Signs Your Smartphone is Hacked (+ How to Protect Yourself)
A smartphone is one of the most important tools in modern life. It helps you keep track of dates, stay in touch with loved ones, take pictures, and so much more. In certain parts of the world, a smartphone is almost essential for day-to-day life. As of June 2021, 3.8 billion people own a smartphone. Unfortunately, this popularity means smartphones are also prime targets for hackers who want to steal your data. They come up with new tricks and strategies to break into it every day, and sometimes, you might not even know your phone has been hacked. That’s why I’ve put together this list of signs your smartphone might be hacked. I’ve also included tips for protecting yourself and taking back control of your phone if it is hacked. However, some of these warning signs can have other, less dangerous causes. As a result, I’ve also included some tips on the first steps you should take if you spot a problem. It’s best to try those before going to the more drastic changes you’ll need to make if your phone is hacked. Whether your phone is hacked or just needs a little cleaning, I hope these tips and warning signs help you keep your phone data safe and secured. Be sure to keep this page bookmarked as a handy guide for phone safety.
How to Tell If Your Phone Has Been Hacked
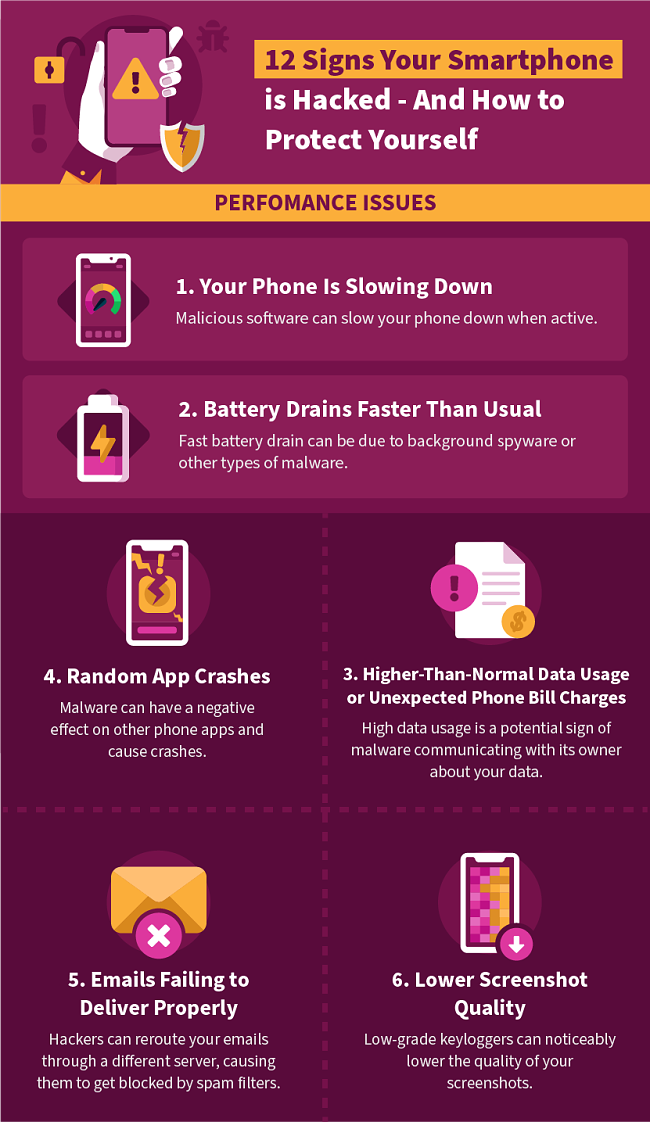
Changes in Performance
1. Your Phone Is Slowing Down:
One of the simplest signs of smartphone hacking is slowed performance. Malware running in the background can leave your device struggling to reach the speeds it once did. However, this performance drop can have other causes. For example, a recent software update can cause a similar slowdown, as can a phone with a full memory. If you download a lot of apps that drain processing power and bandwidth, this can also cause a slowdown. So, a slower phone with no other warning signs is not a cause for alarm. Before blaming hackers, it’s best to try freeing up space on your phone first and see if performance improves.
2. Battery Drains Faster Than Usual:
When your phone is hacked, malware or spyware running in the background can cause a more significant drain on its battery. It will also cause your phone to heat up more than usual. However, there are other factors that could cause this drain, such as running outdated software or using some battery-intensive apps. Social media apps like Facebook or Tinder or mobile gaming apps like Clash of Clans or Genshin Impact are common culprits for depleting battery life. Many of these types of apps can run in the background as well, causing further drain. Closing these apps frequently can help, and I recommend trying this before assuming your phone is hacked.
