Data Leaks in the Medical Industry: A Worldwide Epidemic
Update: The WizCase cybersecurity team has since uncovered 3 new data breaches in the medical industry. For more information, read our new report.
WizCase recently found database leaks from several different medical websites from around the world — leaks included personal prescriptions, medical observations, lab visits, Social Security Numbers, and in many cases, full names and addresses.
The following databases were found in the context of our research to help companies secure their data. They were all unsecured and didn’t require a password to be accessed, leaving millions of patients’ data vulnerable.
We have contacted all of the companies, their hosting provider, and in some cases the local authorities but there are still unsecured databases. We hope that after publishing this exposé they will have no choice but to secure the database and protect their customers/patients’ privacy.
What’s Happening in the Medical Industry?
Technology is moving at a fast pace and many security systems can’t keep up. This is especially concerning when you trust a company that is supposed to protect your sensitive user data. The health industry is no exception, as companies share data with third-party providers around the world.
Personal medical data should be kept private. However, we’ve found several leaks that raise serious questions about how our medical data is handled and secured today.
Our web security team, led by Avishai Efrat, found 9 unsecured medical databases from around the world. Some of these databases are from third-party companies that provide data management and insight for medical institutions. Unfortunately, they might not understand the possible implications of handling sensitive data insecurely online.
Some of the personal data that we found included:
- Patient data (includes full name, address, social security number, email address, and phone number)
- Company data (personal information of employees)
- Research-related data
- Medical observations
- Prescriptions
What Medical Data Got Leaked?
Our team found servers for 9 medical companies around the world.
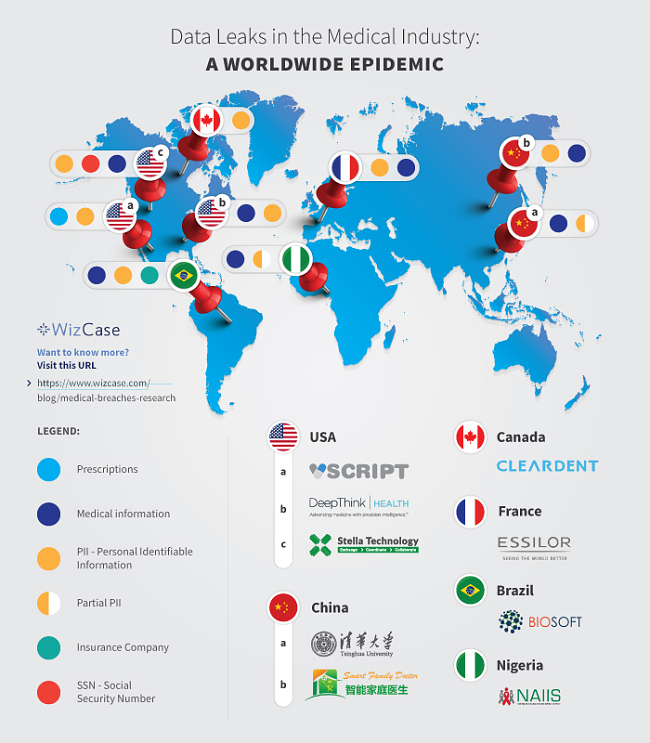
1. CadClin from Biosoft — Medical Software
- Country: Brazil
- Database Size: 3 GB
- Exposed Records: ~1,185,000
- Whose Leaked Data: Patients
- Server Type: Open Elasticsearch server and Kibana interface
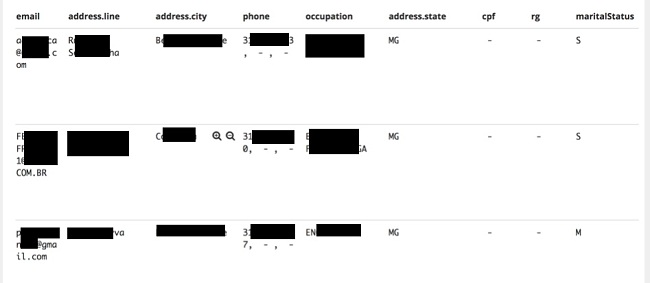
Biosoft is a software company specializing in developing and distributing programs for the medical market, to be used in medical clinics and laboratories.
This specific leak involves CadClin, one of their products, which is an Electronic Patient Record software & calendar.
The data that was found included the patients’ full name, email, different medical observations (in Portuguese), date-of-birth, city of birth, RG (Brazilian ID number), taxpayer registry ID number, insurance company name, and occupation.
