Can iPhones Be Hacked? Top Signs & How to Secure It in 2025
Your iPhone isn’t as hack-proof as you might think. While iOS has strong security, hackers keep finding new ways to get in. Public WiFi, fake apps, and phishing scams can steal your data without warning. If your iPhone drains its battery quickly or sends unusual messages, it may be compromised.
If you’re concerned that your iPhone might be hacked, there are clear signs to look out for and easy steps to fix it. Hackers can track your location, steal passwords, or access private files without your permission. Learning how to detect and eliminate threats can help keep your iPhone secure.
Quick Guide: How to Fix a Hacked iPhone
If your iPhone has been hacked, it’s essential to act fast to stop further damage. Follow these steps to remove threats and regain control:
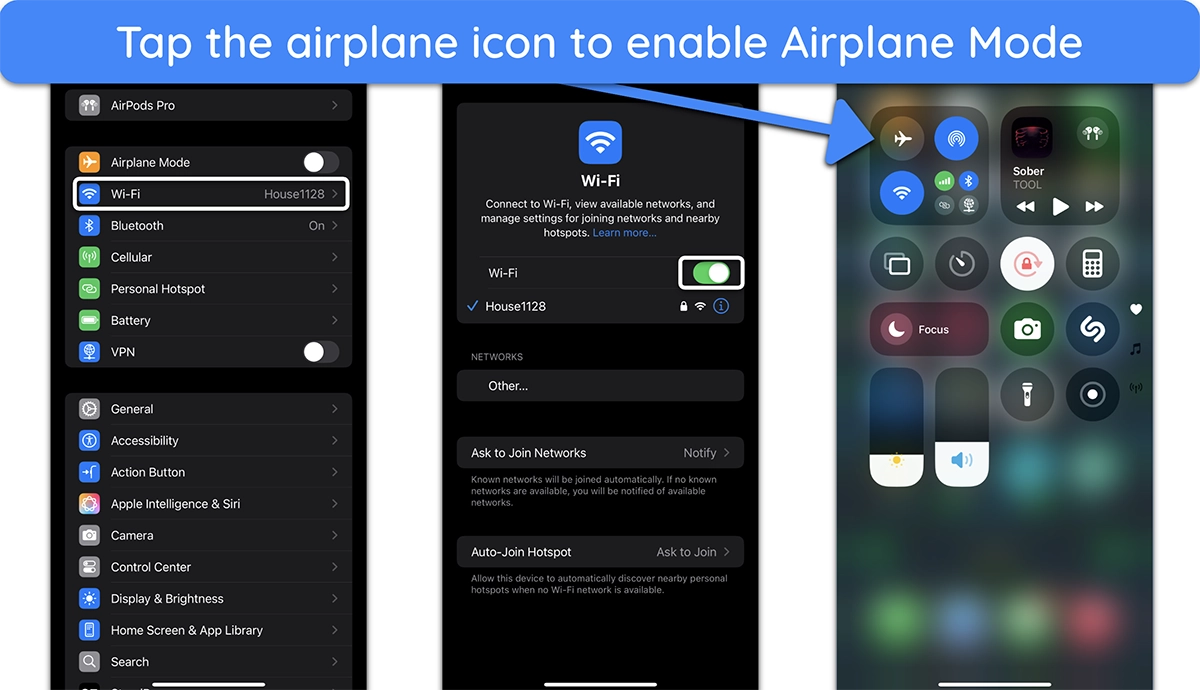
- Cut off access — Turn on Airplane Mode to block hacker control and prevent data theft. Or, go to ‘Settings,’ tap ‘Wi-Fi,’ and turn it off to cut the connection.
![Screenshot of how to enable Airplane mode on iPhone]()
- Check for strange behavior — Watch for fast battery drain, overheating, or lagging performance. Hackers can install hidden apps or run background processes.
- Secure your accounts — Change your Apple ID and email passwords to block unauthorized access. Go to ‘Settings,’ [your name], ‘Sign-In & Security,’ and ‘Change Password.’ Also, update email and other critical passwords.
