The Real Costs of Hacking a Website (+ How to Prevent It)
Cyber attacks happen every 39 seconds, putting businesses of any size at risk of credential theft, system downtime, and revenue loss. Risk Based Security’s report states that in the first quarter of 2020, companies lost about 8.5 million records with sensitive user data. As each lost record costs $150, this amounts to a total of $1.25 billion in damages from cyber attacks.
Luckily, businesses can prevent cyber attacks and related financial consequences with the right cybersecurity methods. This guide will break down the costs of managing the impacts of a cyber attack and teach you how to prevent one, regardless of whether you’re a business owner or not. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
The Cost of Launching a Cyber Attack (And Cleaning Up After One)
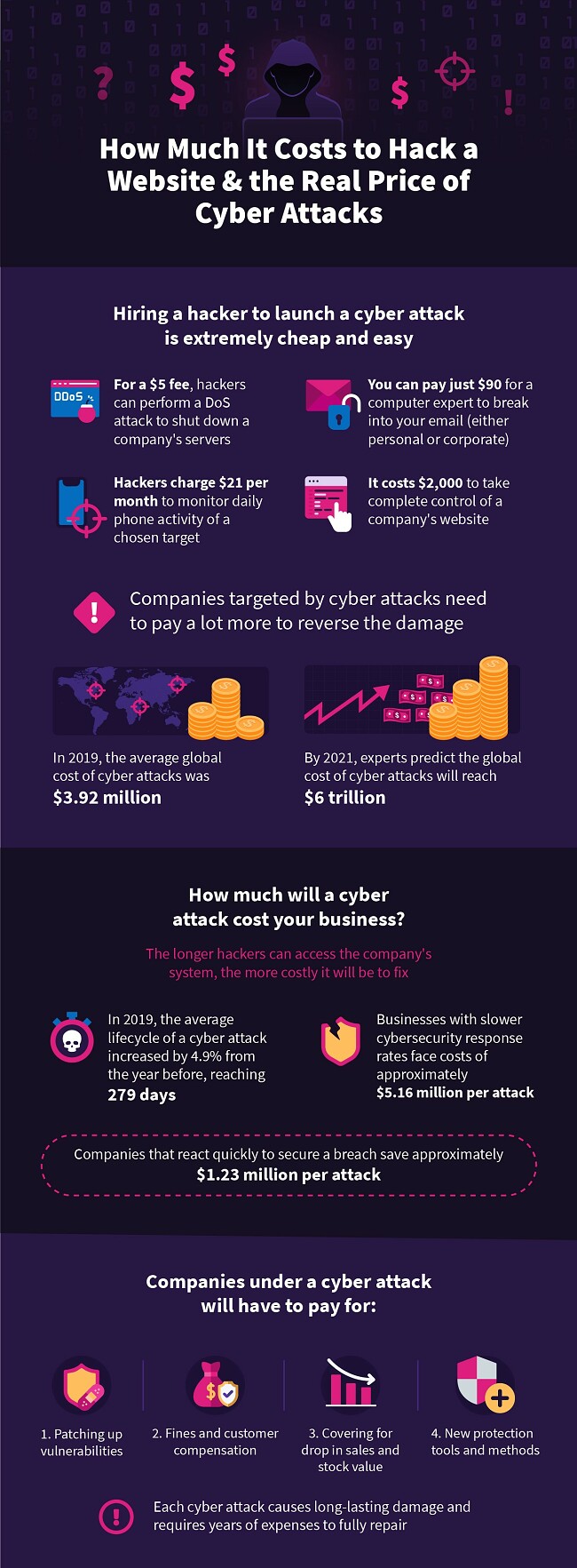
Due to its affordability, anyone can hire a hacker for both ethical and malicious purposes. Computer programmers offer to perform quick DoS attacks to shut down specific servers for as little as $5. If you accidentally lock yourself out of your email account (personal or corporate), you can hire an expert to break into it for only $90. A tech professional will monitor a target’s phone activity for just $21 a month. Worst of all, it only costs around $2,000 to hack into a company’s website and take complete control of it. Unfortunately, the ease of performing unethical attacks puts companies at enormous risk of data loss and financial costs that ruin many businesses.