2. ClearDent — Dental Software
- Country: Canada
- Database Size: 8 MB
- Exposed Records: ~60,000
- Whose Data Leaked: Patients
- Server Type: Open Elasticsearch server
ClearDent develops programs geared for the dental market, such as patient management software, data insights and more.
The data leak included full names and phone numbers from patients in dental clinics using the company’s products, and also some entries with test data or missing values.
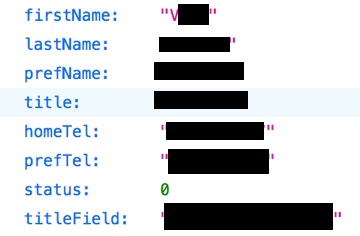
3. Jintel Health (renamed DeepThink Health) — Medical Intelligence as a Service
- Country: USA
- Database Size: 2.7 GB
- Exposed Records: ~ 700,000
- Whose Data Leaked: Patients’ Medical Data and Medical Personnel PII’s
- Server Type: Open Elasticsearch server
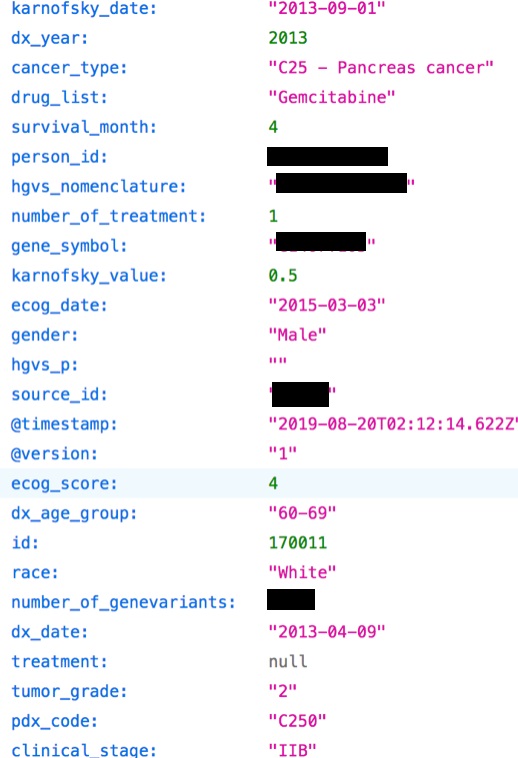
Deep Think Health provides a platform for analytics and machine learning insights for the medical market.
We found three types of data in this leak:
- Medical observations about anonymous cancer patients, including tumor size, cancer type, survival months, gender and age group
- Cancer treatment information, like drug lists and treatment types
- Medical personnel data, including names, physical addresses, and phone numbers
4. Essilor — Ophthalmic Optics Company
- Country: France
- Database Size: 5.7 GB
- Exposed Records: ~ 1,500
- Whose Data Leaked: Patients and Essilor Employees
- Server Type: Open MongoDB server
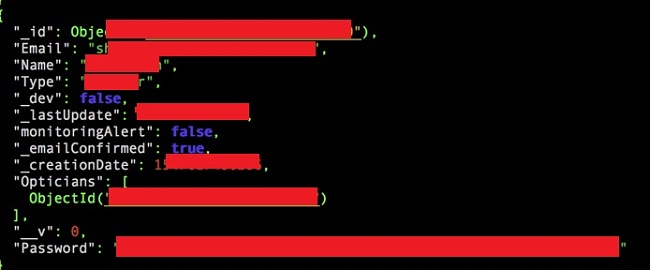
Essilor is a worldwide company that researches, designs, manufactures and distributes eyeglasses and related products.
This specific leak involved data about a specific product called Essibox, which is a management server used with the lenses finishing products that Essilor also offers.
The data leak included:
- Optometrist observations for approximately 1,500 anonymous patients
- Full names and email addresses for 200-300 accounts connected with different Essilor domains (such as @essilorindia.com or @essilorinstrumentsusa.com)
- Hashed passwords for Essilor employees
5. Naiis — Medical Cross-Sectional Survey
- Country: Nigeria
- Database Size: 1 GB
- Exposed Records: ~ 80,000
- Whose Data Leaked: People who took the survey
- Server Type: Open MongoDB server
Nigeria HIV/AIDS Indicator and Impact Survey (NAIIS) assessed in 2018 the prevalence of key HIV-related health indicators.
The data leak included facility and hospital names; patients’ pregnancy status; laboratory results code and value; patients’ age; HIV validation first test date and time; HIV encounter data; medical observations of anonymous people taking the survey; etc.
This survey was made of 88,775 randomly-selected households in Nigeria, counting approximately 168,100 participants, ages 15-64 years and children, ages 0-14 years.
