How Does a Password Manager Work? Guide & the Best App
You likely reuse passwords for most accounts to avoid remembering many passwords. However, reusing passwords is risky. If one account is compromised, the rest are likely to follow. A password manager creates, stores, and auto-fills your credentials to minimize risk.
Unfortunately, not all password managers are reliable. Some have weak encryption, while others have been victims of data breaches. I put in the legwork and tested 20 top names in the industry to find the best all-around password manager.
Dashlane is the best overall password manager. It has a zero-knowledge architecture and includes valuable extras like secure sharing, a built-in VPN, and dark web monitoring. You can try it risk-free with its 30-day money-back guarantee.
Short on Time? Here’s What You Need to Know About Password Managers
- What is a password manager? A digital vault that can securely store your sensitive data and auto-fill it when needed. Jump to see what else a password manager can do.
- How does a password manager work? It encrypts your password data into unreadable code to hide it from snoopers. Here’s how it secures your credentials.
- How do I choose a password manager? Choose from online/cloud, offline, and token-based password managers. Jump here to learn the pros and cons of each.
- What’s the best password manager? Dashlane is my #1 choice due to its feature-richness. Read why Dashlane is the best here.
What Is a Password Manager and What Does It Do?
A password manager is a digital vault that holds the keys to all your online accounts. It’s a secure software program that stores your usernames, passwords, financial data, and personal information in one place. But unlike writing them down on a sticky note, a password manager encrypts your passwords to make them accessible only to you.
You only need to remember a single key called a master password. The best password managers have built-in generators that can create strong passwords in a few taps. The master password unlocks your vault, revealing all your login details for different sites. Most password managers can even auto-fill your login details when needed, saving you time and frustration. Other benefits include:
- Strong, unique passwords — a password manager can create and store complex passwords in a few clicks and alert you to weak and reused passwords.
- Password sharing — allows a trusted friend to access your online account without sharing specific credentials.
- Device syncing — this lets you use the password manager on multiple devices. Any changes you make on one will reflect on other synced devices.
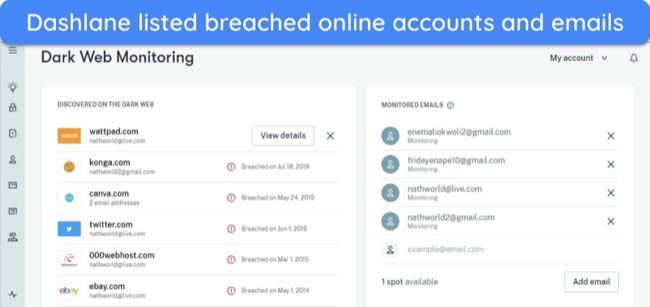
- Dark web monitoring — top password managers like Dashlane alert you if your credentials have appeared in data breaches.
At its core, a password manager encrypts your data to turn it into unreadable code. No one can access your credentials without the decryption key, which only you have. Password managers can store data locally on your device or its cloud servers — I prefer the former. Here’s how they protect you from getting hacked:
- Zero-knowledge architecture — encrypts your data before being stored on the password manager, so even the software doesn’t know what you saved.
- 2-factor authentication — enables a second layer of authentication with a fingerprint, FaceID, or a one-time code sent to your phone to prevent unauthorized access.
- Built-in VPN — to further protect you, some password managers include a built-in VPN so you can browse the internet anonymously.
How Do Password Managers Secure Your Credentials?
A password manager uses a combination of security features to protect your online credentials. These include:
Encryption
Encryption in password managers is like a digital vault door that scrambles your credentials to make them unreadable to anyone who doesn’t possess the key. Most password managers use AES 256-bit, ChaCha20, or Argon2 encryption standards. Here’s a breakdown of the process:
- Key derivation — during signup, your master password is fed into a Key Derivation Function (KDF) and a salt phrase. The KDF stretches the password and makes it more resistant to attacks. It then outputs a key that’s used by the encryption algorithm.