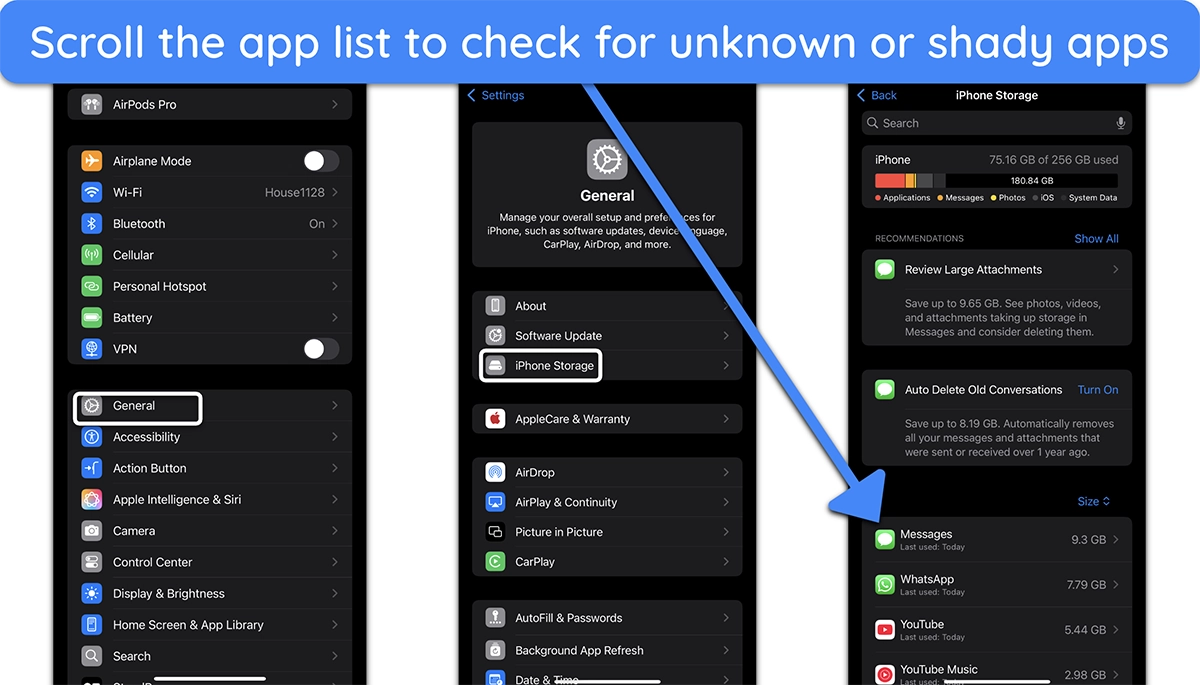
- Delete suspicious apps & profiles — Remove unknown apps by heading to ‘Settings,’ then tapping ‘General’ and ‘iPhone Storage.’ Delete unrecognized profiles in ‘VPN & Device Management.’
![Screenshot of the list of apps showing under iPhone Storage]()
- Assess the damage — Review email, banking, and social media apps for suspicious activity. Check for breach alerts and reset passwords for any affected accounts.
Common Myths About iPhone Security
Many iPhone users believe their devices are unhackable, but that’s far from the truth. False security myths can expose your data, making it easier for hackers to exploit weaknesses. Here are the most common misconceptions and the reality behind them:
- iPhones can’t get malware — iOS has strong security, but hackers still find ways in. Spyware like Pegasus can infect iPhones through phishing links or shady apps.
- Face ID & Touch ID are unbreakable — Face ID can mistake twins for the same person, and Touch ID has been tricked by fake fingerprints. Biometrics help, but they aren’t perfect.
- Public WiFi can’t hack an iPhone — Connecting to open WiFi can let hackers steal passwords or install spyware. They use fake networks to trick you into handing over your data.
- iOS updates aren’t crucial for security — Every update fixes security holes that hackers could use. If you skip updates, you leave your iPhone open to attacks.
- AirDrop lets hackers steal bank info — Viral claims say AirDrop can leak bank details, but that’s false. AirDrop needs your approval to transfer files and doesn’t give access to financial data.
- Apple never shares user data — Apple has strict privacy rules, but some apps can access Face ID data with permission. Your data can also be shared for ads and analytics.
- Encryption apps are unnecessary — Regular calls and texts aren’t secure. The FBI recommends using encrypted apps to keep hackers from spying on your conversations.
How Are iPhones Hacked?
