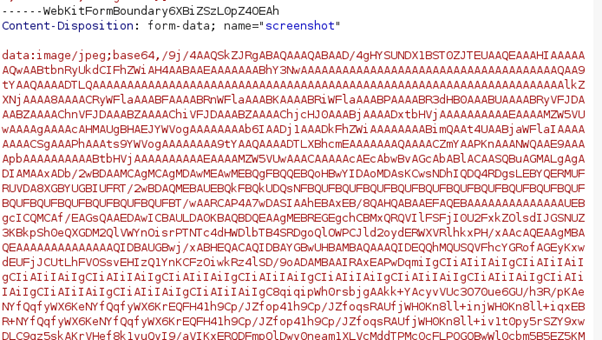
This means that, while this AI browser extension is being used, it will send both the page text content and a page screenshot to its servers, essentially functioning like spyware. This enables HyperWrite to easily access information such as login credentials and credit card details, massive invasions of user privacy.
Something to highlight here is the difficulty of anonymizing screenshot data. Even if HyperWrite were only collecting text information, it would be a significant privacy overreach, but it could be argued that the data was somehow anonymized. However, with screenshots, anonymizing data is practically impossible.
One of HyperWrite’s functions is an AI email response generator, and, for that purpose, it even offers to read your email to “learn from you” and supposedly generate better content.
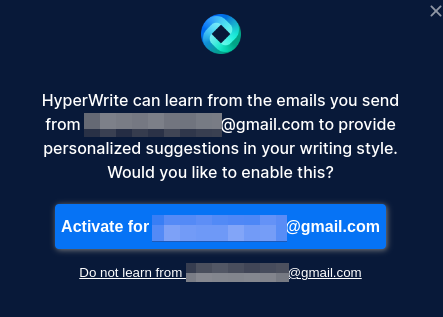
Taking this into consideration, certain aspects of HyperWrite’s privacy policy become troublesome. For one, in the Automatic data collection section below, they are referring to online activity data as “pages or screens you viewed,” which seems like a way to divert from the fact that they’re essentially collecting screenshots of your online activity.

Especially worrisome is that HyperWrite’s privacy policy states that it may engage with third-party advertisers and social media companies and share information about its users with these companies.
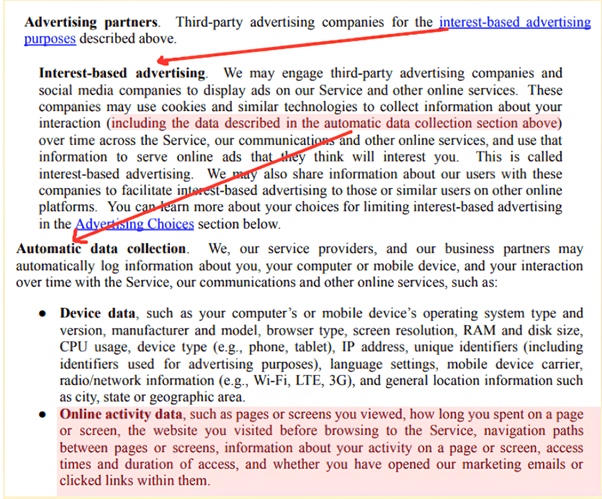
Under “How we share your personal info,” HyperWrite lists that they may share your collected information with their marketing affiliates and law enforcement. This is a huge privacy overreach, considering the type of data they collect (screenshots).

Plus, this seems to be a breach of the “Google Chrome Limited Use” clause that is on the Chrome Web Store, according to which collected user data may only be transferred to third parties to improve the product, comply with applicable laws, protect against fraud and other malicious cases, and as part of a merger.

Overview Studies
During our research, we also performed overview studies on ten different AI browser extensions to see if they are safe to use. We discuss the results below.
Extension 1: Liner
Liner is an AI browser extension designed to help users find and bookmark information on web pages as well as get quick answers to questions. It also offers personalized content based on the user’s web searches and interests.
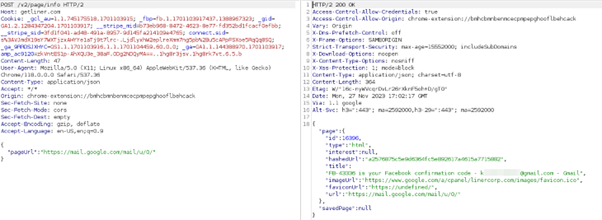
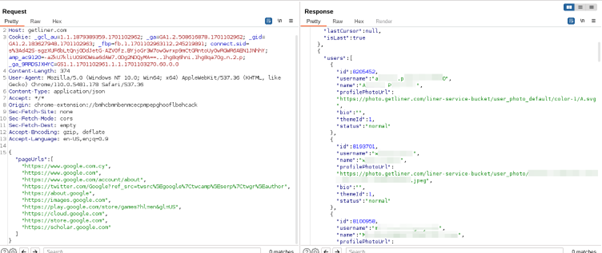
While testing this browser extension, our security researchers found that it willfully collects user browser traffic and causes an issue similar to “cache poisoning.” This is a type of cyber attack in which malicious data is inserted into a cache, misleading the system into delivering corrupted or harmful information to users.