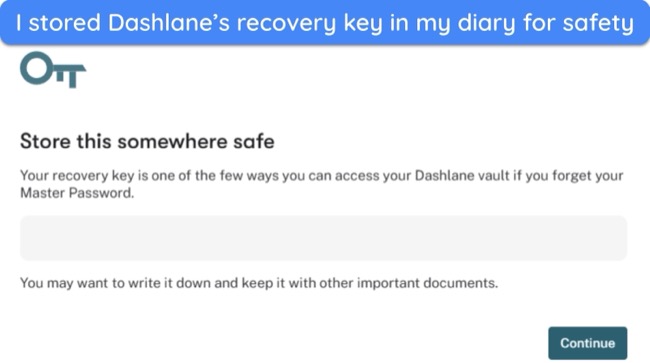
![Screenshot of how to set up a master password when creating an account on Dashlane]() Remember to handwrite the master password in a personal diary for safekeeping
Remember to handwrite the master password in a personal diary for safekeeping - Encryption — the encryption algorithm uses the derived key to scramble your credentials and turn them into an unreadable format.
- Decryption — when you enter the correct master password, the KDF generates the key using your password and salt phrase again. The encryption algorithm uses this key to decrypt your vault and give you access.
Zero-Knowledge Architecture
A zero-knowledge architecture means that even the password manager can’t see the credentials you’re saving. It ensures that data decryption only happens on your device. If the password manager’s server gets breached, your data will remain unreadable without the decryption key only you possess. Here’s how it works:
- Key derivation — your master password goes into a one-way mathematical function with a random secret number (salt). This function turns your password into a unique key for encryption and decryption but can’t be reversed to retrieve your original password.
- Challenge response — when you attempt to access your password vault, the password manager initiates a mathematical challenge and response process.
- Proof generation — your device uses the secret key derived from your master password to perform calculations related to the received challenge. It generates a mathematical response proving you possess the key without revealing it.
- Verification — the password manager receives your response and verifies its validity based on the original challenge. If the response is correct, it grants access to your decrypted password vault.
Multi-Factor Authentication (MFA)
Although the master password is your vault’s sturdy lock, a second verification step prevents unauthorized access even if someone manages to steal your master password. Here are a few types of second-verification:
Time-Based One-Time Passwords (TOTP)
Apps like Google Authenticator generate unique, temporary codes that change every 30 or 60 seconds. Besides the master password, you’ll have to enter the current code displayed on your authenticator app.
Since TOTP codes are constantly changing, they’re significantly more complex to steal or replicate than static passwords. Plus, most authenticator apps can function offline, unlike SMS codes that depend on cellular connectivity.
SMS Verification
SMS verification is the most used, as most people carry a phone with SMS capabilities. After entering your master password, you’ll get a one-time code via text message to your registered phone number. You’ll have to enter this code to enter your vault.
Text-based verification is less secure than authenticator apps. Phone networks can be vulnerable to interception and SIM-swapping attacks that take over your phone number. There’s a slight possibility of attackers receiving the verification code instead of you.
Security Keys
These physical devices look like USB sticks and use Near Field Communication (NFC) or a Universal Second Factor (U2F) protocol for communication. To log in, you’ll have to insert the key into your device’s USB port or tap it against an NFC reader.
Security keys are the most secure. They’re immune to phishing attacks and network vulnerabilities, as they don’t rely on cellular connectivity or the internet. However, it’s easy to misplace these tiny devices, and they aren’t universally compatible.
Biometric Authentication
This method uses your smartphone’s built-in fingerprint reader or FaceID to verify vault access. It’s the fastest and most convenient way to log in to your vault. You don’t have to wait for an SMS code or open another app to fetch an authenticator code.
While convenient, biometric authentication can raise privacy concerns. Unauthorized access is possible through stolen biometric data (fingerprints or facial scans). However, it’s a convenient and secure method to protect your vault.
Advanced Settings
Most password managers let you customize your security level by tweaking settings. For instance, you can block listing access attempts from unknown locations. Other ways of bolstering your vault security are:
- Security questions — set up personal questions that only you can answer as backup MFA. However, choose strong, non-obvious answers that can’t be easily guessed.
- Password strength meter — use the built-in meter to assess the strength of your passwords and make adjustments for enhanced security.
- Session duration — define how long your password vault remains unlocked after successful login. A shorter duration minimizes the window of vulnerability.
- Automatic logout — enable automatic logout after a period of inactivity to prevent unauthorized access if you forget to log out manually.
Types of Password Managers
Password managers come in different types, each with its pros and cons. Knowing these differences will help you pick the one that best suits your security needs.
Online/Cloud Password Managers
Cloud-based password managers let you reach your vaults from any device with the internet. They store your encrypted vault on the password manager’s remote servers. Plus, auto-sync keeps your password vault the same on all your devices. They often have features like secure password sharing and automatic form filling to make things easier.