Hackers use advanced methods to steal data, track activity, or take control of iPhones. Even without malware, phishing scams, fake WiFi, and spyware can bypass security protections. Here are the most common ways iPhones get hacked:
- Jailbreaking risks — Jailbreaking removes iOS security limits, allowing unverified apps that carry malware. It also disables updates, making your device vulnerable to future threats.
- Weak passwords and credential leaks — Hackers use leaked passwords from data breaches or guess weak ones. Use unique, complex passwords, enable two-factor authentication (2FA), and get a secure password manager.
- Phishing scams – Attackers send fake Apple ID alerts or tech support messages. Clicking fake links can expose your login details or install spyware on your device.
- Malicious MDM profiles — Fake device management profiles give hackers remote control. Go to ‘Settings,’ tap ‘VPN & Device Management,’ and delete profiles you didn’t install.
- Unsafe public WiFi — Hackers use fake hotspots to steal data or intercept logins. Always verify WiFi networks and avoid entering sensitive information on public connections.
- Zero-day exploits — Hackers target unknown iOS flaws before Apple can patch them. High-profile attacks like Pegasus spyware have infected iPhones through these security gaps.
- Spyware and stalkerware — Some apps secretly log keystrokes, track locations, and access private files. Check ‘Settings,’ tap ‘Privacy’ and ‘Tracking’ to find suspicious apps.
- SIM swapping attacks — Scammers trick carriers into transferring your phone number to a new SIM. This lets them bypass SMS-based 2FA and take over your accounts.
- Juice jacking via charging cables — Public charging stations can install malware through modified cables. Avoid unknown cables and use a data-blocking adapter for safe charging.
Is My iPhone Hacked? Signs Your iPhone Has Been Hacked
Hackers don’t always leave obvious traces, making it hard to know if your iPhone is compromised. Some attacks run silently in the background, stealing data or controlling your device without detection. Here are the key warning signs to watch for:
- Battery drains fast or iPhone overheats — Hidden spyware or background processes may be running without your knowledge, consuming power and processing resources.
- Apple ID login alerts you didn’t trigger — If you receive login attempts or security alerts, someone may be trying to access your iCloud data without permission.
- Unfamiliar Bluetooth or WiFi connections — Your iPhone may auto-connect to rogue networks or unknown Bluetooth devices controlled by hackers.
- Web pages load slowly or redirect randomly — Browser hijackers can modify Safari settings, forcing you to visit malicious sites or spam-filled search engines.
- Unrecognized apps or system configurations — If apps appear that you didn’t install, hackers may have exploited your device to install unwanted software.
- Call, text, or voicemail logs contain unknown activity — Hackers can clone your SIM or manipulate call forwarding to reroute messages or calls.
- Sudden increase in spam calls or messages — If your number was leaked or sold on hacker forums, you might get more frequent phishing texts or scam calls.
- iPhone performs actions on its own — If apps open, settings change, or the screen moves without input, remote access malware may be installed.
How to Fix a Hacked iPhone
Attackers can hide malware, change security settings, or link their devices to your Apple ID. To fully secure your iPhone, you must cut off their access, remove hidden threats, and lock down your accounts. Here’s exactly what to do:
- Check for unauthorized Apple ID access — Go to ‘Settings,’ then tap ‘Apple ID’ and scroll down to see all devices linked to your Apple ID. Remove unknown devices and change your Apple ID password.