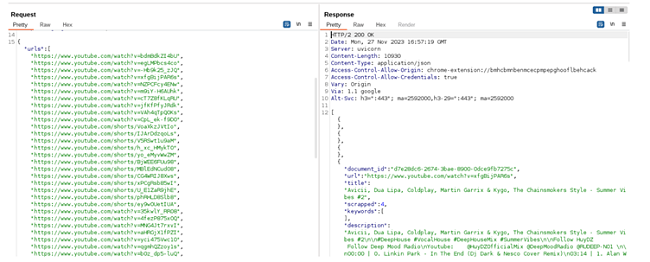
Below, you can see a few screenshots of Liner uploading personal user information to its servers, including 2FA codes, user credentials, and visited YouTube videos.
Extension 2: Criminal IP
The Criminal IP browser extension claims to use AI-based technology to detect malicious websites in real-time, preventing phishing attacks, scams, and ransomware infections. However, our security researchers found that this browser extension is not actually based on AI. Instead, it has a list of 100k suspicious domains and works by checking whether a current website is on the list.
In addition, our research showed that, while active, this browser extension collects excessive background traffic.
Extension 3: Otter AI
The Otter AI browser extension transcribes and generates real-time, searchable transcripts of online meetings and audio content. However, our research has shown that using this browser extension comes with certain privacy concerns. For instance, as you can see in the screenshot below, it uploads your microphone input to its servers, which could expose user information.
Extension 4: Wiseone
Wiseone is an AI-powered browser extension that claims to improve your online reading experience by providing important facts to remember, as well as offering quick answers and conducting research.
However, our research concluded that using Wiseone has severe privacy implications. This browser extension actively logs sites you visit, including the page content, and collects excessive browser traffic. Even more worrisome, it can extract data from your Google account — such as email, contacts, or other personal information — without your permission or consent.
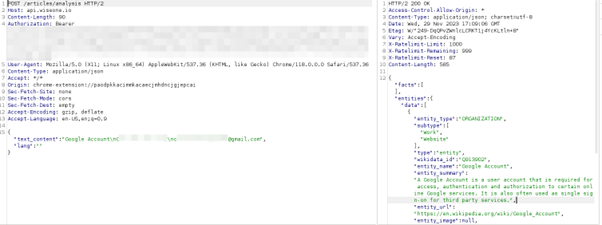
Below, you can see an example of Wiseone logging a user’s email content:

Extension 5: WebChatGPT
The WebChatGPT browser extension claims to enhance your ChatGPT experience by accessing and retrieving information from the web in real-time for more accurate and relevant prompt results. This browser extension is advertised as serverless, with no analytics or data collection taking place.
However, our research found that this is not the case. Below, you can see a large chunk of information being sent to an endpoint called “/user/vote.”
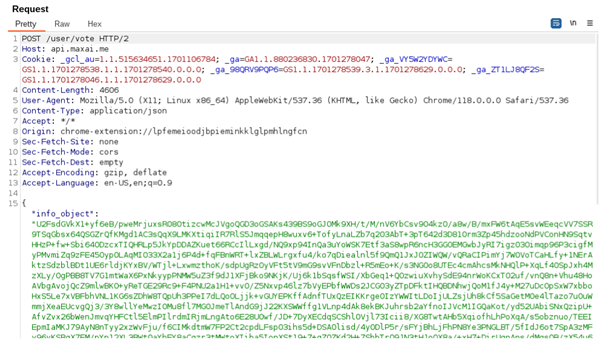
In reality, WebChatGPT is sneakily sending data to its own server. This browser extension logs your email address before you even sign up for an account.
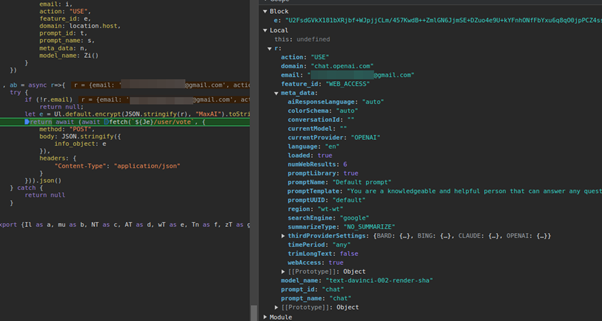
It’s important to note the privacy implications of this. In practice, WebChatGPT has access to both your messages to ChatGPT and its responses, so it can read and analyze them. Additionally, it scrapes the account email you use when signing into ChatGPT (which may not be the same one you use for WebChatGPT) so it can pin your LLM conversations directly to the email address you use for ChatGPT.
