Data Leak: Unsecured Server Exposed Bing Mobile App Data
WizCase uncovered a massive data leak in the Microsoft Bing mobile app, through an unsecured Elastic server. There have been more than 10,000,000 downloads on Google Play alone, and millions of searches performed daily through the mobile app.
What’s Going On?
The WizCase online security team, led by white hat hacker Ata Hakcil, uncovered a massive data leak in a server owned by Microsoft logging data related to its Bing mobile app, available in both Google Play and App Store.
The investigation traced back to the Microsoft Bing App. Hakcil confirmed this by downloading the app and conducting a “Wizcase” search. He subsequently found his information, such as search queries, device specifics, and GPS coordinates on the server, demonstrating that the exposed data originated from the Bing mobile app.
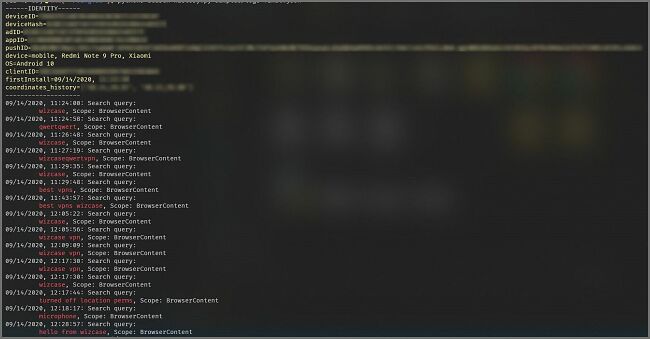
Logs of our search including all details related to the device
The exposed data includes:
- Search Terms in clear text, excluding the ones entered in private mode
- Location Coordinates: If the location permission is enabled on the app, a precise location, within 500 meters, was included in the data set.
While the coordinates exposed aren’t precise, they still give a relatively small perimeter of where the user is located. By simply copying them on Google Maps, it could be possible to use them to trace back to the owner of the phone. - The exact time the search was executed.
- Firebase Notification Tokens
- Coupon Data such as timestamps of when a coupon code was copied or auto-applied by the app and on which URL it was
- A partial list of the URLs the users visited from the search results
- Device (Phone or Tablet) model
- Operating System
- 3 separate unique ID numbers assigned to each user found in the data
- ADID: Appears to be a unique ID for a Microsoft account
- deviceID
- devicehash
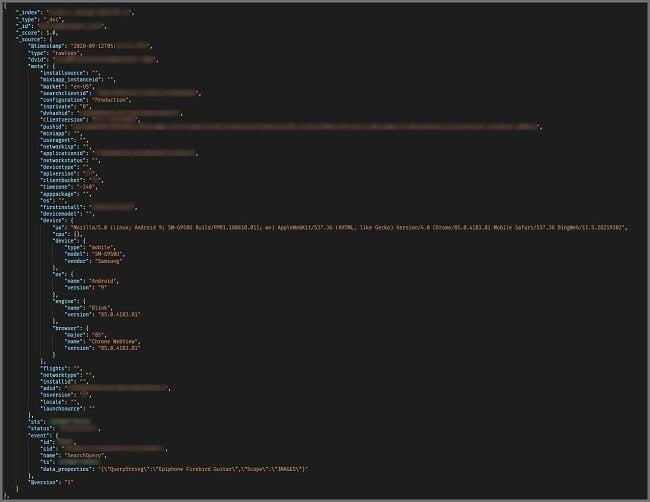
Logs containing some user information
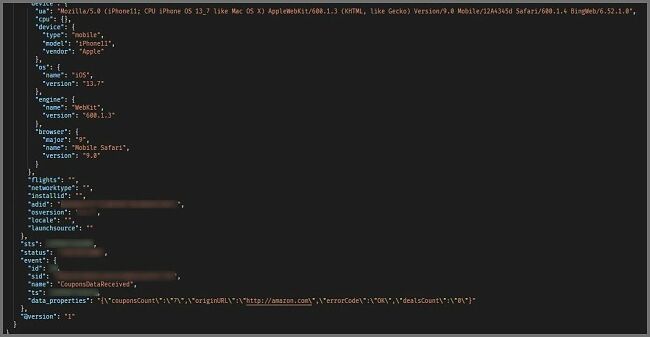
An example of a log related to coupons on the exposed server
Whose Data was Exposed and What Are the Consequences
Hakcil and his team discovered a 6.5TB server and saw it was growing by as much as 200GB per day. Based on the sheer amount of data, it is safe to speculate that anyone who has made a Bing search with the mobile app while the server has been exposed is at risk. We saw records of people searching from more than 70 countries.
According to our scanner, the server was password protected until the first week of September. Our team discovered the leak on September 12th, approximately two days after the authentication was removed.
After Hakcil confirmed the database belonged to the Bing app, the team alerted Microsoft on September 13th. They quickly responded to our message. We then reported the data leak to the MSRC – Microsoft Security Response Center and they secured it a few days later, on September 16th.
From what we saw, between September 10th – 12th, the server was targeted by a Meow attack that deleted nearly the entire database. When we discovered the server on the 12th, 100 million records had been collected since the attack. There was a second Meow attack on the server on September 14.
In addition to the Meow hackers, this data was exposed to all types of hackers and scammers. This could lead to a variety of attacks against users of the Bing mobile app.
Some of the potential threats include, but are not limited, to:
Blackmail: Whether it’s searching for adult content, cheating on a significant other, extreme political views, or hundreds of embarrassing things people search for on Bing. Once the hacker has the search query, it could be possible to find out the person’s identity thanks to all the details available on the server, making them an easy blackmail target.
Phishing Scams: If a hacker knows that someone is searching for something specific, like a vacation destination, pricing on jewelry, or looking at real estate locations, they can use that data to run a phishing scam explicitly built around their search history.
For example, the coupon data that was in the logs can let bad actors track shopping websites used by Bing App users, and if the formers manage to de-anonymize a user from previous search queries, etc., they could target the user with phishing scams specifically designed for that user.
Physical attacks and robbery: One of the data points revealed in this leak is a ping location for your phone or tablet. It doesn’t take a criminal mastermind to be able to use that ping to track your location. The cybercriminal will not only know the users’ daily routine, but they can also have information as to whether you have cash or expensive items with them, based on the search queries. For example, if one were to search for where to buy an expensive item or directions to store, the attacker could be ready to steal the item.
While investigating the server, our research team was able to find search queries from different types of bad actors.
The team could see the search queries entered by predators looking for child porn and the websites they visited following the search.
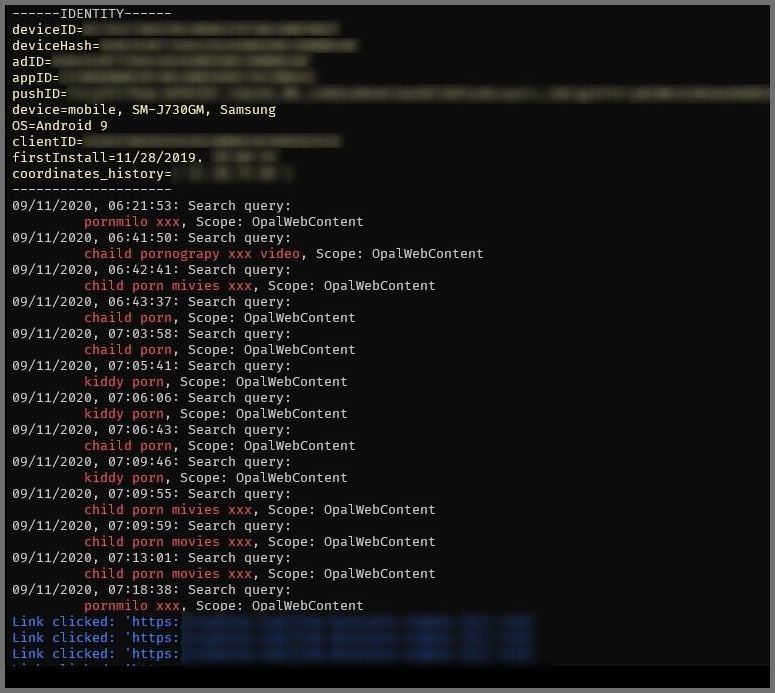
Search query from a predator including “clicked” URL
Not illegal but still worrisome, we also encountered search queries related to guns and interest in shootings, with search histories that included shopping for guns, and search terms like “kill commies.”
