What Is AES Encryption? What It Means & How Does It Work
AES encryption, or Advanced Encryption Standard, is a way to keep digital data safe. It scrambles your information into a code that only someone with the right key can unlock. It’s trusted worldwide by governments, companies, and even the apps and devices you use every day to protect sensitive data.
At its core, AES uses a secret key to secure your information. It’s fast, dependable, and incredibly secure, which is why it’s the go-to encryption method today. From emails to online banking, AES works behind the scenes to keep your data private and out of the wrong hands. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
Quick Summary: What Is the Advanced Encryption Standard (AES)?
AES is a type of encryption that keeps your data safe by using the same key to lock (encrypt) and unlock (decrypt) it. This is called symmetric encryption, and it’s simple and efficient while still being highly secure. It’s widely used because it works quickly and handles both small and large amounts of data easily.
AES protects data by dividing it into fixed chunks, called blocks, that are always 128 bits in size (basically 16 characters). To lock these blocks, you can choose from three key sizes: 128 bits, 192 bits, or 256 bits. Each key size creates a mind-boggling number of possible combinations:
- 128-bit key: About 3.4 followed by 38 zeros
- 192-bit key: About 6.2 followed by 57 zeros
- 256-bit key: About 1.1 followed by 77 zeros
To encrypt your data, AES uses a process called the Substitution-Permutation Network (SPN). It scrambles your data in a series of steps called rounds. The number of rounds depends on the key size: 10 rounds for a 128-bit key, 12 for 192-bit, and 14 for 256-bit. Each round adds layers of complexity, making it almost impossible for hackers to break.
You might wonder why there are different key sizes and why we don’t always use the strongest, AES-256. It comes down to how much power it takes to encrypt data. A stronger key, like 256-bit, uses more processing power and can drain your battery or slow down a device. That said, technology has made these differences so small that AES-256 is often the default choice for top-notch security.
Why Do We Use the AES Standard?
AES has been a trusted encryption standard for over 20 years because it’s fast, secure, and reliable. It was developed in 1998 by two Belgian cryptographers, Vincent Rijmen and Joan Daemen, and was originally called Rijndael. In 2001, the U.S. National Institute of Standards and Technology (NIST) chose AES to replace the weaker Data Encryption Standard (DES).
DES used a 56-bit key, which seemed strong when it was introduced in the 1970s. However, by 1999, researchers could crack DES in just 22 hours using the technology of that time. Today’s advanced computers can break it in less than six minutes. This made DES completely obsolete for modern encryption needs.
AES, on the other hand, is built to last. A 128-bit AES key has 3.4 x 10³⁸ combinations, which would take the fastest supercomputers an estimated 36 quadrillion years to crack. A 256-bit key is even more secure, with so many combinations that it’s impossible to break with current technology.
What makes AES even better is how fast it works. It can encrypt large amounts of data without slowing down, which is why it’s used for everything from online banking to secure messaging.
Where Is AES Encryption Used?
AES encryption is everywhere, from personal devices to global networks. Here’s where it’s commonly used:
- Messaging Apps — Apps like WhatsApp and Signal use AES to keep your conversations private and accessible only to intended recipients.
- Disk and File Encryption — Tools like BitLocker and FileVault use AES to secure files and entire disks, protecting them from unauthorized access.
- Cloud Storage — Services like AWS encrypt your data with AES, keeping it safe while meeting strict security standards.
- WiFi Networks — Modern WiFi security protocols like WPA3 use AES to protect data exchanged between your devices and the router.
- VPNs — Virtual Private Networks rely on AES to encrypt your internet traffic, ensuring your online activity stays private.
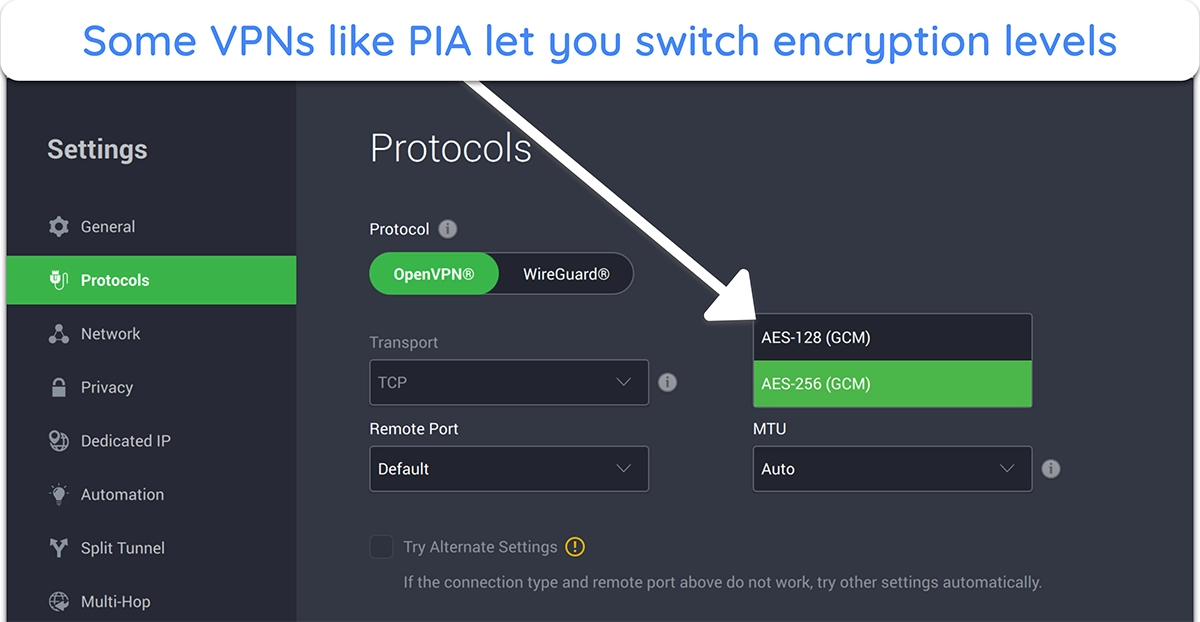
![Screenshot of how to switch between 128-bit and 256-bit encryption on PIA]()
- E-commerce Platforms — Online stores secure payment data with AES to protect your personal and credit card details during transactions.