6. Stella Prism by Stella Technology — Healthcare Big Data Platform
- Country: USA
- Database Size: 4 GB
- Exposed Records: ~ 300,000
- Whose Data Leaked: Patients
- Server Type: Open Elasticsearch server

Stella Technology is a company that has developed several applications and software products for the health industry.
This specific leak involved a product called Stella Prism, which is a big data platform for healthcare analysis. The data leak included full names, address, SSN for the US patients, admittance reason, address, date of birth, gender, medical observations, and emails. Not all records were unique.
In our correspondence with Stella Technology, they claimed that the data was not actual patient information, but rather used for demo purposes. However, we were unable to verify that claim. While investigating databases we always randomly check records, and in this case, two records appeared to be legit.
7. Tsinghua University Clinical Medical College
- Country: China
- Database Size: 643 MB
- Exposed Records: ~60,000
- Whose Data Leaked: Patients
- Server Type: Open Elasticsearch server
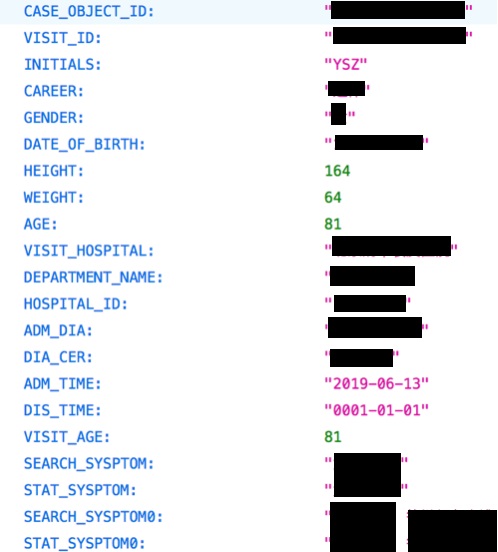
Tsinghua University is one of the leading universities in China. This specific leak involved data from a clinical research database which is maintained by the university’s medical school.
This clinical research database’s leak included details about patients from the medical school and the university hospital, as well as from other hospitals in China.
The database included patient information such as date of birth, age, height, medical information, and medical observations. However, there are no identifiable PIIs to specific people, besides their first and last initials.
8. VScript — Pharmacy Software
- Country: US
- Elasticsearch Database Size: 81 MB
- Elasticsearch Exposed Records: ~800
- GoogleAPI Bucket Exposed Data: 1,000s images of prescriptions and medicine bottles
- Whose Data Leaked: Customers of pharmacies using VScript
- Server Type: Open Elasticsearch server and GoogleAPI Bucket

VScript is a software company specializing in pharmacy-related software.
The database had a few dozen entries, including payment transactions of clients purchasing medical items with full names, masked credit cards, and drug prescriptions.
Information about the presence of the GoogleAPI bucket appeared in the Elasticsearch database itself. Anyone who found the Elasticsearch could then access the bucket without any restrictions and see thousands of photos of drug prescriptions and medicine bottles with full names, addresses, phones, and date of birth.
9. Sichuan Lianhao Technology Group Co., Ltd (四川联颐科技集团有限公司-) — Mobile Health Medical Platform
- Country: China
- Database Size: 42 GB
- Exposed Records: ~ 24,000,000
- Whose Data Leaked: Patients and Doctors
- Server Type: Elasticsearch Database

Sichuan Lianhao Technology Group is a hi-tech company that builds remote medical solutions using IoT devices.
This specific leak was connected with its “Smart Family Doctor” app. It allows patients to run tests such as pulse and heart rate, glucose monitoring, BMI, weight, blood count information and more from home.
The data came from a variety of sources including hospitals, pharmacies, doctors, and patients and included patients’ and doctors’ names, medical status, ID number, and phone numbers.
What are the Consequences of Medical Data Leaks?
Most patients aren’t likely to be aware that the above companies hold their data. This is because these companies are third-party providers. For example, if you bought a prescription in New York, you probably don’t realize that Vscript has your personal information on record.
But the threat is still very real. In fact, the ClearDent Elasticsearch server also included a ransom note. It’s important to note that ransom notes are often automatic methods used to attack open databases. This means that hackers or scammers could have already accessed or taken the data.

In addition to an invasion of privacy, there are several dangers that could occur should a scammer or hacker obtain the data exposed in the medical breaches:
Identity Theft
This is a bigger risk with databases holding complete PIIs, including SSN. Once a scammer has a SSN, complete name, address, and birthdate, they can easily steal your identity.