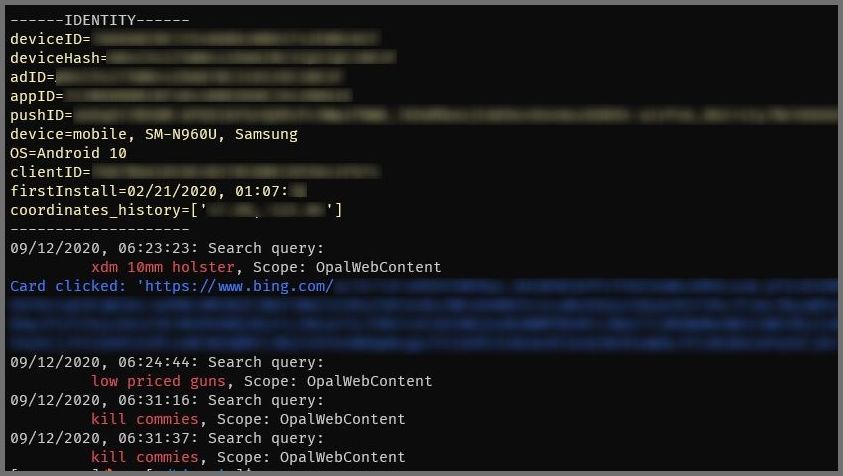
Search results for “guns” and “kill commies”
As ethical hackers, we don’t have the resources to identify these people and turn them over to the authorities. Yet, this discovery revealed how many predators and dangerous people are using search engines to find their next victims and what websites they are visiting.
Furthermore, we would like to take this opportunity to remind all parents to be careful when sharing pictures of their kids on social media. There are many people with bad intentions who browse these sites looking for kids’ image
A recording showing logs of users, exposing their device model, operating system, search queries, and the size of the database.
What Can I Do to Protect My Data?
If you use the Bing mobile app, you should be extra careful when opening emails from unknown senders. Even though a user’s email address isn’t included in the exposed data, there is enough user data for the hacker to find a person’s identity. Once they have a name, address, and place of employment, getting an email address isn’t that difficult. As a general rule, never click on a link that doesn’t come from a trusted source.
While it is generally accepted that search engines like Bing and Google have access to mountains of data, there is a reasonable expectation that they will secure that data.
One way to protect your data is to use a private search engine, such as DuckDuckGo, which doesn’t store any user data or search queries.
The location data comes from 3 sources:
- The phone’s GPS – unless you turned off GPS permissions
- The phone’s OS localization and language
- The connected Microsoft account, assuming its logged in.
To protect your identity against all three of these items, you will need to turn off the GPS permission on the Bing mobile app, and always keep a VPN connection while you’re online.
A VPN is a software that reroutes your internet connection to a remote server, giving you an IP address that isn’t connected to your actual location. While the location data isn’t coming directly from the IP address, Microsoft logs the IP addresses of users for up to six months, and the VPN would keep you anonymous in the event that data storage becomes compromised.
The problem with only keeping your VPN on for some browsing is that it gives bad actors the opportunity to view the connection history thanks to the unique IDs linked to your connection. When they see you are connecting from one country in the morning and another country in the evening, it won’t be difficult to determine which one is the VPN and which one is your actual IP address, so using a VPN becomes pointless if you are not consistently using it.
However, because of the phone’s localization, there will still be general geographical locations such as “en-US” or “fr-FR.”
We also recommend that you download reliable antivirus software that has anti-phishing protection.
Who is Wizcase?
WizCase is one of the biggest international online security websites, with content translated to 30 different languages. We provide tools, tricks, and best practices for online safety and security. This includes detailed VPN reviews and tutorials.
Our online web security team of White Hack hackers have uncovered some of the biggest data breaches, including unsecured webcams and dating site scandals.
Not only do we release our reports to the public, but we disclose it to the company as well, allowing them to secure their serves and creating a more secure environment for everyone.




Leave a Comment
Cancel