According to IBM’s 2019 report, the global average cost companies incur after a cyber attack is $3.92 million. This includes detecting and reporting a breach, fixing vulnerabilities, and applying new tools to prevent future attacks. Yet with the steady growth of new and dangerous hacking methods, the Cybersecurity Business Report predicts that costs related to cyber attacks will reach $6 trillion by 2021.
Out of the total cost of a cyber attack, 36% is used to compensate for a drop in sales as any breach undermines the credibility of the affected company. Once lost, customer trust is almost impossible to rebuild since 86% of clients admit they would leave a company that failed to protect them. The larger the company, the bigger the loss — according to UpGuard’s 2019 report, companies with a customer turnover of 4% or more pay up to $5.7 million per cyber attack. This is especially true for industries that handle extremely vulnerable data, such as healthcare, pharmaceuticals, and finance. Unfortunately, these are also top targeted industries for hackers all over the world.
The cost of cleaning up after a cyber attack will vary depending on your location. These differences are dependent on the local economy as well as the size and popularity of the companies involved. Research shows that US businesses face the biggest financial burden of $8 million (on average) after each cyber attack. The Middle East is a close second with about $6 million reported per attack. With such high numbers, it isn’t surprising that just one breach can put many organizations out of business. Even in countries like Brazil and India, which experience the lowest financial loss (between $1-2 million per attack), many companies still struggle to cover the costs due to their significantly lower income.
Cyber attacks can also cause long-lasting damage to a company’s budget. While 67% of total costs occur within the first year, a company may still be responsible for 33% of costs years after the incident. These delayed payments are often the result of a drop in stock market value, increased cybersecurity insurance rates, and any lawsuits that may come as a result of a data breach. This means that each company must be prepared for unexpected expenditures long after a breach.
The faster a data breach can be identified and contained, the lower the actual costs of managing it. According to Verizon’s 2020 report, the lifecycle of a data breach (which begins as soon as hackers attack your system) is now the longest it’s ever been, with an average of 279 days. Research shows that companies with designated cybersecurity teams were able to locate and secure a breach faster, saving $1.23 million per breach. However, businesses without cybersecurity technology and staff had to pay $5.16 million after an attack — that’s nearly a $1.5 million increase from the global average.
Data Breaches: The Biggest Cyber Threat to Companies

If you’re wondering whether your business can be targeted by a cyber attack, the answer is always yes. Accenture reports that 68% of business owners expect cybersecurity risks to increase as companies switch to digital operations, online access, and cloud storage. Alongside the rapid development of technology, hackers regularly adapt their methods to cause even more harm to their victims. Yet Hiscox (a global specialist insurer) disclosed in its 2019 report that 70% of organizations aren’t prepared to prevent any type of cyber attack.
Oftentimes, companies apply the cheapest security solutions or don’t account for cybercrimes in their budget. A vast majority of businesses hire cybersecurity novices instead of contracting an expert to save money. But in reality, security experts are able to quickly apply appropriate protective methods if an attack were to happen. Hiscox’s 2018 report revealed that 51% of security novices admitted they didn’t know what cybersecurity changes should be made after a cyber attack. On the other hand, 72% of cyber experts apply at least one protection improvement, such as adding extra detection technologies, to effectively prevent other breaches.
However, only 51% of all data breaches are from hacking. Employees are likely to make mistakes that account for a quarter of cyber attacks, especially if they don’t have appropriate cybersecurity training. A single employee can compromise the security of the whole system with just one click. An entire network can get infected in minutes, take months to fix, and cost a company millions of dollars.
Recent studies report that 24% of cyber attacks are caused by system glitches, such as unaccounted IT and business system failures. The issue stems from lack of sufficient testing as well as overloading the IT department with work. This is common, especially for large companies where databases are too large for security experts to handle. Without up-to-date backups and testing, systems can crash and allow hackers easy access.
Unfortunately, a company isn’t immune to future cyber attacks even if it has already experienced a data breach. In fact, the possibility of becoming a victim of multiple cyber attacks has risen to almost 30% in recent years. This means each business may experience multiple breaches within 2 years, which can double the financial repercussions.
Large Companies: The Main Target of Cybercriminals
Research shows that 75% of all cyber attacks target large businesses. Despite such an undeniable threat, big businesses are significantly less likely to prioritize cybersecurity. Only a quarter of UK and US businesses have efficient prevention methods to stop a cyber attack. Some of the biggest companies in the world, like Microsoft, NASA, and Facebook became victims to hacks at least once since 2018.
