The Top 15 Biggest Hacking Attacks Since 2000
Cybercrime and online security have become one of the most significant social issues in the 21st century.

Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
The 15 Biggest Hacking Attacks!
1 WannaCry
The online profile of so-called ransomware has grown tremendously within the last couple of years. Using phishing methods, it freezes or takes control of a system, and the perpetrators demand ransom in Bitcoin.
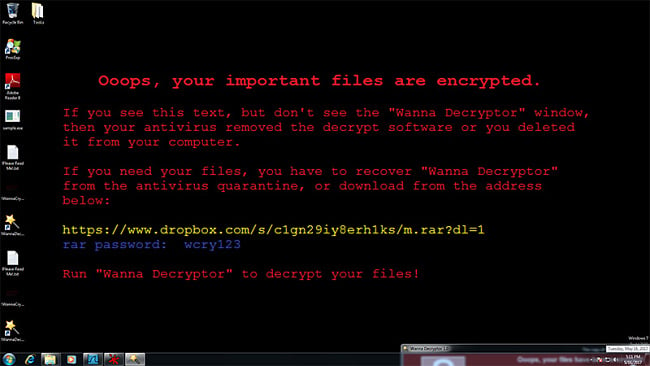
In days, thousands of organizations and business from 150 countries, including the UK’s National department of health services (NHS), were locked out their networks by the Wannacry encryption. The attackers demanded a hefty sum of money to unlock the set code.
2 The Bangladesh Bank Cyber Heist
Noted for the manner in which the hackers bypassed the IT systems of the Bangladesh Bank.
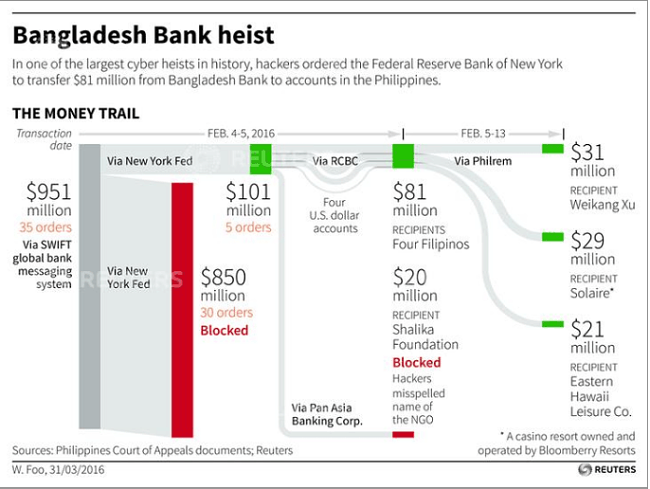
The criminal gang behind this had intended to withdraw close to $850 million before a simple spelling error aroused suspicion. The culprits still made away with approximately $81 million, of which only around $18 million has been recovered, and have previously been linked to attacks in other Asian Banks.
3 Mt Gox Bitcoin Exchange
There is a multitude of bitcoin exchanges or sites where you can purchase Bitcoin. In February 2014, the Mt Gox exchange, the largest in the world at the time, suddenly stopped trading.
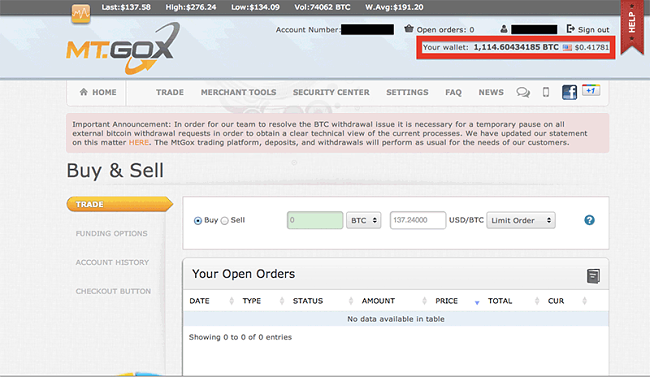
French developer, Mark Kerpelẻs, who purchased Mt Gox in 2001, was later arrested for fraud and embezzlement, although not directly related to the bitcoin theft.
4 Spamhaus
Spamhaus is one of the largest anti-spam apps in the world, keeping a block list of the servers known to be the source of malicious content.
5 PlayStation Network
In April 2011, the LulzSec syndicate of hackers breached the Sony PlayStation Network.
6 CitiGroup
In 2011, this cyber-attack on the Citigroup financial services exposed the weak security in the organization’s online platforms. Hackers found a backdoor giving them access to valuable, private data.
7 Stuxnet
There are several documented cases of malware used by the government for a specific military objective.
One example is the ‘logic bomb’ allegedly released by the CIA, and another is Stuxnet; a worm discovered in 2010. It was specially engineered to attack and infect the industrial controllers of Siemens, infecting 200,000 computers, destroying at least 1000 machines, and wiping out a fifth of the nuclear capabilities of Iran.
8 Conficker
Conficker is an infamous and strange piece of malware. Uncovered in 2008, no one exactly knows where it came from or who designed it. Difficult to eliminate, it continued infecting and destroying systems worldwide.
9 Iceman
Working as an IT consultant by day, Max Ray Butler was well respected in his field. However, by night, he acted as an infamous hacker known as ‘Iceman.’

