BREACH: French E-commerce Site Customers Exposed to Identity Theft After Data Leak
WizCase found an open Kibana interface that works with the Elasticsearch engine of BazarChic, a French e-commerce site. This exposed server, which has already been reported to BazarChic and closed, leaked personal information about customers, including email addresses, passwords, and partial credit card details.
BazarChic, a member of the Galeries Lafayette Group, specializes in clearance sales of high hand brands.
What’s Going On?
Our team of white hat hacktivists at WizCase was able to access what seemed to be private customer data through an unsecured database. The breach, which was discovered through an insecure configuration in the Kibana interface for the Elasticsearch engine, exposed potentially sensitive customer data.
The data that was found on the server includes:
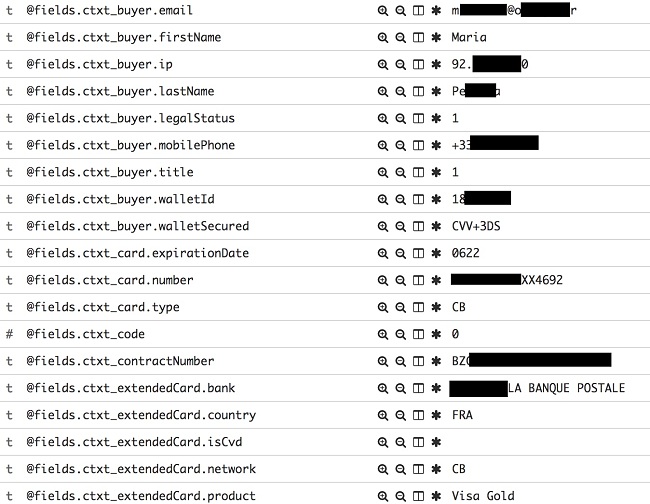
- Customers’ full name
- Billing address
- Phone Number
- Users’ BazarChic password
- IP address
- Last 4 digits of credit card
- Credit card expiration date
- Details on the customer’s device type, device ID, app version, screen size, OS version, etc.
Example of the personal customer data we were able to access

Whose Data is Available
Since the database seemed to log users every time they logged in, and not just unique entrances, it was hard to pin down an exact number of users affected. However, we can say that thousands of visitors were logged into the system since January 2019.
While most of the data remained on the server since the beginning of 2019, financial details appeared to be deleted on a monthly basis. We also determined that not every transaction was logged on this server, it seems that only failed payments attempts were stored here.
The data that was found is a potential gold mine for hackers and identity thieves. The possible risks to the BazarChic user include:
- Identity theft: The PIIs disclosed in the leak could be used by someone trying to impersonate individuals in situations where a company requires any of these private details to identify users (date of birth, address, phone, last 4-digits of their credit card, etc).
- Account takeover: Once the hacker has an Email address and password they can simply log in to the account, change the shipping address and make purchases with the credit card on file. They could also do any action within the site which the user is able to do, like change his details, communicate with the site on behalf of the user, purchase goods, close the account, complain, etc.
- Unauthorized credit card use: Because the credit cards in the leaks are partially masked and with no CVVs, it would be more difficult to use beyond the scope of the site. However, with all the PII that the hacker can find here, including the partial credit card information, they can gain access to other accounts the user has on different sites and get the full credit card details.
![Screenshot of BazarChic redacted information]()
- Privacy risks, theft, and scams: Not only does an attacker have emails and phone numbers but also PIIs that he can use to obtain credibility.
- Targeted phishing scams: A popular phishing scam is to send the target an email, and using their password as proof that you were hacked, they will then demand that you pay a ransom or suffer the consequences.
- Password Access: Since passwords are often reused, hackers could have access to accounts on multiple sites. There are online tools that can scan for social media accounts based on the email address. If the customer has been reusing the password and/or the parallel site’s password policy isn’t up to date with password reuse risks (e.g. not allowing the top commonly used passwords to be used – which can at least sometimes prevent password reuse of common passwords) there’s a good chance that the attacker could gain access to more accounts for this customer, by trying to log in with the same email and password.This is one of the many reasons that you should have a strong and unique password for each site. You can use a password manager to help you manage all of your accounts.
