Data Leaks in the Medical Industry: The Problem Continues
After our previous report on database leaks from medical websites around the world, WizCase’s security team diligently continued their research. They discovered 3 additional unsecured medical databases with confidential information, including full names, passport numbers, birth dates, addresses, and phone numbers.
These databases were found in the context of performing research to help companies secure their data. They were left unencrypted and required no password to access the sensitive information within.
Every company and their hosting provider has been contacted with the security team’s findings. Our goal is to inform them of the leaks so they can secure the exposed servers, protecting their patients’ private information. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
Latest Breaches Found (January 2020)
- HX Wellness Private Limited (Aermed Online Pharmacy App) — India — Approx. 230,000 records exposed, leaking both patient and doctor information.
- Mobile Health Pte Ltd (MaNaDr Mobile Health) — Singapore — Approx. 842,000 records discovered, exposing patient and doctor details.
- Zaldivar Institute — Argentina — Approx. 8,600 records found, leaking ophthalmic patient data.
What’s Happening in the Medical Industry?
You trust companies in the health industry to keep your private data completely secure. But with how quickly technology is advancing, security measures are having a hard time keeping up. It’s a concern since your medical records contain some of your most personal information.
Following our initial article, our web security team at WizCase, led by Avishai Efrat, made several more alarming discoveries. 3 unsecured medical databases were found from companies in India, Singapore, and Argentina.
Some of the personal data we found includes:
- Patient — full names, addresses, phone numbers, birth dates, email addresses, ID and passport numbers.
- Information about doctors and confidential company data
- Scans of prescriptions given to patients
- Medical information — exposed information about appointments, possible surgeries, lab tests, patient medical status, and more.
What Medical Data Got Leaked?
Our team found 3 more unsecured servers, bringing the total to 12.

The 3 leaks in this report were found in Argentina, India, and Singapore.
You can read more about the previous data leaks in our comprehensive report.
1. HX Wellness Private Limited (Aermed App) — Online Pharmacy
- Country: India
- Database Size: 4 GB
- Exposed Records: ~ 230,000
- Whose Data Leaked: Patients and doctors
- Server Type: MongoDB server and Amazon AWS S3 bucket