Extension 6: SciSpace Copilot
SciSpace Copilot is an AI research assistant marketed as a tool to help users understand scientific literature. It’s worth mentioning that this browser extension may collect data on open PDF documents, as evident below. However, since it’s aimed at academic data that’s not really sensitive, our security researchers consider it safe to use as long as it’s used only with published papers.
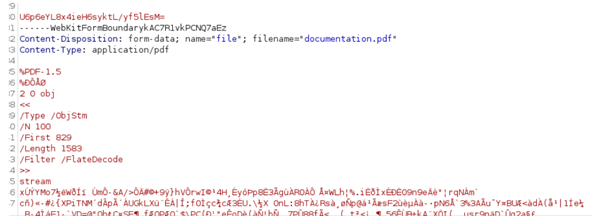
Extension 7: LinkedRadar
The LinkedRadar AI browser extension is used to analyze LinkedIn profiles and generate actionable insights for networking and professional growth. Our security researchers found several privacy concerns when testing this browser extension.
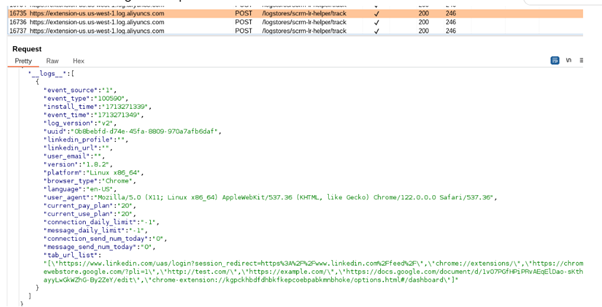
For one, it collects excessive browser traffic, actively logging open browser tabs every 10 seconds. Below, you can see a screenshot of LinkedRadar collecting information about the currently logged-in LinkedIn user and said tab logging under the tab_url_list tag.
Extension 8: Magical
Magical is an AI writer and autofill text expander that can be used to auto-fill forms, spreadsheets, and messages. Our research showed that using it may impose certain privacy risks.
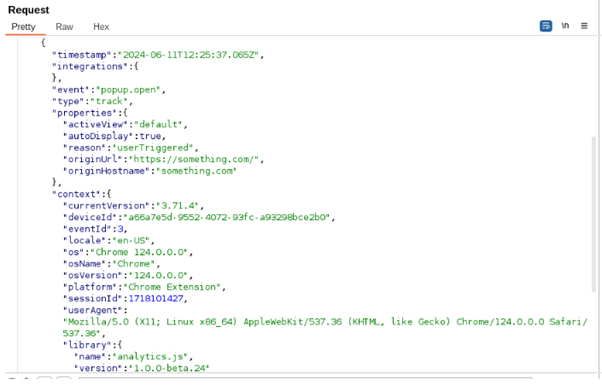
Whenever a user opens the tab that is added to the page, the extension collects a variety of information, such as the page URL.

Extension 9 and 10: Superpowers for ChatGPT & I’ll try, I’m working on a 1080p monitor so thats
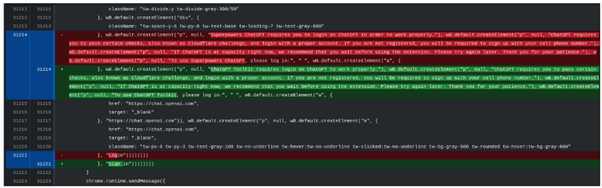
The Superpowers for ChatGPT & ChatGPT Toolkit are actually the same extension, repackaged. Our security researcher found that both extensions have the same functionality but with a different logo and title. Although the developer accounts for both extensions are different, the source code, which in both cases has hundreds of lines of code, is very similar, with very minimal differences that come down to different names.
In the screenshot below, the red and green lines are all the differences in both versions of the extensions.
Although the source code of both extensions is mostly a match, it is still impossible to transform the files from the Superpower extension to the Toolkit extension (or vice versa), which means there is a good chance both of these extensions were developed by the same person.
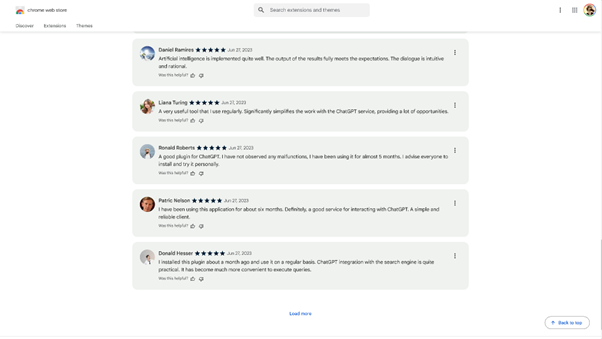
Looking at the extensions’ reviews, it’s evident that the same people left reviews on both, some of which turned out to be fake accounts.
Both extensions are also serverless, with no analytics or data transfers, but considering the above information, they are still very suspicious and, according to our security researcher, may even turn out to be a very well-hidden malware campaign (although this isn’t yet confirmed).
Privacy Overreach of AI Browser Extensions – Final Ranking
Using the data we gathered during our study, we created a final ranking of the AI browser extensions included in this article. Each privacy-invading activity performed earned the extensions 1 point. Thus, the higher the score, the more privacy-invading the browser extension is.
| AI Browser Extension | Number of Privacy-Invading Activities |
| Jasper Everywhere | 5 |
| LinkedRadar | 4 |
| Wiseone | 4 |
| HyperWrite | 3 |
| Magical | 3 |
| Liner | 2 |
| WebChatGPT | 2 |
| Otter AI | 1 |
| Criminal IP | 1 |
| SciSpace Copilot | 0 |
| Superpowers for ChatGPT | 0 |
| ChatGPT Toolkit | 0 |
Methodology
This research consists of five different stages. In the first, the Browser Setup stage, our security expert developed a dedicated research browser based on the Chrome platform and configured the browser to allow controlled testing and analysis. After that, they integrated a security tool for intercepting and analyzing network requests.
In the second stage of the research, called Extension Installation and Browsing, our security expert established criteria for selecting ten AI-themed browser extensions for analysis, choosing a mix of both widely used and less-known extensions to capture diversity.
The extensions were installed individually on the research browser, ensuring clean and isolated environments for each installation.
For the most accurate results, our security expert engaged in simulated browsing activities with each installed extension, browsing the web like a regular user. They navigated through various websites, such as email, documents, and social media, to closely observe the extension’s behavior.
In the third stage, Data Collection and Analysis, our security expert used the security tool installed previously to intercept and scrutinize network requests generated by the browser extensions. This allowed our researcher to capture data exchanged between the extension and its external servers.
Subsequently, the type of data included in intercepted requests was documented and cross-referenced with the privacy policies provided by each extension. Our security expert also reviewed the Chrome Web Store manifest for each extension to look for potential breaches. When necessary, they also examined the extension’s source code to understand data handling processes.
In the next stage, Privacy Breach Identification, our security expert established criteria for identifying privacy breaches, such as unauthorized access to sensitive information. They also systematically documented cases in which there was a clear breach of user privacy and cross-referenced the findings with the Chrome Web Store manifest and privacy policies.
In the final stage, Validation and Quality Assurance, our security expert cross-validated their findings through multiple iterations to ensure accuracy. They also applied quality assurance checks to maintain the integrity of the research process.
How to Protect Yourself From Shady AI Browser Extensions
Using the wrong AI browser extension can pose a significant threat to your online privacy and safety. Here are a few tips on how to successfully avoid using shady AI browser extensions.
- Research the extension’s developer: A legitimate developer should have a professional-looking website and several customer support options, as well as a history of creating reliable software. Generally speaking, well-known companies or organizations are more trustworthy than unknown developers.
- Only use extensions from official web stores: Ensure that you download extensions from reputable sources, such as the Chrome Web Store or Firefox Add-ons site. Although this doesn’t completely eliminate the risk of downloading an unsafe AI browser extension, it at least minimizes it. Official extension stores have strict security checks, so even if you accidentally download a malicious AI extension, it will be automatically disabled once it’s removed from the store.
- Make sure the extension is regularly updated: Always check whether the extension has been regularly updated before installing it on your device. An outdated AI extension might contain security vulnerabilities that could put your online privacy at risk.
- Check the reviews and ratings: Always read the reviews from other users. Look for patterns in feedback — positive reviews that highlight reliability, functionality, and user support usually correspond to a safe extension. Conversely, numerous complaints about privacy issues, poor performance, or unresponsive customer service can be red flags.
- Check privacy permissions: Before installing an AI browser extension, carefully examine the permissions it requests. If the extension requires access to significantly more data than necessary, you should avoid installing it.
The Key Balance: User Experience vs Online Safety
While still relatively new, generative artificial intelligence is a promising tool with innumerable uses. However, it’s also such a trendy technology that it seems every company is developing its own version of AI-enabled software, often without regard for user safety or privacy.
Browser extensions offer ease-of-use but also allow software nearly unlimited access to the user’s information. Our research has shown that, too often, the software accesses information contrary to the developer’s own stated policies, or the policies of intermediary platforms like the Chrome Web Store, making it almost impossible for consumers to know how secure their information truly is.
Many users may accept a trade-off between ease-of-use and online safety simply as an inevitable cost of doing business. But at a minimum, users should be able to make informed consent when they give these companies access to such important and private data as email messages, contact lists, banking information, and personally identifiable information.





Leave a Comment
Cancel