The main problem with managing cybersecurity is the vast diversity and complexity of systems within large corporations. Due to constantly expanding databases from mergers and acquisitions, big companies have more areas to protect. Despite having sufficient funds to apply effective cyber attack prevention, cybercrime develops too quickly for robust companies to prepare in time. As a result, corporations can suffer from extremely high financial losses and significant reputation damage. According to Radware’s 2019 report, 37% of businesses experienced damage to their public image after a cyber attack. On top of that, many companies report their stocks dropped by 0.43% after an attack was disclosed to the public.
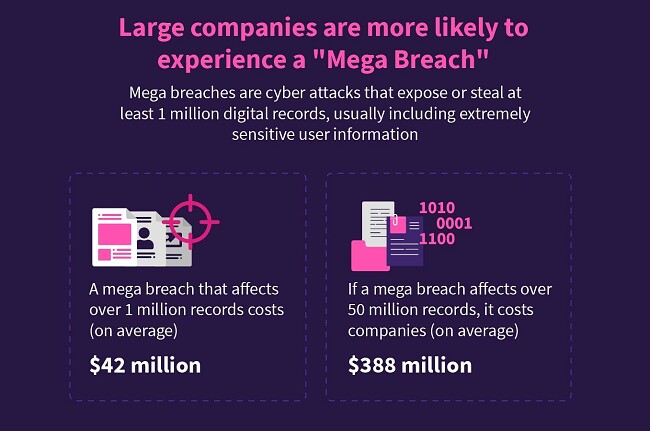
Large companies are also prone to experiencing a mega breach that exposes more than 1 million records. Studies show that these massive cyber attacks can cost businesses even $42 million. Even worse, mega breaches that affect over 50 million digital records cost corporations over $388 million! The costs associated with mega breaches are continuously rising due to the increased complexity of reversing the damage. With a cost increase of even 11% since 2018, experts predict large companies will soon be forced to pay record prices for larger breaches.
Small Companies Aren’t Immune to Cyber Attacks
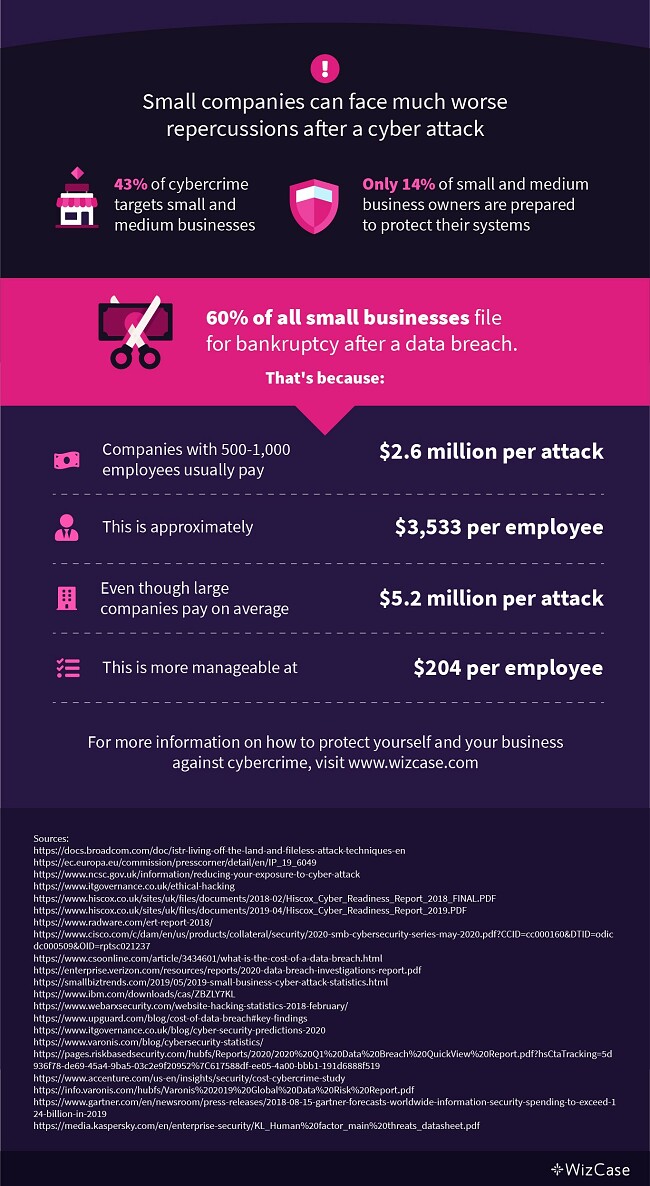
Though news reporters tend to focus on breaches in large corporations, 43% of all cyber attacks are aimed at smaller businesses. However, only 14% of these companies are prepared to sufficiently protect their networks. Owners put too much trust in digital services from lack of experience or detailed knowledge. Even with the most expensive online security tools, small and medium-sized businesses (SMBs) tend to disregard the importance of routine cybersecurity updates. Unfortunately, this makes them less likely to effectively prevent advanced cyber attacks.
