How to Access the Dark Web Safely: A 2025 Beginner’s Guide
Accessing the dark web isn’t 100% safe, even if you use Tor. Your ISP can still see your activity and may report it. It’s monitored because the dark web is linked to illegal activities like drug trafficking, weapon sales, and data breaches. Plus, it’s a known location for cybercriminals who want to steal data and jeopardize your device’s security.
There are a few ways you can boost security when using the dark web: making sure Tor settings are optimized, only visiting trusted sites, and using a VPN all help improve privacy. Of all the options I looked at, a VPN is the best way to access the dark web safely.
VPNs are easy to use and encrypt your connections to ensure your activity can’t be traced back to you — your ISP won’t even know you’re accessing the dark web. A service like ExpressVPN is a great choice, with premium security features and fast connection speeds. Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Safely access the dark web with ExpressVPN
Quick Guide: How to Access the Dark Web Safely in 3 Easy Steps
- Get a trustworthy VPN. With top-tier security and privacy features, plus fast speeds to mitigate slow Tor connections, ExpressVPN is the best option for the dark web.
- Download the Tor browser. Visit the Tor download page and select your device. Once it’s downloaded, you can configure the browser or connect immediately.
- Explore the dark web! Connect to a local VPN server and then open Tor to ensure you have maximum security on the dark web.
What Is the Dark Web?
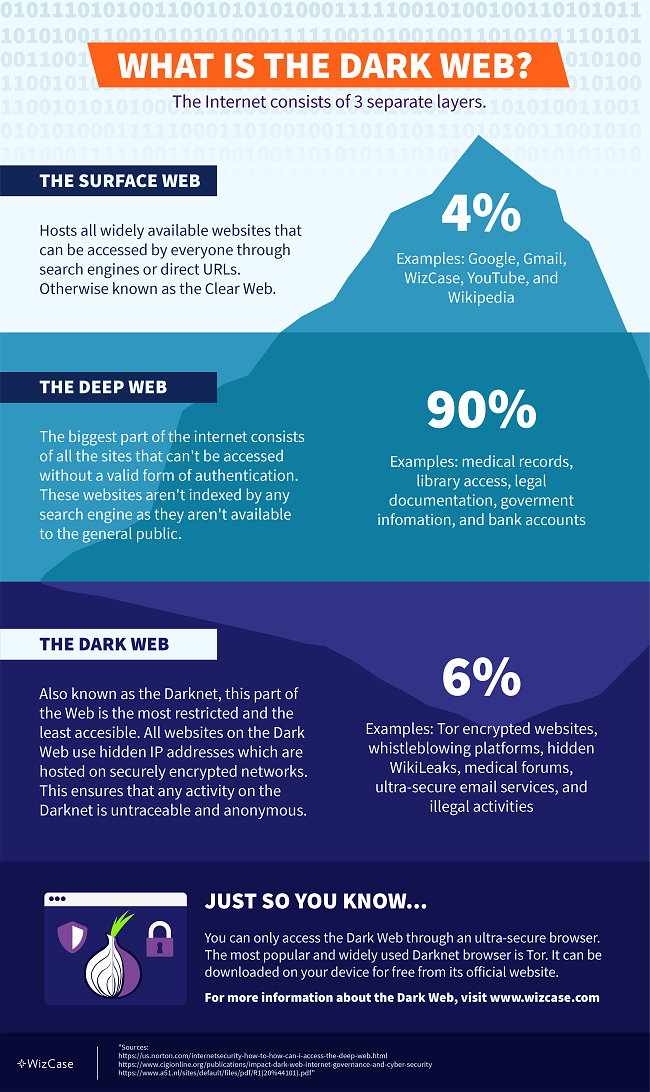
The internet consists of 3 layers: the surface web (or clear web), the deep web, and the dark web.
The Surface Web
The surface web, or clear web, is part of the internet we use every day. It includes news websites, social media, and online shops like Amazon — sites that we can browse directly, without logging in.
The Deep Web
The deep web includes websites that are not open to the public. You need a special link or password to access the sites, as search engines like Google can’t find them. The deep web stores private content like emails, subscription services, and company websites with sensitive data (like medical or financial information).
The Dark Web
The dark web is part of the deep web that isn’t easily accessible. You can’t browse it just by logging in because dark web sites use hidden IP addresses hosted in encrypted networks — dark web activity is fully anonymous and untraceable.