Phishing Scams
Since many of these leaks included an email address and some PIIs, a skilled scammer had enough information to write a believable email with a harmful link in it. Whether they reference the type of medication you’re on, the hospital you’re visiting, or the disease you’re suffering from, it would instantly be seen as credible due to the belief of privacy.
Phone Scams
Much like email phishing scams, once a skilled scammer has your phone number and enough private information, they can devise a credible scam to take advantage of unsuspecting victims. They especially seek out sick and vulnerable “marks”, because they are more likely to believe a caller with some details about their condition. These medical leaks gave the scammers an entire database of targets to victimize.
Blackmail
Scammers can use personal information from the data leak to blackmail patients who want to keep their illness or medication a secret. Revealing it could threaten their jobs, family life, and financial security.
Fraud
Scammers can use the information they collected, such as unedited photos of drug prescriptions, and reproduce the details for fraudulent activities. They can also pretend to be one of the patients in the database and use the leaked information to commit fraud.
What Does This Mean for the Data Leak Victims?
The following is just one example of risk per leak, although there can be more.
Biosoft — Identity Theft
Government-issued ID numbers with full PIIs and private details have been left in the open here. Consequently, this makes it significantly easier for identity thieves to target anyone included in the leak.
ClearDent — Phone Scams
Full names and phone numbers of dental clinic patients contained in the breach would be valuable in the hands of phone scammers.
Deep Think Health — Blackmail
Detailed cancer treatment and medical observations, even though anonymous, could potentially be used for blackmail if more data elsewhere in the system was revealed and correlated with the exposed entries from this leak.
Essilor — Phishing Scams
Email addresses included in the breaches could be targeted as potential access points in attacking individuals and the organization itself with different kinds of phishing and malware attacks.
NAIIS & Tsinghua University — Blackmail
Even though the data we found there was anonymous, the risk of correlating it with additional information from within or outside these databases, and so exposing people and their medical conditions, still exists. The large amount and high sensitivity of the data itself make the exposed population a potential target for blackmail.
Stella Technology — Identify Theft
PIIs (including SSN numbers), medical observations and private information have been leaked. Taking advantage of the exposed patient details to commit fraudulent activity is another associated risk with a data leak of this nature; it could readily be used to confirm individual identity with various companies and other establishments.
VScript — Fraud
Information about different pharmacies’ internal documentation of prescriptions and medicine bottles has been exposed, assisting potential medical document fraud.
Sichuan Lianhao — Blackmail
The vast amount of medical information and PIIs included in this leak, some of which is documented in great detail, could be a plethora of useful and sensitive health-related information used to blackmail vulnerable patients.
As you can see, leaks such as these show what little control people actually have over their personal data. Whether the data is shared with a third party for marketing purposes or for medical research — once it leaves your medical provider, it becomes less secure.
4 Steps to Securing Your Private Information
Unfortunately, it’s difficult to know whether your private information was shared with any of these third-party providers. However, there are some rules you can follow to secure your data and prevent leaks in the future.
1. Never Click on Links Sent via Email
Even if it appears to come from a reputable medical site — unless you’re sure who the sender is. If you’re not 100% sure, call the company and ask if they sent you the link. If you don’t recognize the email address or if the format looks weird, you should be suspicious (and don’t click blindly!).
Even if you recognize the email address, make sure the person hasn’t been hacked by checking with them directly if they actually sent the email. You can check the link using online tools such as Google Safe Browsing, VirusTotal.com, and URLscan.io.
2. Don’t Give Personal Information Over the Phone
Never give any kind of personal information to someone you don’t know personally or who isn’t clearly identifiable. This includes passwords or insurance information. Banks, payment providers like PayPal, and similar financial institutions should never call and ask for personal details.
If you’re unsure, you can double-check the caller ID, call the caller’s company to verify their identity, and check the caller’s phone number online and see if the company’s name appears. Be suspicious of anyone asking for your personal information.
3. Monitor Your Accounts for Unusual Activity
It’s best practice to create a secure password and use a password manager for extra protection.
4. Always Opt-Out of Data Sharing
Depending on the service, you may have to search for this option or explicitly ask to opt-out. It depends on the company’s privacy statement. You can go to simpleoptout.com and similar sites, which details the opt-out policy for many different sites.
Who is WizCase?
WizCase is a leader in the cybersecurity industry. Our web security team has found leaks in the hospitality industry, online dating apps, webcams, and more.
Our team ensures to notify the companies about the leaks prior to publishing the leak details. This allows them to safeguard their database and user data.
Securing the data isn’t always an easy task as the companies tend to disregard our warnings. While working on this research, we reached out to Dissent Doe, who helped ensure the data was secured.




Leave a Comment
Cancel