HX Wellness Private Limited is a start-up company in India that allows its users to order a range of medicines and lab tests online through its Aermed app. The company seems to serve only patients who are based in India.
The exposed server was hosted in Singapore. The data leaked contained sensitive patient details including full names, age, location, email, gender, medical records, order information, and prescription information. Patients’ medical scans could also be accessed without authentication from the exposed Amazon bucket. Full names, emails, and phone numbers of doctors can also be found associated with patient information.
2. Mobile Health Pte (MaNaDr Mobile Health) — Doctor Consultation App
- Country: Singapore
- Database Size: 578 MB
- Exposed Records: ~ 842,000
- Whose Data Leaked: Patients
- Server Type: ElasticSearch server
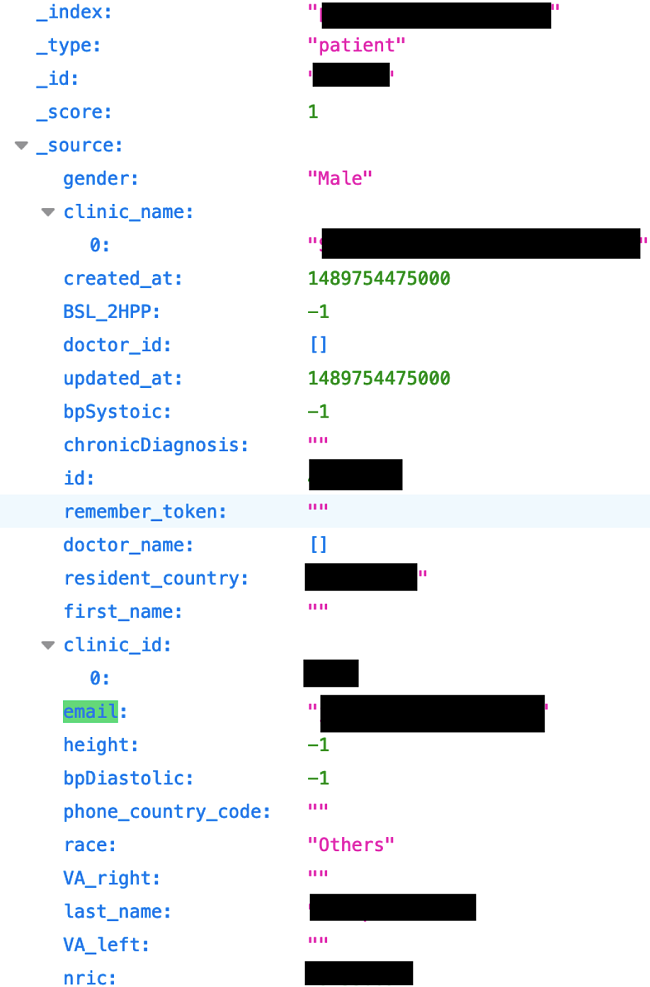
Mobile Health Pte is a company based in Singapore that owns MaNaDr — a healthcare app that lets patients consult with doctors, book appointments and home visits, and get test results directly on their smartphones. Patients seem to mostly be in Singapore, but the app is also used in Australia.
The unsecured server was hosted in the US. Leaked data includes confidential patient data, like full names, addresses, NRIC (Singapore’s ID number), phone numbers, and birth dates. Information about appointments was found, including patient ID numbers, and medical information such as lab test results. Doctor’s names, clinics, and lab details were also found.
In our correspondence with MaNaDr, we found they had closed the leak. They told us the exposed data was not real patient data, but test data used for demo purposes. However, we have been unable to verify this claim. We always randomly check records when we investigate leaked databases — we found some records that appear to be legitimate patient data.
3. Zaldivar Institute — Ophthalmological Treatment Center
- Country: Argentina
- Database Size: 72 MB
- Exposed Records: ~ 8,600
- Whose Data Leaked: Patients
- Server Type: ElasticSearch server
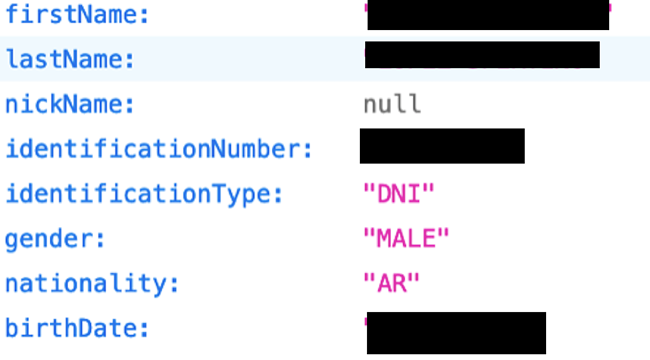
The Zaldivar Institute is an ophthalmic center in Argentina with over 60 years of experience performing innovative eye surgeries and treatments. The institute seems to treat mostly local patients — with worldwide recognition, it’s likely patients are also from other countries.
The two exposed servers were hosted in the US, holding more or less identical information. The data found on the servers had confidential patient information, including full names, Argentinian ID and passport numbers, emails, phone numbers, general details of professions, birth dates, nationality, and addresses. Thousands of medical entries were also found with information regarding appointments and possible surgeries.
Medical Data Leaks: What are the Consequences?
Medical data leaks not only expose your confidential data in a huge invasion of privacy — they also make it possible for hackers and scammers to get your information.
Identity Theft
This is a huge risk with databases that hold complete PII (Personally Identifiable Information) records. Should a scammer get a government ID number (like an SSN), full name, address, and date of birth, it’s easy for them to steal your identity.
Phishing and Phone Scams
These scams rely on appearing credible and your belief that your information is secure. Once a scammer has your contact details, they can use your leaked PII to convince you to click on a suspicious link or give up even more information over the phone.
Skilled scammers deliberately target more vulnerable individuals — those who will believe an authentic-looking email or phone call from someone with information about their condition, the clinic they attend, or the treatment they receive.
Blackmail
Patients who want to keep their medications or treatment secret can be blackmailed as a result of data leaks. Scammers know that revealing certain information could cost the patient their financial security or even their family life.
Fraud
Scammers can use information like unedited scans of prescriptions and reproduce them for fraudulent purposes. They could also use the PII details they took from the leak to pretend to be a patient and commit fraud.
What Does This Mean for the Data Leak Victims?
The following shows one example of risk per leak, though there are more:
HX Wellness Private Limited — Blackmail
Medical observations like scans and lab results and prescription details from the exposed server could be used to blackmail patients — the number of records that were leaked gives a scammer a huge pool of potential victims.
Mobile Health Pte — Phone Scams
A huge number of patients had their phone numbers leaked. Patient IDs were also leaked, along with information about treatments and test results. Patient IDs can be linked to individuals and the data used to establish trust over the phone, persuading vulnerable patients to hand over even more information.
Zaldivar Institute — Fraud and Identity Theft
Leaked information included personal identification numbers (DNI — Argentinian identification numbers and passport numbers) and full names, making these victims prime targets for having their identities stolen and used fraudulently.
2 More Ways to Keep Your Private Information Secure
It’s hard to guarantee that your information will always be kept safe, especially if it’s shared with third-party companies. It’s important to stay vigilant by consistently monitoring your online accounts. Follow the 2 recommendations below as well as the advice from our previous report to keep your personal data as secure as possible.
1. Encrypt Your Data Online
When you’re sharing sensitive information on a website or app, ensure the connection is encrypted and secure. Check the website URL for “HTTPS” as this ensures your online communication is encrypted and guarantees the integrity of the site. You can also use a VPN to encrypt all of your internet traffic — using both together makes it extremely difficult for third-parties or hackers to access your personal data while it’s in transit.
2. Limit the Information You Share on Social Media
If a breach occurs and a scammer gets hold of your information, there’s a chance they could use it to try and find you through your social media accounts. Keep your accounts private, only add people you know, and don’t overshare.
Who is WizCase?
WizCase leads the cybersecurity sector. Our committed web security team strives to ensure that any discovered leaks are reported to the relevant company. This allows the company to seal the breach and maintain the safety of user data.
Securing the data isn’t always an easy task as the companies involved tend to disregard our warnings. While we were working on this research, we reached out to Dissent Doe, who helped make sure the data was secured.
From breaches in the hospitality industry to dating apps and exposing vulnerable webcams, our research team reports the news to the public so we can all enjoy a more secure digital life.




Leave a Comment
Cancel