To reach a dark website, you need a secure browser like Tor. It works similarly to other browsers like Chrome or Firefox, but channels data through a series of connections rather than going directly to your online destination. This is more secure, but much slower.
Websites on the dark web have randomly created URLs consisting of up to 56 letters and numbers. For Tor, instead of using .com or .net, dark web sites end in .onion.
Note: The dark web has both legal and illegal websites, and it is unregulated. While some uses are legitimate, it can also host illegal activities. Always be cautious and follow the law when using any part of the internet.
Step-by-Step Guide: Access the Dark Web Safely on Any Device
Download and Connect to a VPN
- Get a VPN with strong encryption, a strict no-logs policy, and leak protection. ExpressVPN is compatible with Tor. Plus, it’s highly secure and fast.
- Download the VPN to your device. Most VPNs have apps for multiple platforms.
- Connect to a server. Choosing a nearby server, or letting your VPN auto-connect you to the best option, ensures a fast and reliable connection.
Download and Install Tor
Download Tor from its official website at torproject.org. Avoid fraudulent Tor-like browsers that compromise your online security. The browser is free to download and works on multiple operating systems.
Instructions vary depending on your operating system:
Windows
- Visit the Tor Project website and click “Download for Windows.”
![]()
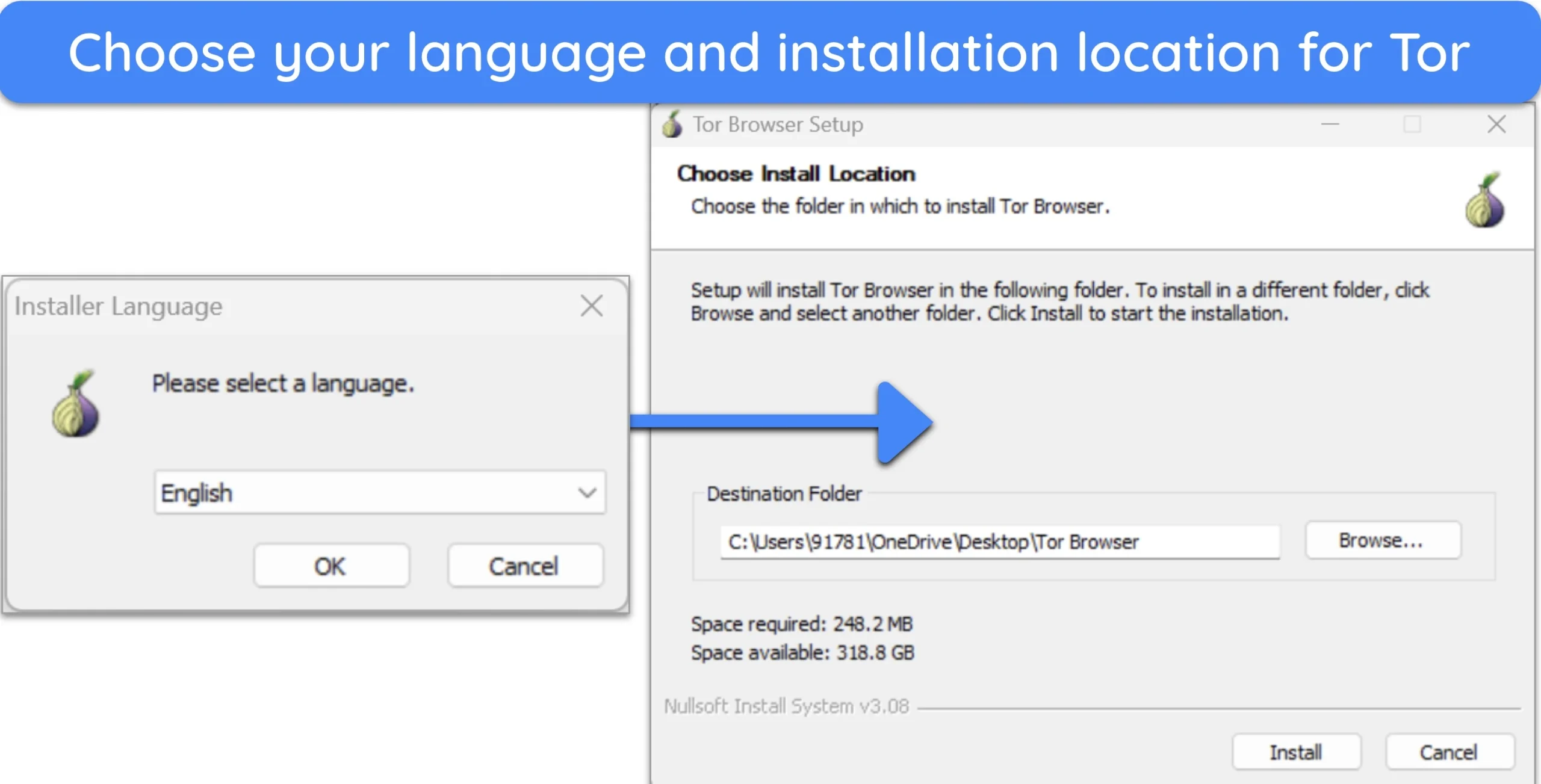
- Click the installer and follow the setup prompts. You can choose your language preference and an installation location for Tor.
![images of Tor browser setup steps for Windows devices.]()
- Click “Install.” Once installation is complete, you’ll be prompted to click “Finish.”
- You can now launch Tor using the main menu or your desktop shortcut.
Mac
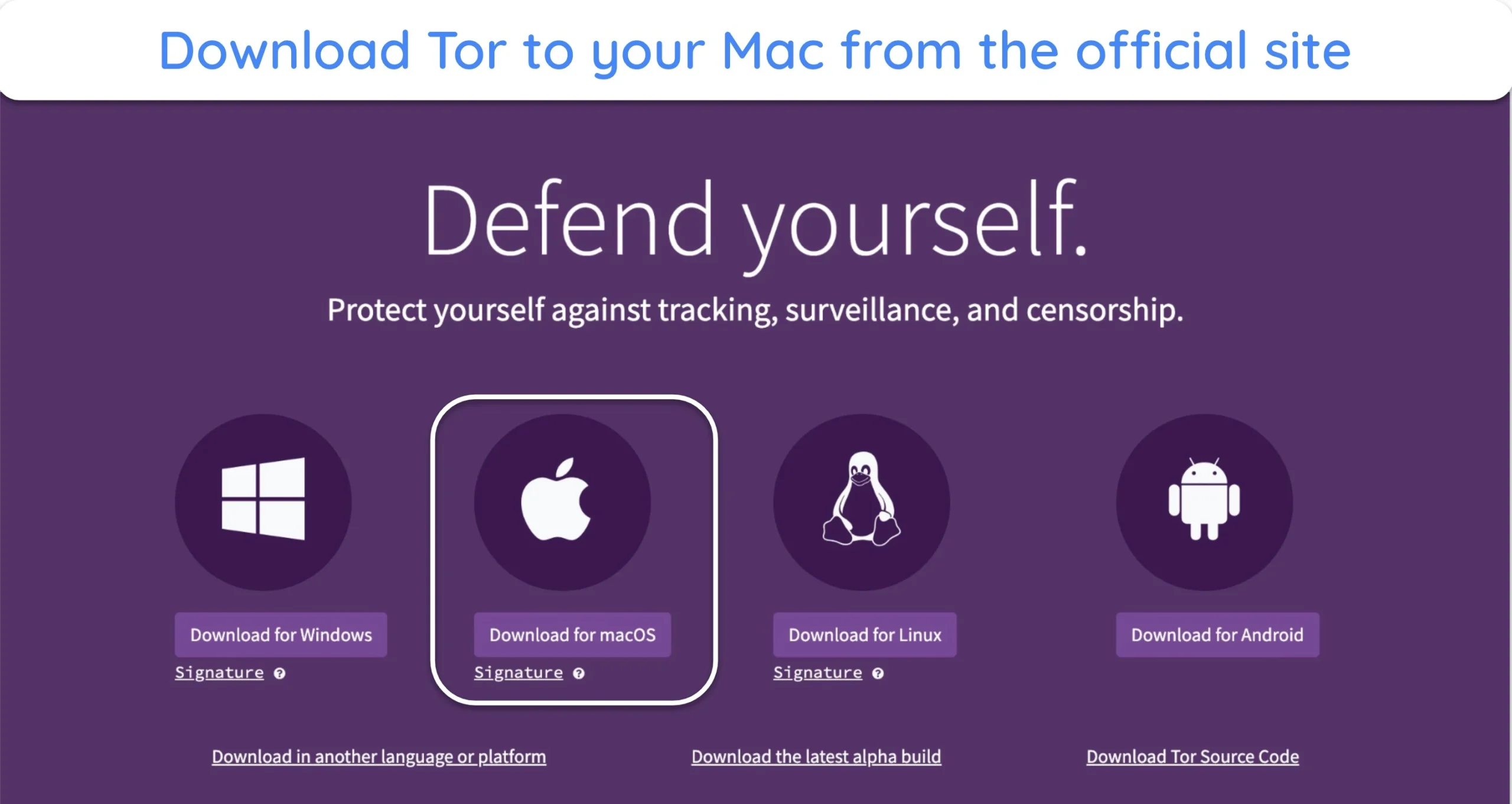
- Download the Tor browser for Mac from the official Tor Project website. Click “Download for macOS.”
![image of Tor Project website with "Download for Windows" highlighted.]()
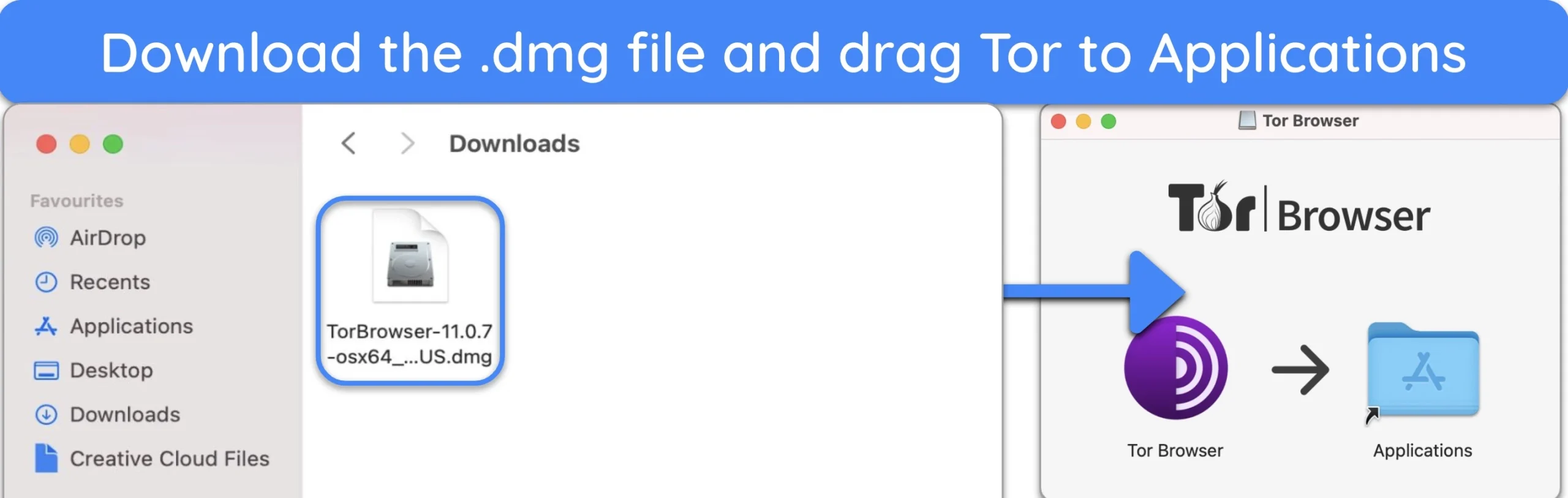
- Double-click the Tor .dmg file in your downloads folder to install the browser.
- You’ll see a screen with a Tor icon and the Applications folder. Drag the icon into the Applications folder to install Tor.
![images of Mac with instructions showing how to download the Tor .dmg file and to drag Tor into the Applications folder.]()
- Launch Tor using the Launchpad or shortcut on your toolbar.
![image of Mac toolbar with "tor browser" in the search before being launched]()
Linux
- Download Tor for Linux from the Tor Project website.
- Right-click on the file and choose “Extract here.” A new folder will be created with the extracted contents.
- Open the new folder. There will be another folder inside that you need to access called “Browser.”
- Double-click the Tor icon to launch the browser. You might have to confirm that you trust the downloaded application in order to open it.
Android
- Visit the Tor Project website on your Android.
- Tap “Go to Google Play.”
- Tap “Install”.
- Tap “Connect”.
- Verify connection at check.torproject.org.
iPhone
Tor developers created a reliable and secure app to allow iPhone users to access The Onion Browser, which you can get by following the steps below:
- Open the App Store on your iPhone.
- Search for “Onion Browser.”
- Tap “Get and Install.”
- Launch Onion Browser.
- Tap “Connect.”
Set Up the Tor Browser
When you launch Tor for the first time, you’ll be prompted to configure your settings. Check security settings by clicking the shield icon on the browser toolbar. There are three levels: Standard, Safer, and Safest. Standard is the default setting and provides secure browsing. Safer and Safest boost security, but increased protection can stop sites from working properly.
I recommend enabling all available add-ons to maximize security. By default, NoScript is already enabled — this disables JavaScript on untrusted sites. Go to the menu in the top right-hand corner and select “Add-ons” for further optimization.
Safely Browse the Dark Web With Tor
Consider using a safe dark web search engine like DuckDuckGo (https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion/) to find the sites you’re looking for. If you already know the websites you want to access, insert the .onion link into Tor’s webpage bar.
Important! Don’t change the Tor browser screen at any point when you’re using it. Even if you manually resize the browser window, you’re still leaving your digital footprint, which can be used by the authorities or hackers to gather your personal information.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Additional Tips for Safe Browsing on the Dark Web
- Don’t reveal your real identity — try to avoid using information that can be traced back to you — use an encrypted email service (like Proton Mail) and separate email address and username, turn off your device location, cover your camera and microphone, and opt for cryptocurrency payments when making purchases.
- Use a different operating system — a privacy-focused operating system, like Tails or Linux, provides a greater level of security overall. They work with Tor to ensure your activities remain private, offer more control over your data, and have more security features.
- Update your device and browser — regular updates protect your device and browser from vulnerabilities and protect you from hackers, malware, and data breaches.
- Disable JavaScript — JavaScript is used to create interactive elements on websites, but it can be exploited to reveal your IP address, bypass VPN and Tor protections, and execute malicious code on your device — disabling it minimizes the risk of being de-anonymized.
- Use an antivirus — antivirus software with real-time protection defends your device against viruses, Trojans, phishing attacks, malware, ransomware, DDoS attacks, and other harmful programs.
- Open downloads offline — this minimizes the risk of malware “phoning home” to an attacker’s server, which could lead to data exfiltration, remote control of your device, or tracking and tracing your identity.
- Only visit trusted sites — visiting unknown sites poses significant risks, including phishing and malware, illegal content, or fraudulent marketplaces — stick to trusted and well-known websites, or use reputable directories or search engines to find websites.
Why You Need a VPN to Be Safe on the Dark Web
Onion routing makes it more difficult for third parties to trace your data back to you, but it’s still possible to identify you through Tor. Without a VPN, your IP address is exposed to anyone who wants to find it. There are also risks of data breaches if the security of the Tor website you are using is compromised.
For example, in 2014 the FBI caught users involved in illegal activity on the dark web because of a security issue with JavaScript. In 2017, a system failure resulted in multiple websites crashing and exposing the IP addresses of many of its users. Though Tor developers tend to fix issues quickly, they can’t always keep up with them.
A VPN encrypts your data before it reaches your ISP. It also hides your IP address by relocating your virtual location. That way, your ISP won’t know you’re browsing on Tor, and your activity will remain private.
VPN Over Tor or Tor Over VPN: Which Is Better?
While using Tor alone provides some anonymity, it may not be enough to protect you from surveillance, traffic analysis, or malicious exit nodes. To enhance security, you can opt for either a VPN over Tor or Tor over VPN setup.
VPN Over Tor
When you use VPN over Tor, your internet traffic first goes through the Tor network, which hides your identity by bouncing your connection through several different computers around the world. After that, your traffic goes through a VPN, which adds another layer of protection by encrypting your data and hiding your location.
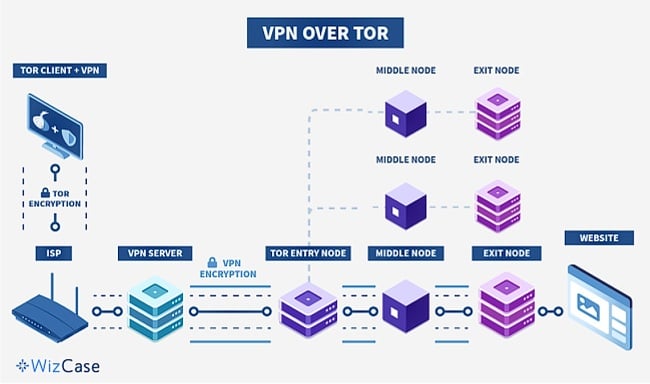
This configuration offers several advantages, including:
- Enhanced privacy through the combination of Tor’s multi-hop routing and VPN encryption.
- The ability to bypass ISP blocks on Tor, enabling access to otherwise restricted websites.
- Protection against malicious exit nodes, as the VPN server obscures the final destination of your traffic.
One disadvantage of VPN over Tor is that you might get slower connection speeds due to the combined overhead of the Tor network and VPN encryption.
Tor Over VPN
In the Tor over VPN setup, you first connect to a VPN and then use the Tor network. This means your ISP can see that you’re using a VPN, but they won’t know you’re using Tor. It’s easy to set up because many VPN providers have built-in support for Tor over VPN.
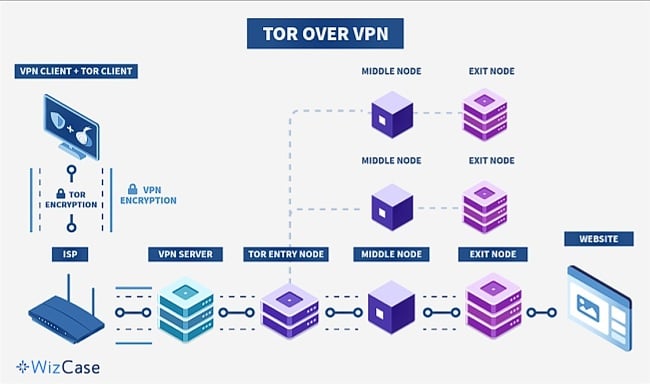
One issue with this method is that you may be vulnerable to malicious exit nodes since your traffic exits the Tor network before being encrypted by the VPN.
Using Tor over VPN is the most secure choice for accessing the dark web because it hides your activity and identity from your ISP and other third parties (like government authorities) who might be able to detect your Tor usage.
No matter which setup you choose, be sure to use a top VPN with a strict no-logs policy to maintain your privacy and resist potential government pressure to disclose user data.
Alternatives to the Tor Browser
While Tor is the best option for browsing the dark web, there are alternatives that offer different levels of accessibility and security. It’s crucial to remember that browsing the dark web always involves risks, so using a VPN for added security is advisable.
- I2P — The Invisible Internet Project allows access to its unique sites called “eepsites.” I2P doesn’t provide access to as many sites as Tor and can be difficult to manually configure. However, I2P is faster and provides better peer-to-peer security than Tor, using one-way tunnels to encrypt traffic. I2P also has a distributed network database that is more resistant to attacks than Tor’s Directory servers.
- Freenet — Only provides access to content uploaded on the Freenet network (not to .onion links). Freenet is an anonymous platform for peer-to-peer content sharing, offering both private and random peer connections. Freenet is much more straightforward to set up and use, and runs automatically in your web browser when opened — I recommend using a different browser than usual to maintain privacy.
Is the Dark Web Illegal?
The dark web is legal to access in most countries, but it can be used for illegal purposes like hacking, selling and buying drugs, and child pornography. Governments and special services worldwide work tirelessly to locate and punish anyone involved in such activities, but it often takes months or years to catch cybercriminals.
Some of the most popular crime stores from the dark web include:
- Silk Road — the first digital marketplace selling illegal goods and services, including guns, forged paperwork, and drugs, with users making anonymous purchases with Bitcoin. Silk Road’s founder, Ross Ulbricht, was arrested in 2013 after the FBI discovered he had set up the website using his real name and email. He was sentenced to life in prison after detectives seized $48 million earned in commissions.
