Thousands of Artists and Customers Exposed in Online Artwork Management Platform Data Breach
WizCase’s team of ethical hackers, led by Ata Hakçıl, has found a major breach in online art retail platform Artwork Archive. This breach compromised users’ names, surnames, email addresses, physical addresses, and other sensitive information. Thousands of artists, collectors and their customers were left vulnerable. There was no need for a password or login credentials to access this information, and the data was not encrypted. The breach has since been secured. Artwork Archive stated that “the breach was addressed immediately and there is no other evidence that this was accessed by anyone other than the third-party cybersecurity company.”
What’s Happening?
Artwork Archive is a US-based online art management website. The site caters to both individual artists and art organizations trying to manage, buy and sell art online. It has thousands of clients and users,including luxury department store chain Neiman Marcus, Ivy League school Brown University, and noted artists such as Robert Farber and Oliver Jeffers.
What Data Was Left Vulnerable?
Our team of ethical cyber researchers discovered a misconfigured Amazon S3 bucket belonging to Artwork Archive containing over 200,000 files and 421 GB of data. The files were dated from August 2015 to the time of discovery. The bucket left over 7,000 artists, collectors, and galleries vulnerable, and potentially their customers too. PIIs exposed included full names, physical addresses, email addresses, and purchase details.
The majority of PIIs came in the form of over 9,000 invoices for the sale of artwork. These invoices contained different details depending on the seller, but most included the PII of the artist themselves at-minimum.
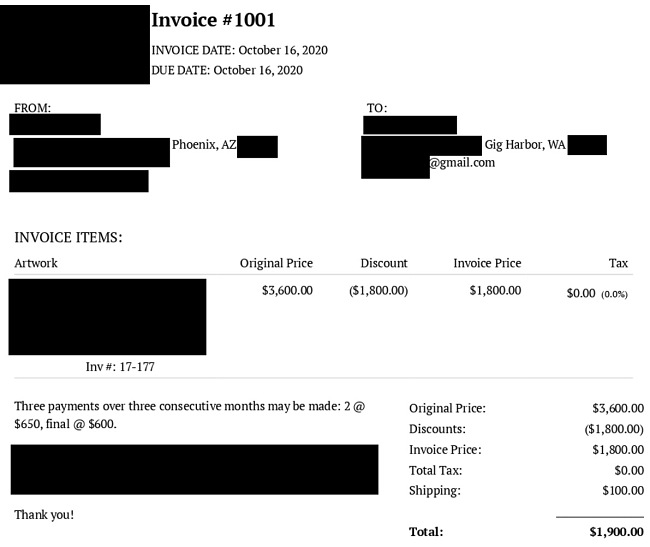
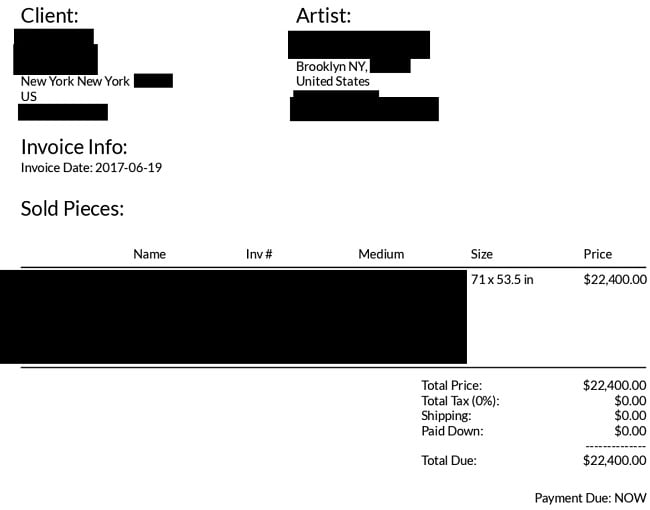
Another major source of exposed PII was from “exported contacts.” These were usually contacts an artist added to Artwork Archive via their contact management feature and included art institutions, individual artists, art collectors, friends, and family. Vulnerable information from exported contacts included full names, phone numbers, email addresses, city/country, and (if applicable) the company they’re affiliated with.