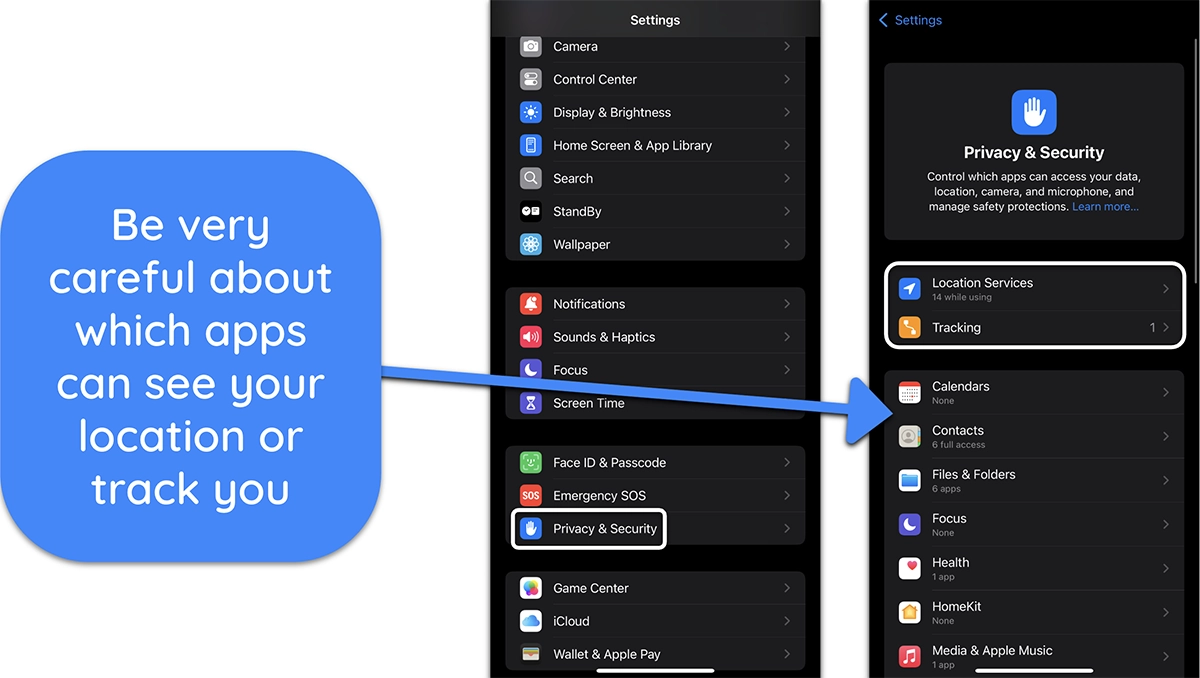
- Revoke suspicious app permissions — Go to ‘Settings,’ tap ‘Privacy & Security,’ and check permissions for location, microphone, and camera. Revoke access from any untrusted apps.
![Screenshot of iPhone's Privacy & Security settings, showing which apps can track and see location]()
- Delete malicious configuration profiles — Hackers use hidden profiles to control iPhones. Go to ‘Settings,’ tap ‘General,’ then ‘VPN & Device Management’ and remove any profiles you didn’t install.
- Uninstall suspicious or unknown apps — Malicious apps can run in the background and steal data. Go to ‘Settings,’ tap ‘General,’ then ‘iPhone Storage’ and delete apps you don’t recognize.
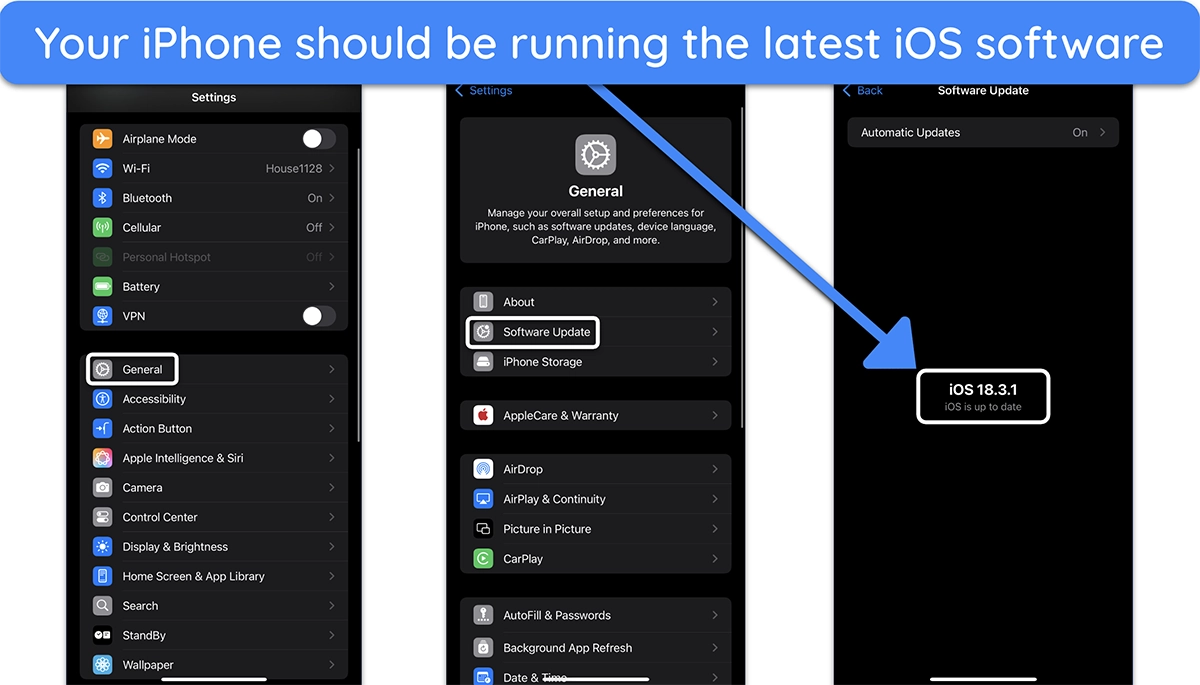
- Update iOS and all installed apps — Security patches fix vulnerabilities that hackers exploit. Go to ‘Settings,’ tap ‘General,’ then ‘Software Update’ to install the latest iOS version.
![Screenshot showing an iPhone running the latest version of iOS]()
- Review trusted phone numbers and emails — Hackers can add their own recovery details. Go to ‘Settings,’ tap ‘Apple ID,’ then ‘Sign-In & Security’ to remove unauthorized numbers or emails.
- Turn off call forwarding — If hackers hijacked your SIM, they could be forwarding your calls. Go to ‘Settings,’ tap ‘Phone,’ then ‘Call Forwarding’ and disable any unknown settings.
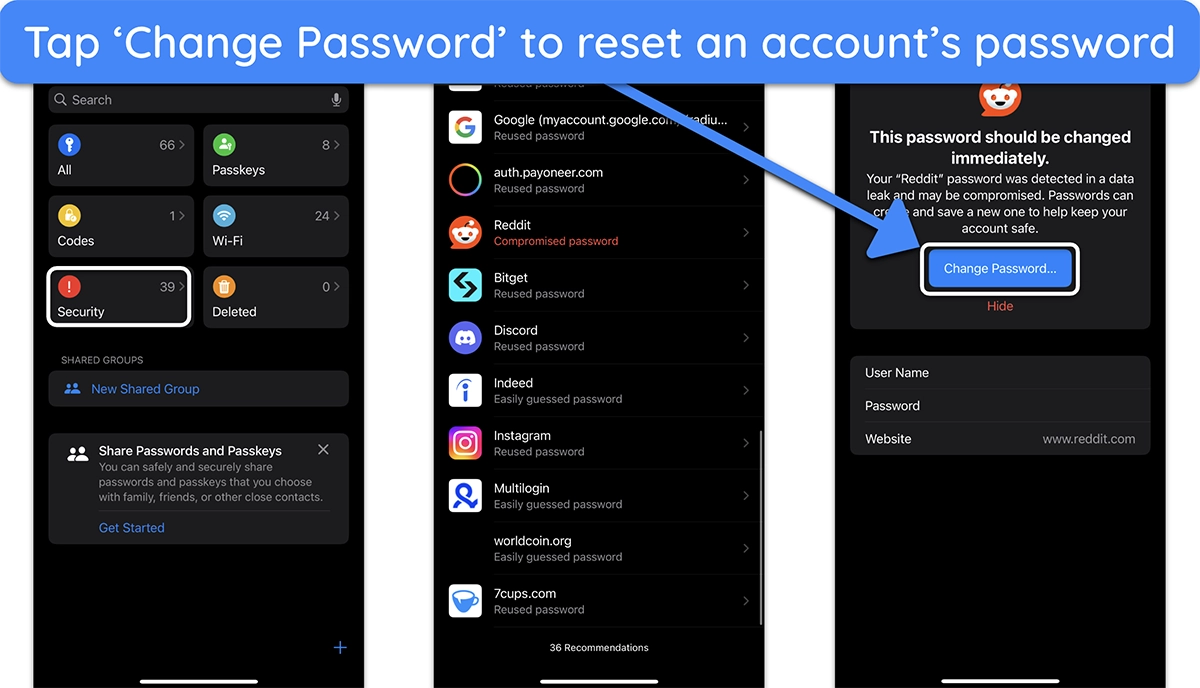
- Scan for leaked passwords — Open the Passwords app and tap ‘Security’ to see your potentially compromised passwords and change them immediately.