3. Higher-Than-Normal Data Usage or Unexpected Phone Bill Charges:
Malware and especially spyware will also cause spikes in data usage, usually by monitoring your phone’s activity and sharing that data via the Internet. If your phone bill ends up higher than usual as a result, this can cost you a lot of money as well. However, frequently streaming videos or music, downloading large files, or using mobile video conferencing like Skype or Zoom can also cause a spike in data usage. Check how much data your apps are using in your phone’s settings before calling your telecom provider.
4. Random App Crashes:
Another sign of a hacked phone is when certain apps crash or fail to load at all. This is most concerning when multiple apps are crashing at random. If it’s only one app that crashes, the app itself is likely to blame.
5. Emails Failing to Deliver Properly:
In some cases, a hacked phone will have its email configuration changed. This can mean your emails get relayed to an unauthorized server then blocked by the recipient’s spam filters. Fixing your email configuration can be a complex process, but there are guides for both Android and iPhone that can help walk you through it. However, make sure you’ve followed our tips for getting rid of spyware and malware later in the article first. If you reconfigure your email without getting rid of the software that changed it in the first place, it’s possible the configuration will get changed again.
6. Lower Screenshot Quality:
A specific type of malware, called a keylogger, can cause screenshots you take to be lower-quality than usual. This is only the case for poorly-made keyloggers, however.
Mysterious Actions

7. Strange Apps:
Sometimes, you’ll find apps on your phone that you don’t remember downloading. While this can be signs of spyware or other types of malware, this can also be an app your service provider or device manufacturer downloaded onto your phone during the latest update. If you spot an unknown app on your device, it’s best to google the app on your computer or another device to make sure the app is trustworthy.
Certain hackers might also use otherwise trustworthy parental control apps to spy on people. You should treat apps like Net Nanny, Kaspersky Safe Kids, Norton Family, and Qustodio with caution if you don’t remember downloading them.
Finally, strange apps might be a sign of your phone being jailbroken or rooted. Jailbreaking a phone allows a user to bypass official app stores. This allows you to download apps that aren’t allowed on or were removed from the app store. If your phone has been rooted and you didn’t do it, your phone is likely hacked. iPhone users should check for an app called Cydia, which is commonly used to download software on rooted and jailbroken devices. Android users should download an app called Root Checker which can scan your phone for signs of jailbreaking.
8. Phone Attempts to Access Strange or Malicious Websites:
If you use your phone on a network that blocks specific sites and networks, you might notice your phone attempting to access these sites without your permission. This is due to the hacker trying to force your phone to open these websites behind whatever you’re currently looking at. But the network blocks the attempt, keeping your phone safe, and leaves evidence that your phone might be hacked. Schools and businesses often have networks like these. If possible, stay connected to that network as long as possible while you attempt to remove any malware or spyware so it can keep blocking these access attempts.
9. Strange or Inappropriate Popups:
Like computers, certain types of malware will force pop-ups onto your phone. These pop-ups will demand you perform certain actions so the hacker can extract data from your phone. These pop-ups usually come while browsing the Internet but can also be unexpected notifications from other apps. For example, a Calendar app might send you a pop-up with a mysterious link for an event you don’t remember planning for. If you find yourself getting these pop-ups frequently, your device is likely infected with malware.
10. Texts or Calls You Didn’t Make:
Certain types of spyware and malware use your phone’s SMS to communicate with their server. Services like Cerberus can also use these outgoing SMS messages to perform commands on your phone, like take a picture or wipe your SD card. If your phone is sending SMS messages or making calls without your permission, it is likely hacked.
11. Password and Setting Changes:
A common trick that hackers will use when they get access to your phone is to change your settings and passwords to give them even more access to your sensitive data. They can also lock you out of social media accounts this way.
12. Phone Won’t Turn Off:
Certain types of malware can interfere with your phone’s shutdown process to keep it from shutting down properly or extending the time it takes to shut down. For example, whistleblower Edward Snowden exposed NSA technology that can keep your phone from fully shutting down. This lets them continue to spy on your phone. While it’s a high-level example, it shows that this sort of software exists and can be used maliciously. If you find your phone has difficulty shutting down, it might be hacked.
How to Protect Yourself and Take Back Control of Your Smartphone
Despite these dangers, you can still protect yourself and your data. I’ve compiled some tips that could help you with this. We’ll start with general tips then move onto specific advice for Android and iPhone users.
Firstly, keep your phone on you as much as possible. There are a variety of methods hackers can use to access your phone remotely. However, physical access is the easiest way to get into a phone, and you can prevent that by knowing exactly where your device is at all times.
Another good practice for data security is never clicking on links from sources you don’t trust. If you get an SMS message from an unknown phone number, do not click on it. It’s also a good idea to research an app before you download it, even if it comes from a trusted developer. Check reviews and any articles to see if they have security or privacy issues that might put you and your data in danger.
Do not give an app access to your phone’s location or photo gallery unless you need to. This includes trusted or official apps. Most apps don’t need these permissions to function; they just make it more convenient to use.