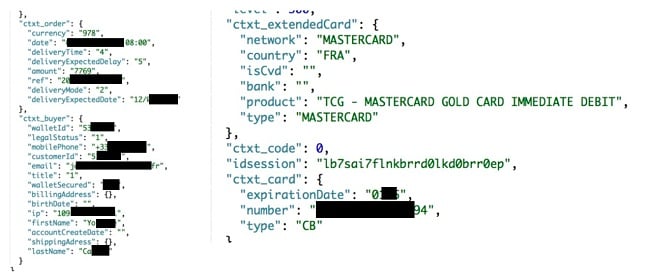
Example of the leaked credit card information we were able to find
If a hacker were to access the BazarChic data through the Kibana interface, they would easily be able to access system data that should remain private. While not all the info found will be directly beneficial to finding an exploit but it will surely help in performing reconnaissance on the system for more elaborate hacks.
In any case, best practice is to expose the minimum amount of data about the underlying technology and backend system. The reason for this is that there are different known exploits & vulnerabilities for specific frameworks, technologies and platform versions. Identifying that a given site is using some unpatched software in its infrastructure which could be attacked using one of these exploits is easier if such logs as the ones seen in the leak are available.
In the Kibana interface, we witnessed logs that indicate a brute force attack to the login mechanism. This tells us that what happens to the system is reflected in this database and can be used against it.
This kind of system data could also include private data about the users in some cases (e.g. an HTTP request showing a POST request with a user’s email & password).
- HTTP Traffic: This can contain details about BazarChic’s internal resources and sensitive data that has been passed on to the back end of the systems. It can be a privacy risk and a gateway to parameter tampering attacks and more.
- SQL Queries: This can reveal information about the underlying structure of the website and can assist with SQL injection attacks and more.
- Web Server Folder Structure: Knowing how the folders are stored on the server can help a hacker attack the web framework, path traversal, and more.
This data could be used to attack or map the site and discover more resources from the web application.
How Did It Happen and How Can it Be Prevented?
We were able to identify an open Kibana interface with no authentication that contained sensitive information. This is a known issue in setting up Kibana and Elasticsearch servers – the systems are intentionally made to be internal and with no default authentication (since they are meant to be used for analysis & activity logging from within a company’s internal network). However, they are sometimes set up in a way exposing them to external networks and the internet, thus causing such leaks.
To protect this server, BazarChic may first have to prevent it from being accessed from external sources and add a password authentication mechanism to the Kibana interface. There are several ways to add these security measures, depending on the implementation. In such cases, it’s also important to remember to change the default user & password.
It’s also crucial to assign user roles for those with access rights to the data and set correct privileges so that only certain people will have access to sensitive data.
Newer versions of Kibana should have security plugins & access controls already installed by default, so the server administrators only need to configure them properly.
An additional related line of defense would be to make sure that the server is running with encrypted HTTPS communication in order to prevent the data from being sniffed.
It’s also worthwhile to mention that logging sensitive data and saving it in clear-text should usually be avoided if possible.
We strongly recommend that if you logged into BazarChic since the beginning of 2019 to take some steps to secure your online identity. This includes:
- Change your passwords on other online accounts if it’s the same or similar to your BazarChic password.
- Look through your credit card transactions and make sure there are no extra charges.
- Don’t open links in emails unless you are sure that you know the sender.
Who is WizCase? Why Should I Trust You
Wizcase is an international online security website that is translated into 30 languages. While our focus is on VPN reviews, comparisons, and tutorials we also have a dedicated Security Research Team. Once we uncover a data leak, we first contact the company and give them time to close their leak before releasing the data to the public.




Leave a Comment
Cancel