- Hieu Minh Ngo — a hacker who stole the bank details, names, and Social Security numbers of more than 200 million US citizens and sold the data on the dark web. Minh Ngo earned up to $2 million through online transactions before his arrest — he was sentenced to 13 years in federal prison.
- Shannon Grant McCoole — a worker for the Australian Department of Child Protection who launched a child pornography website, uploading explicit interactions with children as young as 18 months old. He was arrested in 2014 and the police discovered more than 100,000 images and 600 videos of exploitation on his personal computer — he was sentenced to 35 years in prison.
- Ashley Madison — a popular dating site for extramarital affairs that fell victim to a dark web hacker attack in 2015, stealing over 60GB of user data. After ignoring the hackers’ demands to shut the site down, the hackers published personal information, including user emails and home addresses — the hackers’ identities remain unknown.
Though extremely unsettling, these are only a few out of hundreds of illegal activities taking place on the dark web every day. However, the dark web isn’t all bad, and you can use it to engage in many useful and legal digital practices.
What You Can Use the Dark Web For

Despite the dark web’s bad reputation, it provides a way for many people to bypass local digital restrictions and access content unavailable in certain countries. Users also view the dark web as a platform to exercise their right to freedom of speech and privacy. Though not exhaustive, these are the most popular positive uses of the dark web:
1. Stay Anonymous Online
The dark web has many social media platforms, gaming websites, and ultra-secure email services. Plus, your online activity is anonymous and can’t easily be traced by hackers and government authorities. It also allows you to bypass censorship and access websites otherwise restricted in many Middle Eastern and Asian countries.
Warning! Don’t log into personal accounts (e.g., online banking or email) on the dark web. Your activity becomes linked to your profile, even if you use Tor. Instead, use a dummy email address.
2. Exposing Corruption
Multiple online magazines and news channels like CNN, FOX, and NBC have open sites on the dark web to receive anonymous tips from online users.
Journalists and whistleblowers regularly turn to the dark web to share controversial information about government representatives, celebrities, or money scandals, like tax evasion. This ensures that activists exposing illegal practices can avoid prosecution.
3. Sharing Personal Stories
Due to the anonymity it provides, many people use the dark web to share their personal stories. This ranges from websites with advice on a variety of topics to online support forums where people discuss traumatic experiences like physical or sexual abuse. It’s a way to connect with other victims and seek help without revealing your identity.
4. Buying Things Anonymously
While I don’t condone purchasing any illegal items, there are many legitimate reasons to buy products and services on the dark web. This includes buying software, electronic devices, or medication.
Warning! Be careful when buying on the dark web. Due to the lack of regulations and the fact that many illegal and stolen items are sold daily on the digital market, you can never be sure what you’re getting. Before making any transactions, check buyer reviews and seller ratings. Also, remember to only use cryptocurrencies as a payment method.
5. Getting Medical Advice
Some doctors offer advice to patients on the Dark Web. Practitioners can be found on various medical forums as well as their own websites. This is a great way to get assistance and advice for those who want to keep their conditions private.
The most popular “Drug Counselor,” who goes by the nickname DoctorX, has answered hundreds of questions regarding drug addiction, self-harm, and more.
6. Joining Online Communities
By browsing Tor, you can find similar sites and online communities that you’d find on the clear web, including clubs and social networks.
Always avoid engaging in any forums involving illegal activities (like sharing sensitive material), as you could face prosecution.
7. Research
The dark web can be a valuable resource for academic research and data gathering, providing access to information that may be difficult to find on the surface web. This includes unpublished works, controversial articles, and unique primary sources across a range of topics.
Researchers can also use the anonymous communication features on the dark web to interact with experts, insiders, and fellow researchers while protecting their privacy. However, it is essential to verify sources, cross-check data, and avoid accessing or engaging in illegal content to avoid serious legal repercussions.
The Risks & Dangers of the Dark Web
Malware
Hackers create fraudulent dark websites containing malware that can infect your computer. These malicious programs can record keystrokes, steal documents and financial data, record audio and video from your computer, or even hijack your personal device for blackmail.
As it’s often difficult to tell whether sites on the dark web are legitimate, it’s easy to download malware without knowing. To stay safe, use the dark web with a specific aim in mind and do research beforehand to get a list of trustworthy links.
Criminal Activity
The dark web is used by criminals to sell stolen goods, weapons, drugs, and fake documents. Criminals also use the dark web to hire hackers and assassins. Some sites have disturbing and illegal content like child pornography or live-streamed murders. I strongly advise against browsing random sites to avoid accessing unsettling content.
Surveillance
Law enforcement agencies and governments monitor the dark web to catch criminals. As it’s incredibly difficult to identify users on the dark web, governments sometimes set up fake illegal websites to catch cybercriminals. In some countries, you can attract the attention of the authorities simply by using a browser like Tor.
Fraudulent Sites
Fraudulent sites may impersonate popular online marketplaces, financial services, or charitable organizations to deceive users into providing sensitive information. This can include login credentials, credit card numbers, and personal details. Always verify the authenticity of a site before providing any personal information or making transactions.
FAQs on Accessing the Dark Web Safely
Can I access the dark web without Tor?
Can I access the dark web on Chromebook?
How can I find websites on the dark web?
You can use dark web search engines, directories, and forums to find websites on the dark web. Don’t forget to use a VPN while browsing the dark web, even if it seems safe.
Here are some useful websites on the dark web:
- The Hidden Wiki — the Wikipedia of the dark web (http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page)
- DuckDuckGo — a privacy-focused search engine for the dark web and the surface web (https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion/)
- Proton Mail — free, anonymous, and secure email provider (https://protonmailrmez3lotccipshtkleegetolb73fuirgj7r4o4vfu7ozyd.onion/mail)
- ProPublica — award-winning news publication (http://p53lf57qovyuvwsc6xnrppyply3vtqm7l6pcobkmyqsiofyeznfu5uqd.onion/)
- Dread — the dark web equivalent to Reddit (http://g66ol3eb5ujdckzqqfmjsbpdjufmjd5nsgdipvxmsh7rckzlhywlzlqd.onion/)
Note: While these websites are considered safe, it’s crucial to exercise caution and use a combination of Tor and a reliable VPN when browsing the dark web to ensure your privacy and security.
Is there a dark web search engine?
Yes, there are many dark web search engines, but they don’t work as well as services like Google — the dark web changes frequently, so you may get dead links and unhelpful results. Sites found through these search engines may be dangerous, so be sure to research before visiting any sites and use a reliable VPN to protect your privacy.
Here are 3 dark web search engines that work efficiently:
Is it legal to access the dark web?
Can I access the dark web with a VPN?
Why isn’t the dark web stopped or shut down?
Can my ISP see that I am accessing the dark web?
Can I be traced, tracked, or hacked if I access the dark web?
Yes, it’s possible to be traced, tracked, or hacked if you access the dark web. While it provides a level of privacy and anonymity, it’s not foolproof — your activity can be monitored or traced by third parties like government agencies or cybercriminals.
In addition, the dark web is home to a range of illegal activities and content, including drug trafficking, weapon sales, and cybercrime, which can attract the attention of law enforcement agencies and other authorities.
Warning! If you do not take proper precautions, such as using a secure VPN with a Tor browser, your online activity and personal information may be at risk of being hacked or compromised. This can lead to identity theft, financial fraud, and other serious consequences.
Can I access the dark web with a free VPN?
You may be able to access the dark web with a free VPN, but I don’t recommend it. It’s essential to use a VPN with strong security features, and free VPNs often lack the secure protocols necessary to protect your online activity. Free VPNs also often collect and share user data with third parties, and can have slow, unstable connections.
If you really want to use a free VPN with the dark web, there are some safe and secure free VPNs that provide a level of protection. However, you’ll only get comprehensive service from a premium VPN provider.
Access the Dark Web Safely With Tor Over VPN
The dark web provides users with digital freedom and unlimited resources, and there are plenty of positive ways to browse despite its negative reputation. However, it’s vital to follow precautions to use the dark web safely.
Avoid sharing personal information, and use an antivirus and reputable VPN to access the dark web safely. The best VPN for the dark web is ExpressVPN, with top security features and reliably fast speeds for safe, smooth browsing. All ExpressVPN plans are backed by a 30*-day guarantee, so you can get a full refund if it’s not right for you.
*Please note that ExpressVPN’s generous money-back guarantee applies to first-time customers only.
Summary — The Best VPNs to Access the Dark Web Safely in 2025
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.







Leave a Comment
Cancel