Finally, locking your phone with a password, PIN, or fingerprint can also help. I personally recommend securing your phone with a password or passphrase. PINs are comparatively easy to crack. Biometric options like fingerprints or iris scanners can be effective and easier to use than passwords. However, they can still be spoofed or cracked, and if they are cracked, you can’t change your fingerprint or iris the way you can change a password.
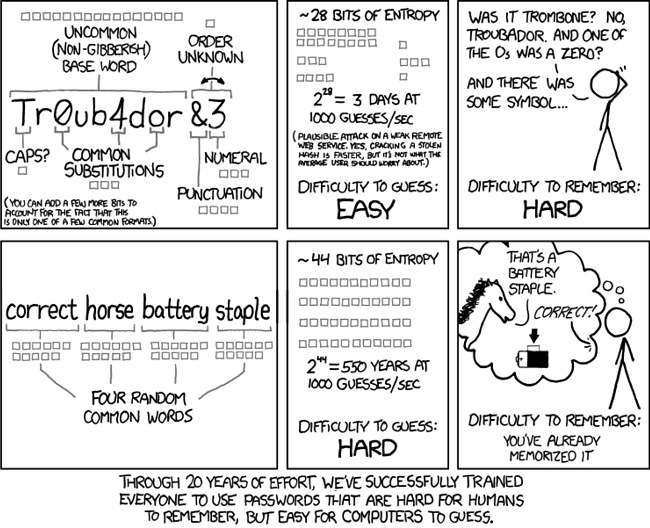
That said, the way we are traditionally told to create passwords is also not effective. The software that hackers use to guess your passwords are designed to find random strings of letters and numbers like “ghnfei39WHH9jjsbAxX82.” Such a password is easier than, say, Pa$$w0rd, but it’s still not the most secure method for creating a password. Worst of all, these passwords can often be easier for computers to guess and harder for humans to memorize. A string of unrelated words like “Supreme Mammal Oral Fragile” is both easier for us to remember and harder for computers to guess.
Tips for Android
There are a couple of pieces of security advice unique to Android. You can block apps from sources outside the official Google Play Store by going into your Settings, finding Apps, clicking on the icon in the top right corner of the Apps screen, selecting Special Access, and finding Install Unknown Apps. This won’t protect your phone from spyware or stop dangerous apps on the official store, but it’s still a wise choice. I also recommend installing AppNotifier to see when apps update or get installed on your phone. GooglePlay used to update you itself, but an update removed this feature. It’s also a good idea to keep Google Play Protect turned on so the Play Store can check any new app installed on your phone for malicious software.
Tips for iPhones
The Cydia app on iPhones can be a sign someone has installed spyware and keyloggers on your phone. This is especially dangerous for victims of domestic violence, as abusers can install these to keep track of their victims’ activities. Parental Control apps like Net Nanny or unapproved apps like mSpy are some of the most commonly-used apps used to spy on others. They can do anything, including constantly monitoring your location, recording audio from your device’s microphone, and logging everything you type on your device’s keyboard. Worst of all, these apps notify the purchaser if you remove the spyware app from your phone. This means whoever installed an app like that on your phone now knows that you did so. I recommend following our steps for resetting your Apple device to get rid of any jailbreaking done to it.
If you or someone you know might be in danger from an abuser using these methods, please consult these resources to find help before taking action:
In the US:
The National Coalition Against Domestic Violence
The National Resource Center on Domestic Violence
ASISTA
In the UK:
UK Government Resources
Refuge National Domestic Abuse Helpline
Galop LGBT+ anti-abuse organization
In European countries:
EU National Resources
In Australia:
Services Australia
Domestic Violence Resource Centre
How to Remove Spyware From Your Phone
Spyware can be some of the hardest to spot and remove malware out there. However, there are a few methods you can use. The first, and easiest, is to update your phone’s operating system. New software updates often close potential holes in your phone’s security, and updating your phone requires no work on your part. If updating your OS doesn’t work, you can manually remove mysterious apps by going into your App Settings and deleting them off your phone. This is the easiest to do for parental control apps like Find My Friends. If you’re still struggling with spyware after this, the final step is to perform a full factory reset. This will get rid of any jailbreaking or unauthorized apps from your phone. However, it will also delete all your phone’s data. So, I recommend backing up any important data like photos and notes in your notepad app before taking this step.
Keep Your Phone Safe Today With These Tips and Warning Signs
With how essential smartphones are to day-to-day life, it’s more important than ever to keep your phone data secure. I hope these warning signs and tips for keeping your phone safe will help protect you from anyone trying to steal your data. Sadly, the above warning signs are not comprehensive, and hackers work daily to find new ways to exploit your data. Like with other forms of security, the key to keeping your smartphone secure is vigilance. If you or someone you know suspects their phone has been compromised, pay attention to potential indicators and utilize these suggestions to safeguard your private information.





Leave a Comment
Cancel