10 Operation Get Rich
Commonly, renowned retailers living in the US are targeted through a series of serious hacks, as perpetrators aim to steal customer debit and credit card details to sell on.
Such attacks run by Albert Gonzales, together with his criminal gang, used what we call ‘SQL injections’ to exploit the weaknesses of an unsecured public or company WiFi.
11 Operation Shady RAT
Operation Shady RAT is the name given to describe a series of ongoing cyber-attacks targeting 74 various organizations in 14 different countries. The World Anti-Doping Agency and IOC were targeted before the Olympic games of 2008, and although fingers were pointed towards China, no one knows who was really behind these attacks.
We do know they used the same remote access system approach to gain control of its victim’s computers.
12 Estonia DDoS
In Estonia, April and May 2007, digital espionage ‘spilled over’ and became open cyber warfare. In one week, waves of DDoS attacks went on to affected government servers, including those involved in education, media, and banking. Within days, it had crippled the entire economy, daily life, and distribution of public services.
These attacks prompted military organizations everywhere to revise the importance of their network security.
13 Sven Jaschan/ Delta Airlines
German student, Sven Jaschan, carried out one of the world’s most devastating hacks from the comfort of his bedroom. Aged 18 and still living in his parent’s home, he’s credited for developing the Sasser worm. It’s a self-distributing and replicating virus that destroyed vulnerable operating systems from Windows.
Delta Airlines was hugely hit and had to cancel a lot of its transatlantic flights. He was eventually caught after a mysterious tip-off, but by that time the virus had caused more than 500 million dollars’ worth of damage.
14 MafiaBoy
Another teenager led cyber-attack where a troubled genius decided to launch massive DDoS attacks. The perpetrator, Micheal Calce, was able to infiltrate Yahoo, Amazon, CNN, Fifa.com, and eBay.

15 Melissa Virus

What is Hacking and Who is Behind It?
Hacking is the unauthorized access to a network or computer and is usually committed for financial gain, to extract data, or cause damage. From undercover government spies, naughty teens, disgruntled political entities, and petty crooks, anyone with the inclination and knowledge can hack a system.
From the mischievous youth with talent to waste to organized cyber terrorists looking to make a profit, the last ten years have seen a surge of hacking cases. These attacks cause damage to businesses and governments, eventually raising the standards of living. But how can you secure your device and online activities from such threats?
For the best defense against cybercrime, we recommend using a VPN.
In addition, keep your system up-to-date, ensure that your anti-virus, firewalls, etc., are on, and be wary of suspicious websites and content.
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.




Leave a Comment
Cancel