Look for cloud-based managers with AES-256-bit encryption and a tough key maker (KDF) like PBKDF2. This ensures your data stays unreadable even if the company’s servers get hacked. Also, pick a service with a zero-knowledge architecture, which guarantees your credentials are never stored on their servers.
| Pros | Cons |
Offline Password Managers
Offline password managers encrypt and store your data on your device. Since they don’t need remote servers, they don’t have the weaknesses of cloud storage. Therefore, an offline password manager doesn’t need zero-knowledge architecture. However, you should look for military-grade 256-bit encryption and a tough key maker like PBKDF2.
Since the vault lives on your device, security relies heavily on your master password strength and good device security habits (encryption, screen lock). A weak master password or unlocked device is like leaving the vault door open. Unfortunately, offline password managers often lack auto-sync, so accessing your vaults isn’t as seamless.
| Pros | Cons |
Token-Based Password Managers
Token-based or ‘Stateless’ password managers are usually open source and don’t have a password vault. You can store data in hardware tokens like USB sticks or key fobs. However, hackers can access your account if they have the physical token and the master password. Token-based password managers work in 2 ways:
Software Encryption With Token Authentication
Some password managers rely on a combination of software encryption and token storage. Your password vault might be encrypted on your computer using a robust algorithm (AES-256) and then transferred to the token for secure storage. The token works as a secondary layer of security, requiring a PIN or fingerprint scan for access.
On-Device Encryption
Other token-based managers encrypt data on the device. Therefore, you don’t need password management software on your computer, reducing hassle. This approach reduces the attack surface, as it doesn’t rely on software vulnerabilities. Plus, token-based password managers let you access your data without the internet.
| Pros | Cons |
What a Password Manager Doesn’t Do
While password managers keep your online credentials secure, they can’t protect you from all security threats. Here’s what password managers can’t do:
- Automatically update passwords — a password manager can detect weak, reused, and compromised passwords but doesn’t automatically update them. You’ll have to manually update your passwords on the respective websites.
- Stop malware like keyloggers — keyloggers are malicious programs that record your keystrokes to steal your credentials. A password manager can prevent keystroke recording with auto-fill, but it can’t remove viruses on your computer. To protect yourself from viruses, you must use a top-tier antivirus.
- Secure physical devices — if someone accesses your unlocked device with the password manager running, a password manager can’t stop them from stealing your credentials.
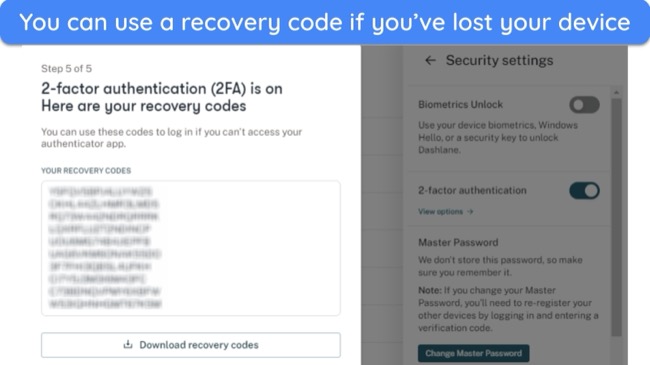
- Remember your master password — forgetting your master password can lock you out of your vault for good. However, some password managers like Dashlane offer recovery methods.
How to Choose a Good Password Manager
With so many password managers on the market, picking the right one depends on your specific needs and priorities. Here are some factors to make a good purchase decision:
- Security features — pick a password manager with 256-bit encryption, zero-knowledge policies, multi-factor authentication, and dark web monitoring.
- Extra features — look for bonus features like a password generator, one-click password change, secure sharing, file storage, and vault editing.
- Compatibility — ensure the password manager supports all major platforms and has auto-sync if it’s cloud-based.
- Ease of use — a well-designed and intuitive interface makes a password manager easy to use. Consider trying out free trials or demos to get a feel of the user experience.
- Money-back guarantee — this gives you a window to try a password manager risk-free. Look for solutions with at least a 30-day refund policy.
What’s the Best Overall Password Manager?
Dashlane is my #1 choice for password management. It uses zero-knowledge architecture, 2-factor authentication, and military-grade encryption for bulletproof protection against hackers. It also lets you share credentials with your friends and family, with the option to control access permissions. Other features include:
- Password auditing — analyzes existing passwords and scores them on strength, identifying weak, reused, and compromised ones.
- Password generator — can produce 4 to 40-character-long passwords with letters, digits, and symbols and provides a history of previously generated passwords.
- Dark web monitoring — lets you monitor up to 5 email addresses and alerts you to breached accounts so you can take corrective action immediately.
- Built-in VPN — uses Hotspot Shield’s VPN to provide online anonymity, though it’s not as good as other top standalone VPNs in 2025.
With passkeys, you can log into your accounts without a password. Passkeys are special codes Dashlane stores for each account. Instead of typing a password, your device confirms it’s you with a fingerprint, PIN, or FaceID and sends the signal to the website to log you in. However, the app needs to support passkeys for this feature to work.
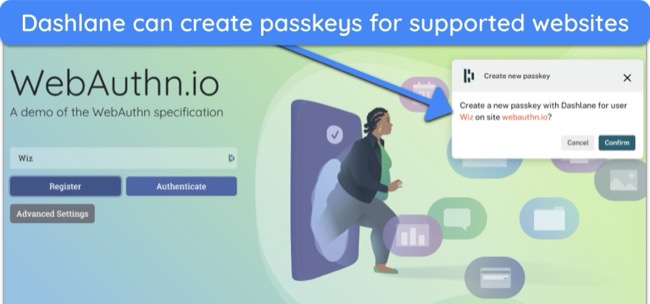
After setting up an account, Dashlane’s ‘Get Started’ dashboard introduces its auto-fill features and shows how to add new logins. Its desktop and mobile apps share an intuitive interface, though I had to give permission to use Dashlane’s auto-fill feature on its mobile app. It also has Chrome, Firefox, Edge, and Safari extensions for convenient vault access.
I recommend Dashlane’s Premium plan, as it offers dark web protection, real-time phishing alerts, and a built-in VPN and supports unlimited devices. The free plan is a barebones app, but you can try the Personal plans risk-free for 30 days with Dashlane’s money-back guarantee. I got my refund in 5 working days by requesting it through live chat.
How to Set up a Password Manager
- Install a password manager — download a password manager for your device from its website or the app store and install it. Click ‘Get Started’ and enter your email.
![Screenshot showing Dashlane's 'Get Started' interface and how to create an account using email address]()
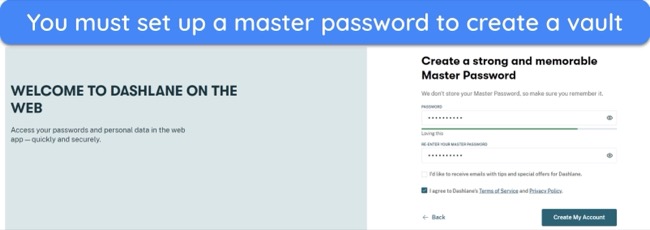
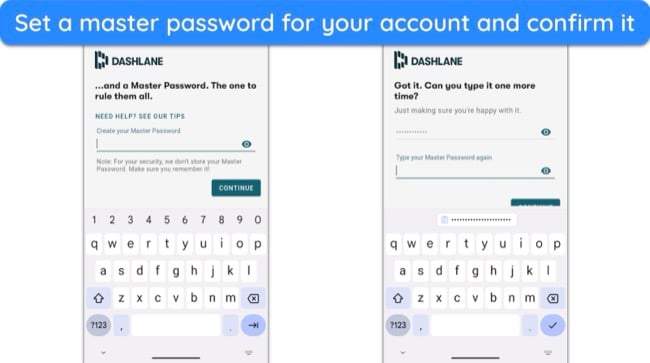
- Create a master password — you’ll have to set a master password after opening the password manager. Handwrite it in your diary for safekeeping.
![Screenshot of how to set up a master password when creating a Dashlane account]()
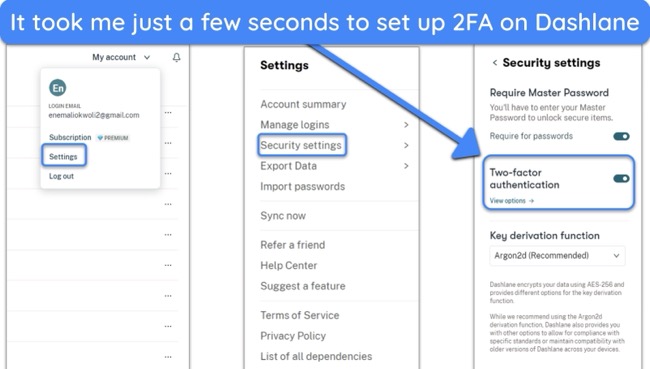
- Enable 2-factor authentication — navigate to ‘Settings’ and enable 2-factor authentication. Select a method like biometrics, an authenticator app, or SMS.