Though it may seem like SMBs face much lower financial implications after a cyber attack than their bigger competitors, these repercussions also cause a lot more damage. For example, the average cost of a data breach in a company with 500-1000 employees can reach $2.6 million. This is about $3,500 per employee — an amount any small business can barely cover. Even though large companies pay twice as much to reverse damage caused by a cyber attack, it amounts to only $204 per employee. This imbalance causes 60% of affected small companies to file for bankruptcy due to the lack of sufficient funds to recover from a cyber attack.
6 Types of Cyber Attacks to Watch Out For
In order to protect your company (and yourself) from cyber attacks, you need to know the dangers you’re facing. It’s important to stay up-to-date with existing and emerging attacks as hackers are constantly developing more complex methods to infiltrate systems. All types of cyber attacks can be used on their own or combined with others for a breach on an even larger scale.
1. Denial of Service — the Most Popular Cyber Attack
Denial of Service (DoS or DDoS) is the most popular cyber attack used to prevent a website from functioning properly. By sending multiple online requests, DoS impedes a site from processing its internet traffic, causing a crash that completely stops it from responding. Though it isn’t used to steal user credentials, DoS attacks aim to disrupt online business and crash servers to cause financial loss. That’s why its main targets are any companies that rely on online platforms to provide services or distribute goods.
2. Malware
Malicious software, also known as malware, is any program designed to create severe damage to a victim’s device. It allows hackers to view, modify, and steal private data in the form of viruses, trojans, ransomware, and spyware. It’s estimated that hackers create 300,000 pieces of malware daily.
Viruses
A virus is a computer program designed to corrupt files, destroy data, and cause damage to your computer system. Viruses can be spread through emails, pop-up ads, instant messaging systems (such as Facebook Messenger), or file-sharing platforms like torrent sites. Unlike any other type of malware, viruses have self-replicating capabilities. This allows them to duplicate and spread across all files on any infected device to further spread damage.
Ransomware
Possibly one of the most dangerous malware types, ransomware encrypts certain files on a device or completely locks you out of its system. You then have to pay a ransom specified by the attackers to regain access. Despite the decrease in overall number of ransomware incidents that target the general public, companies found a 41% increase in ransomware attacks from hackers that focus on businesses instead.
Trojans
Trojans are malware files that disguise themselves as legitimate and harmless programs. Just like viruses, they are usually spread through file-sharing platforms, like torrent websites and email services. However, trojans are commonly used to create backdoors for hackers who create them. That way, attackers can further infect a device with other types of malware, such as spyware or ransomware.
Spyware
Spyware is created with one aim in mind — to spy on the device it’s downloaded on. Once safely installed on your device, spyware can easily record keystrokes, monitor online activity, or even steal files from your device. It allows hackers to collect personal information about the victims, including bank details, home addresses, and phone numbers.
Adware
Adware includes all software designed to display ads on your device. Usually used to increase online sales, adware can also be a great hacking tool as it’s easy to disguise as a legitimate product. Oftentimes, hackers use adware to enable man-in-the-middle attacks, which redirect your online traffic through the cybercriminals’ servers. This allows them to intercept and monitor your activity while gathering your sensitive data.
3. Formjacking
Formjacking is a very popular and easy way to steal user credentials. Hackers simply upload malicious JavaScript code on any retail website, which gives them free entry to databases with credit card details. Over 4,800 small retailers and popular stores are affected by formjacking each month. The 2019 Symantec report shows that the main targets of formjacking are small and medium-sized vendors, rather than high-end stores. That’s because smaller e-commerce companies tend to have lower cybersecurity measures in place, making it easier for attackers to inject the dangerous code on their site.