There were also thousands of sale and income reports related to the sale of artwork and the revenue gained from these sales. While these did not reveal additional PIIs, this was sensitive financial information. These reports made it clear that the platform is managing sales in substantial amounts of money, with some pieces being sold for tens of thousands of US dollars.
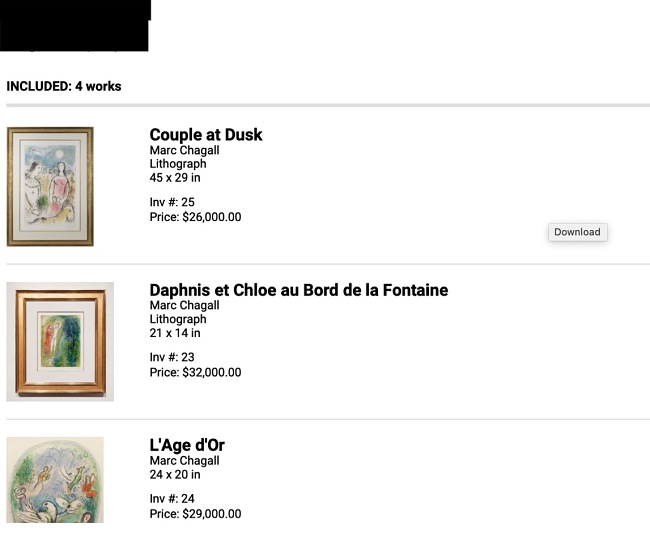
Additionally, a number of inventory reports in the leak. These inventory reports list artwork owned by specific artists, buyers, and galleries. Artworks in these reports include pieces by notable artists like Jean Miro and Marc Chagall.

What Are the Risks and How to Protect Yourself
Theft and Fraud: The abundance of artist, order, and customer details exposed could allow bad actors to pose as an artist and sell forged artwork to customers. Conversely, the contact information of artists could be used to perform refund or overpayment scams, in which a fake buyer requesting the artist wire funds back to them due to writing a check for more than the artwork is worth. While the wire transfer is processing, the check will bounce, leaving the artist to pay for various fees in addition to money already lost. Additionally, the artist could have their actual pieces stolen, as their locations were found in inventory reports.
Phishing: With so many PIIs from art buyers and artists exposed, hackers could target them with SMS messages and emails masquerading as Artwork Archive or another website they purchased artwork from in order to get them to enter financial information on a malicious website.
Corporate Espionage: With artists’ PIIs, income reports, sales reports, and client lists exposed, attackers or rival sites or artists could use the data to harm their competition, such as stealing clients from Artwork Archive themselves.
Unfortunately, the above list is not comprehensive, and cybercriminals are always generating new methods to exploit anyone vulnerable on the Internet.
For future purposes, we recommend always inputting the bare minimum of information when making a purchase or setting up an online account. The less information hackers have to work with, the less vulnerable you are. If you are an artist and worried about fake buyers contacting you, be sure to never divulge any personal information with new clients and never wire money to a buyer you are not familiar with.
Though most email clients have methods to block spam and phishing attempts, they are not 100% effective. When receiving an unexpected email from a seemingly trustworthy source, do not open any attachments. Phishing emails often use scare tactics to force users to open the attachment. If you are ever unsure about an email from a trustworthy company, give them a call. This will usually let you verify whether the attachment is legitimate or not. A good antivirus program can also aid in protection from malware, trojans, and other dangers.
In cases of potential corporate espionage, companies and in this case artists should warn their clients of the breach as soon as possible to ensure their clients’ vigilance and safety.
Why Should I Trust WizCase?
WizCase is a widely popular web security platform offering advice and tips for thousands of readers every week. Translated into over 30 languages, our website has gained the trust of a wide number of people worldwide. Our team regularly discovers new data breaches across the internet and contacts the companies responsible for them prior to publishing any reports. We have found leaks and breaches affecting many different companies from news websites, to popular dating apps, and to the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel