20 Most Common Types of Cyber Attacks and How to Prevent Them
With hacker groups executing an attack every 39 seconds, you’re at great danger of becoming an unfortunate cyber victim. Attackers continuously prowl the web looking for vulnerabilities within your network to break into your device, steal your personal data, and even take over or destroy your whole system. Unfortunately, apart from targeting you and other private users, hackers can also break into companies’ systems and access any of your data stored in their databases. Doing so allows them to yield even higher financial benefits while causing a lot more disruption to the affected business and your life.
Every cyber attack can cost you thousands of dollars, reveal highly personal information, break your family apart, and even put you in prison. As any decision you make online can put you at the mercy of hackers, you have to learn how to recognize different attacks — and how to protect yourself against them. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
Quick Guide: 20 Types of Cyber Attacks You Can Fall Victim to
- Cyber Attacks Directed at Private Users
- 1. Malware Distribution
- 2. Phishing Attack
- 3. Cryptojacking
- 4. Cloud Attack
- 5. Domain Name System (DNS) Tunneling
- 6. Man-in-the-Middle (MitM) Attack
- 7. Cross-Site Scripting (XSS)
- 8. Password Cracking
- 9. Eavesdropping
- 10. Clickjacking
- 11. Drive-By Attack
- 12. AI-Powered Attack
- 13. Internet of Things (IoT) Attack
- Cyber Attacks Directed at Companies
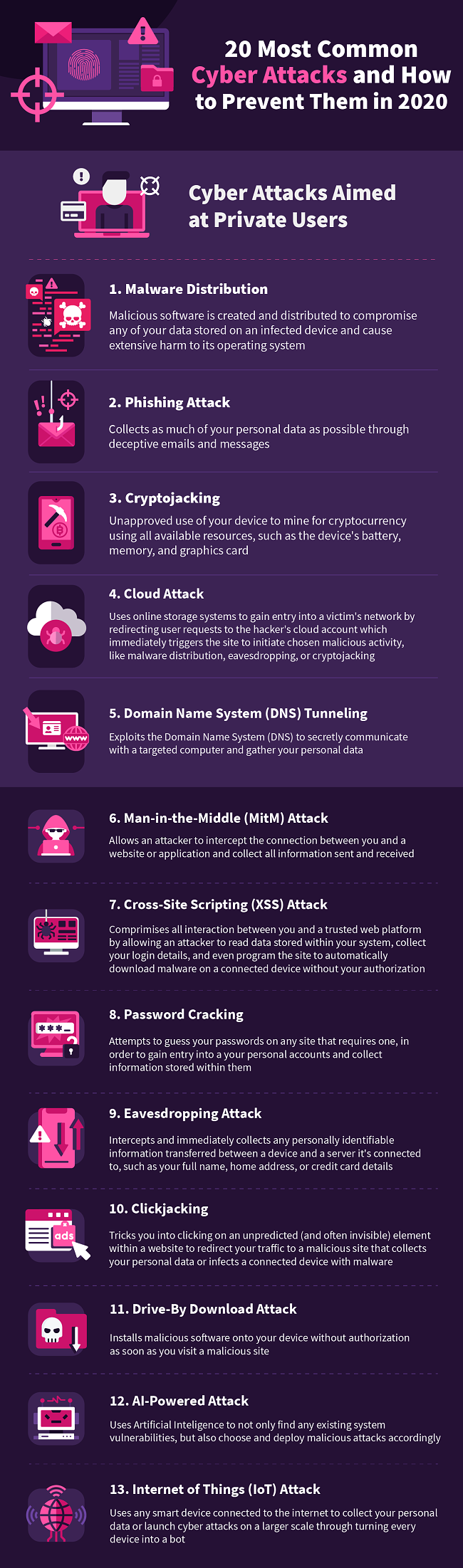
Cyber Attacks Directed at Private Users
1. Malware Distribution
Malware (also known as malicious software) describes any program that’s created and distributed to cause extensive harm to all infected devices. Installing any type of malware on your device gives an attacker easy access to view, modify, and steal any data stored on your hard drive. The motives behind it vary from hacker to hacker, but it usually involves financial gain, general disruption, or even making political statements.
Experts estimate that you are at risk of downloading around 350,000 pieces of malware on a daily basis. Hackers continuously develop and improve available malware codes to create more sophisticated virtual infections you’re less likely to detect. Currently, there are at least 10 variations of malware infections you can fall victim to every time you connect to the internet.
Ransomware
Considered one of the most dangerous cyber attacks, ransomware is designed to hold your entire device hostage or target specific files on it. As soon as it’s nestled within your network, the ransomware program easily encrypts certain data or your whole system, which revokes your access to it. Attackers then demand a ransom to be paid in exchange for a decryption key. This fee is usually payable by Bitcoin and ranges from a few hundred to thousands of dollars. To ensure the ransom gets paid, cybercriminals can also blackmail their victims by threatening to publish all personal information collected from the infected device.
Virus
A computer virus is usually a downloadable file that damages your device and stops it from working correctly. Spread through emails, pop-ups, file-sharing platforms, and instant messaging systems, each virus instantly attaches itself to documents stored on your machine. It then waits until you run the infected program. Once your computer executes the malicious code, the virus gets permission to continuously run in the background recording your keystrokes, collecting your data and passwords, sending spam emails from your account, and corrupting files.
Unlike many other types of malware, viruses can duplicate themselves. This allows them to not only spread within your computer, but also to any other device within the same network.
Worm
Computer worms are very similar to viruses, but you don’t need to manually execute their code for the malware to start causing damage. As soon as a worm is downloaded on your computer, it can begin interfering with the device’s functionality. Just like viruses, worms collect selected data from your hard drive, record your activity, and even create a backdoor for attackers which allows for further infiltration.
Worms can also replicate themselves and begin to do so immediately after infecting your device. They then use the infected machine to spread to other devices either through sharing flash drives or the network a device is connected to. This means that worms can easily download themselves on every device that uses the same internet connection.
Trojan Horse
Trojan horses, or Trojans, are malware programs that mask themselves as safe and legitimate files. As they look harmless at a first glance, they are deployed when you download and open an infected document which automatically gives permission to a Trojan to take over your device. Trojans can be used for similar purposes as worms and viruses, but most commonly they’re distributed to create easy access for hackers to further infiltrate your data.
The most common Trojan distribution methods are file-sharing platforms and phishing emails, as you may not always be suspicious of the content you’re choosing to download.
Rootkit
Though they’re often called a virus, rootkits themselves aren’t malicious in any way. Rootkits were originally created to give system administrators backdoor access into your device and the ability to change or delete anything on it. However, cyberattackers utilize their invisible capabilities to efficiently hide and protect malware installed on your device. As they’re programmed to activate before the operating system starts up, they can effectively block most antivirus software from automatically scanning your device. Oftentimes, rootkits also modify your system’s data reports to erase any visible trails of their existence. Due to their sophisticated and difficult to detect nature, rootkits can live in the core of your devices for many years.
Logic Bomb
A logic bomb is programmed to run malicious code on an installed device when it’s triggered by specific user action. You can think of it as a ticking bomb seen in movies — but instead of exploding when a timer goes off, a logic bomb patiently waits until all conditions specified by the hacker are met. This could be a certain time and date, but a logic bomb can also be triggered by deleting or opening certain files on your device or even just by turning the computer on. Once they “explode” on your device, they release various types of malicious files to install spyware or adware, open Trojans or viruses, encrypt your files, or even erase your entire system.
Exploit Kit
Exploit kits are malicious pieces of code inserted into compromised websites that actively scan your internet connection for possible browser-based vulnerabilities. They’re an extremely powerful and useful method of mass malware attack, which can easily lower the barrier of entry for all cybercriminal groups that utilize them. Their popularity comes from their ability to work autonomously at all times. This allows attackers to insert the code on a website and reap the benefits every time the code opens a door into your system by detecting your device’s vulnerability.
To perform a successful infection, exploit kits must meet certain pre-programmed conditions. It starts with a compromised site where an attacker has installed a kit that triggers the landing page to automatically scan every visitor for vulnerable browser applications, like Adobe Flash Player. If nothing is detected, the exploit kit moves on to another potential victim. However, if it finds any security weaknesses, the code begins to run malware on your device. Often, this involves sending a download file that automatically retrieves available malicious files from the web. The whole process is usually carried out without your knowledge and can be extremely tricky to pinpoint.
Adware
Adware is a form of software that hides on your device and continuously creates pop-up ads on its screen. Adware software can disguise itself as a legitimate program or be attached to a file you’ve downloaded on your device — meaning you don’t even know you’re installing it at all. Unfortunately, aside from being extremely annoying, adware is often used by hackers to collect personal information, such as your location, internet activity, and shopping habits. It can also act as a leverage to other cyber attacks, such as man-in-the-middle, which reroutes your online traffic through servers set up by attackers.
Spyware
As the name suggests, spyware is developed to spy on your device. Programed to go completely undetected, it collects vulnerable data, such as your bank account logins, credit card details, and phone numbers, to send it directly to its developers. This data can be collected through recording keystrokes, monitoring your online activity, and even stealing files from the affected device. Certain types of spyware can also modify your login details or even install additional malicious software without you realizing it.
Botnet
A botnet is a network of infected computers (bots) that can be controlled by hackers. While botnets aren’t malicious in nature, cybercriminals often utilize them to carry out more impactful attacks. That’s why botnets are usually used in DDoS attempts, phishing, and clickjacking.
Your machine can become a bot either by being directly hacked or by catching a “spider.” The latter is simply a program that autonomously crawls through the web searching for any vulnerability it can exploit. Once your device is connected to the hacker’s network, it sends a message to its owners to inform them about a successful task completion. Your infected device becomes a bot that’s completely dependent on what the botnet owner (also known as botmaster) chooses to do with it. However, you won’t be able to spot if you’ve been connected to a botnet as your device can be used as usual. It’ll only stop responding once the botmaster summons it and takes control over the system.
That’s not all — many botmasters don’t actually carry out any attacks themselves. They simply create multiple botnets and then put them up for sale. That way, any hacker who doesn’t want the hassle of creating and spreading viruses can use a ready-made network for their own purposes.
2. Phishing Attack
Phishing attacks are designed to collect as much of your personal data as possible through a range of deceptive methods. Attackers contact you, pretending to work at a legitimate company and encourage you to share your details, such as bank accounts and passwords. This information is then used to facilitate successful identity theft or fraud.
Although most people tend to think of phishing emails when talking about phishing — there are other methods you should be aware of.
Email Phishing
Email phishing is one of the easiest (and most dangerous) threats as it can be mass produced and sent to millions of victims at the same time — according to the Valimail report, at least 3.4 billion phishing emails are sent every single day. Using generic messages, attackers use various scare tactics that urge you to click on a link or a file attached in the email. However, doing so allows the scammers to effortlessly collect your sensitive information or infect your device with various types of malware for further data infiltration.
To carry out a successful email phishing attack, hackers need to register a domain and an email address that mimic an existing company. This can be done by substituting certain letters, for example using “r” and “n” (“rn”) together instead of “m”, or using the company’s name in the local part of an email address (such as amazon@registerdomain.com). This creates the illusion that the sender is in fact legitimate as many recipients don’t bother to thoroughly check where each email came from.
Vishing and Smishing
As consumers move from emails to instant forms of communication, hackers have adapted phishing methods to distribute scam messages through phone calls and text messages.
Vishing is a form of phishing done over a phone to persuade you to share your personal information, such as your home address, credit card numbers, or banking information. To appear trustworthy, the scammers often pose as financial experts or insurance and bank employees.
Smishing stands for “SMS phishing.” It works similarly to traditional phishing, but instead of sending convincing emails, attackers create fake text messages. These usually contain an urgent call to action that encourages you to click on attached links or approve malicious bank transfers. Sometimes, smishing can even be used to facilitate vishing by asking you to immediately call a phone number included in the text message.
Spear Phishing
Spear phishing is a type of email phishing that targets a very specific person or company. Unlike generic scams, spear phishing doesn’t focus on a large number of low-yield targets. These emails are sent with an intent to purposefully harm a chosen victim. It’s a lot more time-consuming as it usually requires in-depth research to be carried out prior to drafting and sending out highly personalized emails. The main aim of spear phishing is to encourage you to download malware and hand over data or financial information.
Whaling Attack
Whaling is even more specific than spear phishing as it targets senior executives and other important employees in various businesses. Also known as CEO fraud or scam, whaling requires each attacker to pose as another influential member within the same organization. Doing so adds elements of social engineering into the attack, as every target is more likely to follow the instructions in the email thinking it came from someone more important. Whaling attempts can be made even more believable if hackers utilize all available research resources, such as public social media profiles. The more information they can gather, the more trustworthy the whaling email will appear.
Even though whaling emails aren’t aimed directly at you, they are still a threat to your private data. That’s because the most common examples of whaling include phony requests related to payroll and tax returns. This provides scammers with a lot of important information about a company’s employees, including your financial status and social security number.
Angler Phishing
The growth of social media has enabled hackers to create a very specific scamming method called angler phishing. This approach involves attackers creating fake customer service accounts that appear to belong to actual companies. Scammers reach out to you by responding to your complaints about a product or a service posted on social media. They can quickly gain your trust by appearing genuine and friendly and then persuade you to click on malicious links or give sensitive personal information — often by promising a refund.
However, angler phishing doesn’t always involve actively reaching out to disgruntled customers online. Scammers can also use their faux social media accounts to lure you into visiting their websites. This is usually done by advertising fake competitions, selling nonexistent concert tickets, and many other similar tactics.
3. Cryptojacking
Cryptojacking (or cryptomining) describes an unapproved use of your computer, phone, or tablet to mine for cryptocurrency. Apart from compromising common gadgets, hackers can use singular web browsers that automatically embed a cryptomining code within your device.
Distributed like any other type of malware, cryptojacking code can easily load itself on an infected device as soon as you click on a malicious attachment or link. However, cryptojacking code doesn’t exploit or interact with your personal data on the infected machine in any way. Instead, its purpose is to run the code in the background whenever the machine is on, using all available resources, particularly the device’s CPU.
Some cryptomining programs have worming capabilities — meaning they possess certain features similar to a computer worm. This allows them to replicate and infect other machines and servers connected to your infected device. Worming software is also extremely difficult to recognize and delete, which ensures constant cryptomining on the same network.
Even though the main aim of most cryptomining attempts is to drain your device’s energy to steal online currency, it’s possible for hackers to utilize it as a backdoor into your system. As cryptomining kits can be easily bought on the Dark Web for as little as $30, they provide attackers with a much more affordable and time-saving method of breaking into vulnerable networks. This creates a bigger threat to your data because hackers can view, steal, modify, and even delete all of the files stored within your device as soon as they have access to it.
4. Cloud Attack
Hackers can access all files stored within your cloud account by utilizing its token login system. This authentication method requires all cloud providers to assign one token to your device when you first create your account and log in. This token then stores your login information which is read by the cloud whenever you want to access your storage space — without you having to enter your credentials every time. Unfortunately, this token can also be used to break into your account from anywhere in the world.
Your login token can be easily obtained and copied for future use by infiltrating your device with specific malware that’s distributed through phishing emails. Once downloaded, the malicious software syncs your account data with the hacker’s cloud profile. This tricks the cloud into providing the attacker with the same token allowing for unrestricted access to your online storage.
Cloud attacks are particularly dangerous as the collected data is often used for identity theft, fraud, or even blackmail. This is particularly true if attackers find any extremely private files that could compromise your reputation or personal relationships. Such data includes nude images, self-made pornographic videos, fraudulent documents, and many others. Should a hacker obtain this information, they may choose to duplicate it and demand you to pay incredibly high amounts of money. If you fail to deliver it on time, the stolen information is then sent to your family, friends, employers, and sometimes even published on social media or in the news.
Apart from eavesdropping, hackers can use your cloud account to store and deploy malicious files to any accounts linked with yours. This allows for attacks such as cryptomining and malware distribution on a much larger scale but with minimal effort required from the hacker.
5. Domain Name System (DNS) Tunneling
Handling over 100 billion internet requests every day, the Domain Name System translates human-friendly domain names, like www.wizcase.com, into computer-readable IP addresses. That way, you don’t have to remember all IP addresses yourself — DNS does it for you. However, cybercriminals also use DNS to hide malicious codes and bypass firewalls. DNS tunneling utilizes the Domain Name System to gather your personal data, such as passwords, login credentials, and location, by secretly communicating with your computer. This is done by uploading malicious commands and data into the DNS protocol your device uses to access any websites.
To perform a DNS tunneling attack, hackers register a domain name, like cyberattacker.com, and upload malicious code onto it. The IP to this faux site is then stored on its local DNS server. Hackers then distribute the link to their website through pop-up ads and phishing emails, encouraging you to click on it with an enticing message. However, every time you send a request to visit the fake platform, your traffic is rerouted through the attacker’s server. This redirection triggers the hacked server to automatically collect your sensitive information and send it directly to its owners.
6. Man-in-the-Middle (MitM) Attack
MitM attacks describe every situation when an attacker successfully gets in the middle of the connection between you and a website or application. Even though most internet traffic is now encrypted, the attacker can strip it of any protection once he or she is safely nestled within the open connection. This position allows the perpetrator to either silently observe or modify the online traffic. The aim of MitM attacks is to gather as much of your vulnerable data as possible, especially if you use online banking or fill in payment forms.
MitM attempts are usually done through a public WiFi connection where your internet connection is less secure and easier to infiltrate, like in cafes or restaurants. These attacks can also be performed by network spoofing — a technique that creates fake networks disguised as legitimate connections. Controlled entirely by a hacker, these networks use malicious programs that continuously listen and even manipulate all of your data that goes through them.
The threat is now especially real as your phone connects to an average of 2-3 public networks every day, according to Verizon’s Mobile Security 2020 Report. Almost 10% of those connections show at least one vulnerability that could allow even inexperienced hackers to eavesdrop on your online communication. This means that every time you use open internet connections to do work-related tasks or access personal accounts, your data has a high chance of being collected by hackers.
7. Cross-Site Scripting (XSS) Attack
If a website allows for your input, for example through comments or forums, hackers can easily upload malicious JavaScript code into it. So-called cross-site scripting (or XSS) compromises all interactions between you and a trusted web platform. Even though it’s executed within a company’s website, it’s only aim is to cause harm directly to you.
Uploaded JavaScript code is executed alongside the site’s code within your browser, giving attackers full control of your online communication on that site. The attack is designed for various purposes but is mainly used to transmit any of your vulnerable data that the site collects straight to the attacker. XSS attacks are now the most popular form of hacking and account for almost 40% of all cyber attacks, according to Precise Security.
Depending on how cross-site scripting attacks are executed, there are several different types of XSS attacks that you could fall victim to.
Reflected Attack
Reflected attacks describe XSS attempts where a URL that contains the malicious script bounces off of your web browser. Hackers use an existing webpage and attach JavaScript code to its URL that creates an entirely new address. That link is then sent to you with an enticing message that encourages you to click on it. At first, you land on the legitimate page that displays the 404 error message — only to be immediately redirected to the hacker’s site. This automatically allows for quick collection of your data or even unauthorized downloads of malicious files.
Stored Attack
Also recognized as persistent or second-order XSS, stored attacks happen when the malicious code becomes permanently embedded into the site’s internal code. As it’s written directly on the server, every user who visits the website automatically runs the hacked script and participates in the attack.
Due to their nature, stored attacks can fully compromise every part of your data. Since they’re fully contained within the affected web application, hackers don’t need to entice you to click on a reflected URL that contains the script. The malicious code simply runs itself as soon as it records a new visitor on the platform — making it a lot easier for the hackers to manage.
8. Password Cracking
Passwords cracking describes every active attempt at guessing your passwords stored within a website’s database. A cracked password can then be used to gain unauthorized access to your online account. As research shows that around 70% of users protect their profiles with the same password, hackers are often able to access multiple personal accounts by guessing just one of your passwords.
This attack can be performed by anyone, as it doesn’t require any sophisticated equipment or even specific knowledge. However, there are certain techniques attackers can choose from, depending on how fast they want to crack your account.
Brute Force Attack
Favored especially by novice hackers, a brute force attack uses a computer program that tests all possible password combinations until it finds an entry into your account. The software is run on a login page where, starting from the easiest passwords, it tries different combinations by swapping one letter after each unsuccessful attempt. Due to the incredibly large password library, brute force can take weeks or even months before cracking only one password — despite testing 100-1000 entries per minute.
Dictionary Network Attack
A more sophisticated method of password cracking involves employing a dictionary network attack. A dictionary network utilizes the most commonly used passwords that are more likely to succeed. Unlike brute force, a dictionary network bases its search on all words found in a dictionary instead of cracking passwords by swapping every letter. Additionally, dictionary network programs can combine capital letters and numbers in their search bringing a much higher possibility of succeeding a lot quicker.
9. Eavesdropping Attack
Otherwise known as sniffing or snooping, eavesdropping silently intercepts communications between your device and a server it’s connected to. Attackers use this technique to steal your valuable information, mainly financial data and login details. Even though data is collected in a similar way to MitM attacks, eavesdroppers use a very specific type of software installed somewhere within your network. This means hackers don’t have to actively look through all of your data that is being transferred in real time — instead they can retrieve vulnerable information after it’s gathered by the software.
However, eavesdropping software isn’t always used by cybercriminals — according to BBC News, stalkerware can also help concerned spouses spy on their partners. Installing spying apps on a desired device will automatically record your keystrokes, pictures and videos, screenshots, audio clips, ambient audio, messages, past and current location, and more. Research shows that in 2019 alone, cybersecurity companies detected over 37,500 devices with a spying program installed on it. This boost in popularity is believed to come from how widely available stalkerware has become, giving your partner an easy way to check how faithful you are.
10. Clickjacking
Click hijacking, commonly known as “clickjacking”, refers to tricking you into clicking on an unpredicted element within a website. To override the existing code within a platform, hackers create a transparent clickable layer that covers the whole webpage. That way, whenever you want to interact with any element on the infected site, instead of selecting the actionable content (such as a play button on a video), you click on the overlaying page. After triggering the malicious code, you quickly become a victim to various types of other attacks — from downloading malware on your devices to handing over all of your personal data.
11. Drive-By Download Attack
Drive-by downloads describe installing malicious files on your device without your authorization. Used to distribute all kinds of malware, drive-by attacks don’t require you to perform any kind of action — all you need to do is visit an infected website. Such attacks can enter your devices in two ways: without any consent or notification at all, or with consent that comes from a lack of full understanding of its implications.
These unintentional downloads are due to various vulnerabilities that affect even the most popular platforms. All hackers need to do is leverage those vulnerabilities to create a point of entry. Then, they can easily upload malicious PHP or HTTP code into the existing program, which automatically executes itself as soon as you open the site or app.
One of the biggest drive-by attacks took place in 2016 and affected multiple high-profile sites, like The New York Times, BBC, and the NFL. Hackers were able to compromise all these platforms by exploiting vulnerabilities within the ad networks used by the publishers. This meant the attackers were able to display malicious ads and redirect all traffic through malicious advertising servers. They infected tens of thousands of users with Trojans and ransomware before the affected sites were able to take the ads down.