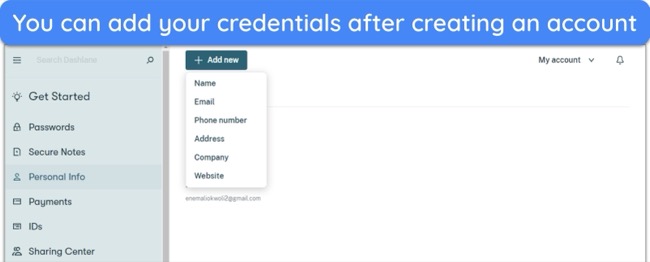
- Add passwords and other data — click ‘Add Logins’ to manually enter your credentials or import them from another password manager.
![Screenshot of how to add credentials on Dashlane after creating an account]()
How to Stay Safe Online
Staying safe online means taking active steps to protect yourself. By following these key tips, you can guard against cyber threats and make your digital space safer. Here’s what you need to do to keep risks at bay.
- Use strong passwords — avoid common phrases and include a mix of letters, numbers, and symbols. Password managers can generate complex passwords for you.
- Update your software — cyber attackers exploit vulnerabilities in outdated software. Keep your operating system, browser, and all apps updated to prevent hacking.
- Be wary of phishing attempts — never click suspicious links or attachments in emails or messages, even if they come from a familiar source, and double-check URLs.
- Use secure WiFi — Public WiFi can be a hotbed for cyber attacks. Use a reliable VPN like ExpressVPN to encrypt your data for online anonymity.
- Limit shared data — the more information you share, the easier it is for cybercriminals to target you. Be mindful of the personal details you post on social media.
Use a Reliable Password Manager to Protect Your Data
A password manager is like your digital safe. It encrypts and stores your passwords and other sensitive data to hide them from prying eyes. This takes the hassle out of remembering many complex passwords and prevents you from reusing them, which is risky. With a good password manager, you can seamlessly log in to all your online accounts.
Choosing the right password manager can be tricky, as many lack military-grade encryption standards. After extensively testing 20 different options, I recommend Dashlane. It has a zero-knowledge architecture, 256-bit encryption, and secure password sharing. You can try Dashlane risk-free with its 30-day money-back guarantee.
FAQs
How do password managers actually work?
What does a password manager do?
What happens if I lose my master password?
If you lose your master password you won’t be able to access your vault or recover stored data. However, top password managers like Dashlane offer recovery options like a reset link sent to your email or security questions. Here are a few common recovery methods:
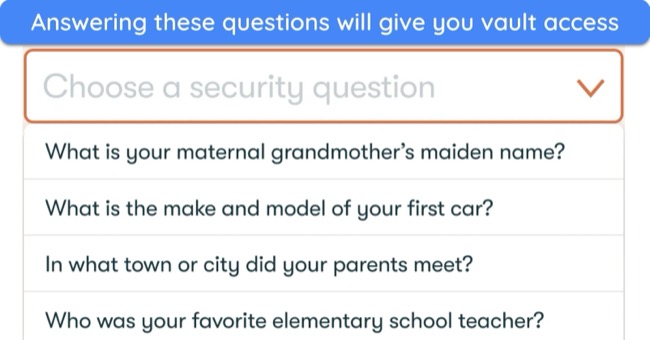
- Security questions — while creating a vault, you can set up personal questions and their answers to validate your future logins if you forget your master password.
![Security questions give you a cushion to access your vault if you forget your master password]() Security questions give you a cushion to access your vault if you forget your master password
Security questions give you a cushion to access your vault if you forget your master password - Secondary password — some password managers let you assign a secondary password, which is less complex than the master password.
- Trusted contact — the password manager sends a recovery link to a trusted contact you’ve assigned while creating an account.
Should I use a password manager?
Yes! Using a top password manager with these features is crucial. Cyber threats are evolving, and attackers can exploit weak passwords or reuse information across accounts. Password managers help you create strong, unique passwords for each login.
Passkeys are a new login method that replaces traditional passwords altogether. It minimizes the risk of weak passwords being exploited by attackers. However, you still need a way to store and use them on your devices. You need a password manager to sync your passkeys across all devices.








Leave a Comment
Cancel