![Screenshot of iPhone's Password app showing a list of weak and compromised passwords and how to change password]()
- Check your calendar for spam entries — Hackers may add fake events with phishing links. Open ‘Calendar,’ find suspicious events, and delete them. Also, check ‘Accounts’ in settings to remove unwanted calendar profiles.
- Reset your iPhone as a last resort — If issues persist, back up important data, then go to ‘Settings,’ tap ‘General,’ then ‘Transfer or Reset iPhone.’ Choose ‘Erase All Content and Settings’ to wipe your device.
Tips to Protect Your iPhone From Getting Hacked
Hackers don’t always need malware to break into your iPhone. Weak settings, unsafe networks, and hidden exploits can give them access. These security tips will help you block their entry points.
- Avoid jailbreaking your iPhone — Jailbreaking removes Apple’s security protections, making it easier for malware and spyware to infect your device.
- Set a SIM PIN to block SIM swaps — Hackers use SIM swapping to hijack your phone number and bypass two-factor authentication. A SIM PIN prevents unauthorized transfers.
- Disable auto-join for WiFi networks — This stops your iPhone from connecting to rogue hotspots that can steal your data. Go to ‘Settings,’ tap ‘Wi-Fi,’ and turn off ‘Auto-Join.’
- Turn off Bluetooth when not needed — Keeping Bluetooth on allows hackers to exploit vulnerabilities. Disable it in ‘Settings’ or set AirDrop to ‘Contacts Only.’
- Enable Find My iPhone and Activation Lock — This prevents thieves from resetting or reselling your iPhone. Go to ‘Settings,’ tap ‘Apple ID,’ then ‘Find My’ to enable both.
- Use a passcode instead of Face ID in public — Attackers can unlock Face ID while you’re distracted or unconscious. A strong passcode adds an extra layer of protection.
- Restrict lock screen access to features — Disable Control Center, Siri, and Notifications on the lock screen to prevent unauthorized use. Adjust settings in ‘Face ID & Passcode.’
- Block USB access — Hackers can extract data through malicious accessories. Go to ‘Settings,’ tap ‘Face ID & Passcode,’ and disable ‘USB Accessories.’
- Use a reliable iOS antivirus — A good iOS antivirus can detect phishing links, block malicious sites, and alert you to security risks, preventing your iPhone from getting hacked.
The Best Antivirus Software to Prevent iPhone Hacks
- Norton — Norton blocks 100% of malware and phishing threats using advanced SONAR analysis. It secures WiFi networks, filters spam links, and detects malicious calendar invites. The Deluxe plan covers up to 5 devices for full protection.
- TotalAV — TotalAV’s Smart Scan finds security flaws and performance issues before hackers exploit them. WebShield blocks phishing sites, and its breach scanner alerts you to leaked passwords. It also prevents QR code phishing attacks.
- McAfee — McAfee monitors the dark web for stolen data and alerts you to breaches. It scans networks for unsafe WiFi, provides a secure VPN for anonymity, and offers credit monitoring in select countries.
FAQs on iPhone Hacks, Recovery, and Protection
Can my iPhone be hacked?
Can someone hack my iPhone remotely, through a website, or with a phone call?
How should I know if my iPhone is hacked?
My iPhone is hacked — what do I do?
What’s the best way to protect my iPhone from hackers?
Is there free security software for my iPhone?
Are iPhones more secure than Android?
Keep Your iPhone Safe From Hackers With the Best Software
If your iPhone gets hacked, you might not notice until it’s too late. Hackers can steal your data, track your location, or lock you out completely. Many attacks don’t even need malware — they trick you into clicking bad links or using unsafe settings. The best way to stay safe is to lock down your security and stay alert.
A good iOS antivirus helps by blocking phishing scams, unsafe WiFi, and tracking attempts. It won’t scan for malware like on a computer, but it stops threats before they reach your device. Paired with strong passwords and regular updates, antivirus software protects your iPhone from new and evolving cyberattacks.





Leave a Comment
Cancel