12. AI-Powered Attack
With the rapid growth of Artificial Intelligence in everyday life, the threat of attackers using it against you and companies is also growing. Unlike human-powered malware, AI is able to adapt and learn extremely quickly. Programmed to not only find vulnerabilities in your system, but also to effectively choose and deploy malicious attacks, AI attacks allow for much faster system infiltration by cybercriminals.
AI-powered attacks are considered particularly dangerous because experts still can’t predict what the software could be programmed to do. Despite cybercriminals not utilizing it to its full potential, AI software has already been used to cause significant damage. The Emotet Trojan is one of the most popular AI-based phishing attacks that allowed for automatic creation and distribution of spam emails. However, unlike usual phishing emails, Emotet has the capability of inserting its message into already existing email threads. This tricked thousands of users into believing the email was actually sent as a reply from a legitimate company and downloading malicious files directly on their devices.
This is just one out of the few examples of how AI can be beneficial to hackers. Even though we don’t know the full extent of its possibilities, experts agree these attacks have the power to completely change how cybercrime works.
13. Internet of Things (IoT) Attack
The Internet of Things (IoT) is used to describe all devices that are connected to the internet and continuously share online data. This includes your home and office automation machines and smart appliances, such as lightbulbs that can be controlled from your phone, motion sensors, or even your child’s remote-controlled toy car.
The ease with which anyone can set up an IoT device has created huge gaps in networks’ security systems, allowing cybercriminals to perform around 5,200 IoT attacks per month. Hackers regularly scan whole networks looking for weak connections that can be turned into a point of entry. As IoT objects often don’t come with high cybersecurity settings, the lack of extensive protection allows hackers to break into any smart device connected to the internet. Once the attacker has access to any of your IoT appliances, he or she can then infiltrate your whole network searching for personal information, payment data, and more.

Cyber Attacks Directed at Companies
14. Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attack
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks prevent an affected site from functioning properly by sending multiple online requests at the same time. While DoS attacks are performed through a single internet connection, DDoS uses multiple connections at once. This allows hackers to send a much bigger volume of server requests causing significantly more long-term damage in a shorter period of time. Additionally, as DDoS attacks can be launched from various different locations across the world, they’re a lot more difficult to detect and stop.
The main aim of these attacks is to disrupt a company’s online servers or networks and make them fully or partially unresponsive to their clients. Once the website crashes, hackers can deploy further cyber attack methods to force entry into a company’s databases or to manipulate its entire system. This can allow them to easily collect and modify your personal data stored by the company. Experts predict that due to their ease of distribution and high disruption capabilities, these attacks are only going to grow in popularity, reaching 15.4 million by 2023.
15. Supply Chain Attack
Supply chain attacks penetrate and damage a company’s systems by using existing vulnerabilities in its supply chain network. These vulnerabilities are particularly common if certain suppliers or vendors linked to a targeted company don’t have appropriate cybersecurity methods applied. This allows attackers to leverage each weak point to infiltrate their targets by infecting the systems with malware. These malware programs are able to steal your credit card data, personal information, and even allow hackers to remotely control your whole system.
The latest trend in supply chain attacks involves targeting tech and software developers. That’s because by infiltrating their networks, hackers can upload malicious code directly into the devices and software updates, which are then distributed to millions of customers. Doing so allows cybercriminals to attack multiple victims at once without them ever realizing it. As the malicious code is recognized as a part of the program it’s in, it automatically gets the same device permissions.
As supply chain attacks allow cybercriminals to affect multiple companies with minimal effort, these attacks increased by 78% in 2019. Experts agree that hackers are going to abuse weak points in supply chain networks with an increasing interest in the years to come.
16. Formjacking
Sometimes cybercriminals focus specifically on attacking e-commerce websites to collect your payment details — this is known as “formjacking”. It happens when hackers inject malicious JavaScript code into a retail site in order to capture all of the personal data you provided through a payment form. That way every time you enter all information required to make a purchase, such as a full name and credit card number, the code instantly transfers it to the attacker. At the same time, it processes the transaction to make sure you don’t realize your data was stolen. The gathered information can then be sold on the Dark Web or used for identity theft and fraud.
Formjacking is steadily on the rise due to the increased interest in online shopping. The 2020 Symantec Internet Threat Security Report shows that almost 8,000 e-commerce websites had their platform infected with malicious JavaScript code. That’s almost 2 times more compared to the findings from the company’s 2019 research. Experts agree that this escalation is related to the ease and profitability of each formjacking attack. As even just 10 stolen credit card numbers can bring in over $2 million profit, it isn’t surprising that more hackers are showing interest in creating malicious JavaScript codes.
What’s more, formjacking attempts are almost impossible to spot. The affected website doesn’t display any signs of infection — it still displays secure HTTPS code, the form looks exactly the same, and each transaction is processed as usual. To detect the attack, a cybersecurity expert needs to know specifically what to look for within the website’s code. However, formjacking targets are mainly small and medium-sized businesses that often don’t have appropriate digital security methods, like firewalls or a skilled IT specialist, in place. This allows cybercriminals to passively collect your payment details for long periods of time without raising any suspicions.
17. Zero-Day Exploit
A zero-day exploit takes place when hackers learn about a system vulnerability before or on the day it’s reported to its vendor. The ‘zero-day’ part of the name refers to how long the developer has been aware of the fault in the software. This threat is particularly dangerous as the unreported vulnerability exploitation can stay hidden for months allowing unlimited data collection.
Zero-day attacks pose a direct threat to you as a private user because the system vulnerability can be used to break into your personal device and either install malicious software on it or connect it to an existing botnet. From there, hackers can take full control over your computer and collect private data, record keystrokes, or even completely lock you out of the system to demand a ransom.
Cybercriminals can also learn about vulnerabilities through regularly checking forums or social media sites. That’s because it’s often the users who discover security issues within programs they use. Users then report the issue to the vendor and immediately after, share their discovery with other users online. However, doing so not only warns others about the vulnerability but also informs hackers about possible ways into a company’s system. Finding security weak points through social media means attackers don’t have to waste their time actively looking for them.
18. SQL Injection
SQL injection uses the most popular database programming language (SQL) to easily manipulate and steal any of your data that is stored within a database. Attackers utilize this code to create malicious SQL statements and input them into login forms or search bars on an unsecured website. As the code prompts the site to ignore existing commands, it automatically displays your private information by giving attackers full access to affected databases. Through infiltrating the database, hackers can run multiple requests that allow them to read, upload, modify, or delete your data. SQL attacks are not only used to steal your personal credentials, but also to transfer bank funds, or even gain access to a company’s whole operating system.
According to Edgescan’s 2020 Vulnerability Statistics Report, SQL injections accounted for over 40% of common critical vulnerabilities within all web applications. This means that almost half of the online platforms you access don’t have appropriate database protection methods to shield your private information from outsiders. As it’s impossible to spot such vulnerabilities as a regular user, you can never know if the data you share with a business is at risk of falling into the wrong hands.
19. Insider Attack
According to Verizon’s 2020 report, around 30% of all cyber attacks come from an insider, such as an employee or a close friend. Anyone who has, or used to have, an insider’s knowledge of how a system or a network works and how to access it, automatically becomes a potential cyber threat. That’s because it gives them the capabilities to perform any type of attack and steal valuable data. Insider attacks most commonly happen in companies, but it’s not impossible for private users to become involved as well.
Insider threats are particularly dangerous as they’re a lot more difficult to prevent, even with the toughest cybersecurity measures in place. As the insider already has the necessary details to access a company’s systems, they can easily bypass many verification processes with their login credentials. The aim of an insider attack differs between all actors, but it’s mainly executed to steal and sell your personal information for financial gain or move your data across to a competitive company.
20. Targeted Attack
Targeted attacks refer to any cybercrime that requires hackers to actively pursue a specific victim. While these attacks combine multiple malicious methods mentioned in this list, they’re often conducted in a series of smaller attempts that allow hackers to get deeper inside your system. Spear phishing, whaling attacks, malware downloads, and cloud attacks are the most common forms of targeted cyber threats.
To hack a chosen target, attackers must possess a sufficient amount of resources and a certain level of expertise that can be used to plan their next steps. As the attacks take significantly longer before hackers can enjoy the benefits, they usually target highly-important companies and government agencies. However, hackers can be hired to perform a specific attack directly on you. Attacking specific targets is linked with various motivations, such as a political movement, financial gain, data theft, or as a form of personal revenge.
4 Types of Cybersecurity Vulnerabilities to Watch Out For
A cybersecurity vulnerability is a flaw in your device or a website’s security system that can be used by hackers to damage or manipulate the data stored on it. Though every vulnerability can be leveraged by cybercriminals to enter your network, security flaws exist because of software or app misconfigurations. Unfortunately, they can be extremely difficult to identify, even by specialists, due to the high complexity of computer networks.
The nature of each vulnerability determines the approach a hacker needs to take to exploit it. Luckily, you can easily reduce the possibility of experiencing a cyber attack by knowing where to look for them. Security weak spots can be divided into 4 main categories based on where and how they occur:
- Network errors are problems like unsecured or weak internet connections, or misconfigured firewalls. These cause hardware and software vulnerabilities and can be leveraged by hackers to create an entry into your system in order to infect it with malware.
- Process vulnerabilities are a result of disregarding the importance of specific process controls, like setting up weak passwords or insecure login credentials. As they can be easily cracked in brute force or dictionary attacks, hackers can break into any of your personal accounts and collect all of your data.
- Operating system issues arise after installing a software upgrade that was released with unpatched code errors. These weak points are often utilized in zero-day attacks to infiltrate your system before the vulnerability is fixed by the vendor.
- Human mistakes are any instance where a person unintentionally gives bad actors an entry to a network or leaks sensitive data themselves. This includes accidentally sharing internal login details, becoming a phishing victim, or even leaving your device unattended in a public space. These errors are the most common reasons behind a hacker attack as they’re very common and easy to utilize to compromise your system or steal your personal information.
Even though you can’t always prevent these vulnerabilities from happening, there are certain protective methods you can utilize to ensure they won’t be used as an entry into your system. These precautionary steps are extremely easy to apply in your everyday life and often won’t even require you to purchase any overpriced software.
Protect Your Devices With These 12 Cybersecurity Tips
Recognizing different types of cyber attacks is just the first step towards creating a more secure online space. While all of the possible threats may make you want to quit using the internet altogether, that isn’t the only way you can protect yourself. Even though you can’t stop all cybercrime from happening, you can make it a lot more difficult for hackers to break into your devices.

While these preventive methods are a necessity to stay safe online, an additional layer of protection will massively lower your chances of sharing your data with hackers. By installing just one form of a detection tool, you’ll allow regular monitoring on your device and continuously scan all vulnerable files. Your chosen software can also alert you every time your device is under attack and advise the best course of action to remove malicious files and programs from your system.
The 4 Types of Detection Tools You Should Be Investing In
Due to the constant evolution of cyber threats, it’s getting increasingly difficult to detect if you’ve become a victim of a hacking attack. This risk can be significantly lowered by investing in at least one type of detection tool. Detection tools were developed to not only secure your internet traffic to the maximum, but also find and fix any vulnerabilities that may exist within your network. Additionally, these programs can also quickly pinpoint if your device was linked with a hacker’s computer and remove that connection straight away.

Encryption Tools
Encrypting your internet traffic immediately turns it into encoded packets of data that can only be deciphered by authorized people. This means that when you send a text message to your friend, the encryption software transforms the message into a set of meaningless characters until it reaches the receiver. This way hackers cannot easily intercept your online communication without expensive decryption tools and a lot of spare time.
Data encryption can also be used on all of your devices and internet browsers, not just instant messaging systems. The 2020 Global Encryption Study by Ponemon Institute shows that almost 90% of companies and private users are now relying on encryption to protect their information. This is particularly true if you use the cloud, as cloud-based encryption showed an increase of 21% just within the last 4 years. This is mainly due to the fact that encryption tools, like BitLocker or FileVault2, encrypt your traffic with one click of a button and massively boost your cybersecurity.
Malware Sandboxes
Sandbox environments provide a safe environment within your device that lets you check if downloaded files contain any form of malicious code. Malware sandboxes, like Any Run, detect and delete malicious activity by observing how the executed code behaves within the environment. Installing and executing the files within the isolated space doesn’t actually infect your device with malware — it’ll be kept in the sandbox at all times until it’s safely removed.
Network Monitoring Software
If you’re not sure where to look for any vulnerabilities on your devices, network monitoring software can find them for you. Enabling such tools on your digital devices will consistently scan their networks for anomalies and slow or broken components. As soon as a weak point is found, the software alerts you by email, text message, or notification. It often also suggests the right course of action needed to secure the fault in a quick and effective way.
Many network monitoring tools, like Nagios Core, cover a range of devices and servers that use the same network. This includes routers and home appliances as well as email or application servers. Monitoring software can also scan links and connections between the devices and servers. All these features work towards finding even the smallest fault in the objects themselves and in the way they communicate with one another.
Cyber Threat Intelligence (CTI)
Cyber threat intelligence uses a global database of cybersecurity methods to locate and remove any malicious activity within a network. These programs continuously analyze data about existing and emerging threats, such as malicious IP addresses, faux networks created by hackers, and any ongoing attacks. As they’re always connected to the cybersecurity database, CTI tools (such as IBM X-Force Exchange or LookingGlass Cyber Solutions) help companies and private users understand how their networks could be compromised.
Don’t Wait to Become a Victim — Protect Yourself Now!
To effectively protect yourself against cybercrime, you must first understand where the danger could come from. Hackers employ a range of techniques, including setting digital traps to trick numerous users into targeting specific victims, in order to infiltrate your system and take control of your life.
Luckily, with the right prevention methods, you can become a much more difficult target to hack. Remember to keep your system up to date, avoid using public and unsecured connections, and consider downloading reliable antivirus and detection software.




Leave a Comment
Cancel