4. Cryptojacking
One of the latest online threats, cryptojacking (or cryptomining), allows hackers to use a victim’s device to mine for cryptocurrency. It can compromise not only commonly used gadgets like laptops, tablets, and cell phones, but also attack singular web browsers.
Cryptojacking programs can be distributed just like any other malware. Usually sent through emails or pop-up ads, the software downloads itself in the background as soon as you click on an infected link or attachment. Created to go undetected at all times, the program then runs the cryptomining code without a user ever realizing.
Alternatively, hackers can upload a piece of malicious JavaScript code into a specific web page to exploit cryptocurrency from multiple victims at the same time. So called “drive-by cryptojacking” infects every device that accesses an infected website and continues to cryptomine even after it’s disconnected from the source.
5. Supply Chain Attacks
Targeting software developers and distributors, supply chain attackers upload malicious code within a product’s network protocols, update mechanisms, and source codes. The malware is then redistributed with the software product as a new app or an update without the vendors realizing. As the malicious code is built into the existing system, it can run with the same permissions as the program it’s in. This means that anyone who uses the infected program allows hackers to collect the personal information stored within their devices.
Supply chain attacks can affect more than just the software — hackers can target various tech devices and pre-install malware on them before they’re sold to the public. The popular targets for hardware supply chain attacks include cameras, phones, webcams, and USBs.
6. Phishing
Contrary to popular belief, phishing doesn’t take just one form. There are many different phishing methods you may not be aware of.
Email phishing
Email phishing is one of the simplest yet most dangerous cyber attacks, designed to steal credentials and infect devices with malware hidden in email attachments. Using fake email addresses that mimic trustworthy organizations, attackers create generic emails to send to large groups of people with scary and believable messages that compel them to click on the attached links or documents.
Spear phishing
Spear phishing aims to steal private data and spread malware, but the attack is developed with a specific target in mind. It can be just one person or a whole organization that hackers can benefit from attacking. The email is carefully crafted after in-depth research that allows attackers to get to know their victim. The more information a hacker has, the more likely a spear phishing attempt is to be successful.
Whaling attacks
Otherwise known as a CEO scam, whaling is a subtle and sophisticated phishing attack that targets senior executives of different companies. Scammers disguise themselves as important or influential members of an organization (a ‘whale’) in order to steal crucial information or money. Due to the seemingly high seniority level of the sender, the victims are less likely to refuse anything the email is asking them to do.
Requests related to tax returns and payroll are the most common examples of whaling. That’s because a successful attempt provides cybercriminals with an abundance of useful information such as full names, email addresses, and social security numbers.
Preventing Cyber Attacks: Why You Should Hire a Hacker
Cybercriminals are getting more creative with their attacks and developing new methods as quickly as tech experts are fixing existing vulnerabilities. The best way to protect your company from cyber attacks and prevent a breach before it happens is to hire an expert with extensive cybersecurity knowledge — an ethical hacker.
What is an Ethical Hacker?
Ethical hackers (also known as penetration testers or pen testers) are hired to break into a company’s computer systems to evaluate their security. Simulating an actual cyber attack allows them to see what changes need to be implemented to increase an organization’s online protection. Hiring an ethical hacker is completely legal — very often it’s even highly recommended for many businesses.
Pen testers will provide you with a full report and suggested security improvements, but it’s your responsibility to ensure your IT team has the resources and knowledge to action them.
Where Can I Find an Ethical Hacker?
There are multiple pen testing companies across the world offering a range of hacking services. Using a registered company ensures the top expertise and trustworthiness of each hired hacker.
If you want to hire a freelance pen tester and avoid any additional costs, you can find them through various hacking forums. However, if you aren’t using a reliable hacking company, always check the tester’s reviews and ask to see his or her training certificates. Check specifically for Certified Ethical Hacker (CEH) qualification as it’s provided by EC-Council, one of the most renowned e-commerce consultancy companies.
Warning! Beware of malicious hackers who use fake credentials and diplomas to trick potential clients into hiring them. They could use your information against you.
How Much Do Ethical Hackers Charge?
According to IT Governance, an ethical hacker usually charges between $4,000-$30,000, but it can reach as much as $100,000 per project. It may seem like a steep price at first, but it’s only a small percentage compared to the average of $4 million needed to reverse an actual cyber attack.
The cost varies depending on what you’d like a pen tester to do. To avoid high expenditures, you can ask ethical hackers to perform specific tests within an area of your choice instead of hiring them to check your whole network. This can be running external penetration tests, improving mobile app security, or replicating a social engineering attack. Make sure to specify your area of focus before hiring a pen tester to avoid unnecessary additional charges.
The final cost also depends on how complex your system is and what tools or skills the hacker needs to test it. The more complicated the issue, the higher the price will be. Regardless of the cost, hiring a pen tester is highly recommended to protect any business. The only way to beat a malicious hacker is to hire someone who thinks like one.
8 Additional Tips to Protect Your Business From Hackers
There are various other steps you can take to prevent cyber attacks. While they aren’t cheap, preventive methods still cost less than the fees to repair damage from hackers.
8 Proactive Measures to Protect Your Business:
- Allocate your budget to provide cybersecurity training: With 47% of businesses claiming that human error was the main cause of a data breach, regularly training your staff is a crucial part of strong cybersecurity protection. This significantly lowers the risk of an attack happening.
- Ensure frequent system security inspections: Each change and update to a company’s network often creates new vulnerabilities. Regularly check for common misconfigurations, such as SMB configurations, open directory listings, and more.
- Separate your personal and business accounts (such as bank accounts, email addresses, and more): Many businesses, especially smaller ones, still keep them within one system. Keeping them separate will ensure that even if your personal accounts is compromised, hackers won’t be able to access your business data.
- Regularly monitor third- and fourth-party vendors and their data protection policies: All companies you collaborate with have access to your network and databases. This means that if their system becomes compromised, attackers will be able to break into your company’s network.
- Consider adding responsible disclosure policies and bug bounty programs: Having a separate publicly available email address will allow ethical hackers to contact you if they find a weak point in your system. Alternatively, set up bug bounty programs and offer rewards to anyone who can break into your network.
- Limit user access control: Not all employees need to access all files on the network. Narrow down who should view certain files and provide them with appropriate login details and passwords.
- Decide on appropriate disaster recovery procedures: Having a plan will show your employees what to do if your business becomes the victim of a cyber attack. This knowledge will significantly speed up the recovery process to save your company a lot of money.
- Regularly back up your whole system and data: In the event of a cyber attack, having back-ups significantly speeds up the disaster recovery process.
Reader Beware — Companies Aren’t the Only Targets
While hackers are more likely to perform an attack on an existing business, the National Cyber Security Centre (NCSC) reports it is common for personal devices to become intercepted. As long as you have internet access, you’re in danger of becoming a victim of cybercrime.
Hackers target private victims to steal their bank details, credit card numbers, and various other credentials. These can then be used for transferring large amounts of money out of your accounts and stealing your identity to sell on the Dark Web. Additionally, the stolen information can be used against you for blackmail.
The most common cybercrimes that target the general public are malware attacks and phishing (especially through email, text messages, and phone calls). Luckily, you can increase your online safety if you apply certain changes to your digital habits.
6 Easy Steps to Protect Yourself Against Cyber Attacks:
- Use strong passwords and store them in secure password manager programs.
- Invest in a reliable antivirus.
- Avoid unsecured websites — if they don’t have a protected HTTPS address, it’s best to avoid them.
- When using an online service, adjust the account security settings and provide only the absolutely necessary information.
- Regularly update your operating systems and security software.
- Never open links or attachments in emails and messages from unknown senders.
Apart from taking extra precautions yourself, never trust any business to keep your data safe. If their network becomes intercepted, your details will be at risk. Even with the toughest cybersecurity system, any business is susceptible to cyber attacks. That’s why, regardless of how trustworthy a site may be, always implement protective measures to prevent becoming a victim of a cyber attack.
With the Right Plan, You Can Avoid the Financial Repercussions of a Cyber Attack
As more companies are shifting their services and storage online, they are more at risk of cyber attacks than ever. The costs associated with fixing the damage caused by hackers can reach unbelievably high financial consequences in a very short amount of time. However, you can prevent your company from becoming another victim of cyber attacks if you know how to avoid prevalent online threats and keep up with cybersecurity advances.





Leave a Comment
Cancel