- Banking Systems — Banks encrypt data on their platforms with AES, ensuring your account details and transactions are secure.
- Government Agencies — Governments use AES, especially with 256-bit keys, to secure classified communications and sensitive data.
- Healthcare Providers — Patient records are encrypted with AES to comply with privacy laws like HIPAA and ensure confidentiality.
- Mobile Apps — Many apps encrypt stored data with AES, protecting it even if your phone is lost or stolen.
AES Implementation Types
AES encryption can work in different ways depending on the needs of the application. These “modes of operation” determine how AES processes and secures data. The mode you choose affects how secure and efficient the encryption is. Here are the most common types:
ECB (Electronic Codebook)
This mode splits your data into chunks, called blocks, and encrypts each one separately. While it’s simple and allows parallel processing, it’s not great for large or repetitive data. That’s because patterns in the data can show up in the encrypted version, making it less secure.
CBC (Cipher Block Chaining)
In this mode, each block of data is combined with the encrypted version of the previous block before encryption. This creates a chain effect, making it much harder for attackers to spot patterns. The first block uses something called an Initialization Vector (IV), a unique starting value, to kick things off securely.
CTR (Counter)
CTR turns AES into a stream cipher by combining a counter (which changes with every block) and a unique nonce (a number used only once) as inputs. The output is then combined with your data to create the encrypted version. CTR is fast, works well for parallel processing, and is ideal when you need random access to encrypted data.
OFB (Output Feedback)
Like CTR, OFB turns AES into a stream cipher but works a bit differently. It uses an IV to generate a keystream (a random-like sequence), which is then combined with your data to encrypt it. OFB has to process each block in order, so it’s slower than CTR. If there’s an error in transmission, it can affect the following blocks.
CFB (Cipher Feedback)
CFB is similar to OFB but works on smaller pieces of data, like bytes. It encrypts the IV and combines the result with your data to create the ciphertext. Each new piece of encrypted data is used to help encrypt the next piece. Like OFB, it requires sequential processing, which can slow things down.
GCM (Galois/Counter Mode)
GCM is a more advanced mode that does two things at once — encrypts your data and checks it for integrity to make sure it hasn’t been tampered with. It’s very fast, supports parallel processing, and is widely used in secure network protocols like HTTPS.
Features of AES Encryption
What makes AES encryption so effective is its combination of strong security and practical design. It’s built to handle modern challenges while staying fast and efficient. Let’s break down the features that make AES the gold standard for encryption:
- Symmetric Key Encryption — AES uses the same key to lock (encrypt) and unlock (decrypt) data. This makes it simpler and faster compared to methods that need two different keys.
- Fixed Block Size — It encrypts data in chunks called blocks, each 128 bits in size (about 16 characters). This fixed size ensures consistency and speed in processing data.
- Variable Key Lengths — You can choose from 128-bit, 192-bit, or 256-bit keys. Longer keys are more secure but require more computing power to use.
- Substitution–Permutation Network (SPN) Structure — AES scrambles data by substituting and rearranging it in multiple steps. This structure makes it incredibly hard to crack.
- Multiple Encryption Rounds — AES encrypts data in 10, 12, or 14 rounds, depending on the key size. Each round adds complexity, making the data virtually unbreakable.
- Resistant to Hacking — AES is designed to resist common hacking methods like brute-force attacks. Its complexity ensures your data stays secure against modern threats.
- Efficient Performance — AES works quickly and doesn’t need much processing power. It’s efficient for both powerful servers and smaller devices like phones.
- Open Standard — AES’s algorithm is public, meaning anyone can use or review it. This openness builds trust and allows for widespread adoption worldwide.
How Does AES Encryption Work?
AES encryption works by transforming readable data into a secure, scrambled format that only someone with the correct key can unlock. Here’s a detailed breakdown of how the process works:
Step 1: The Key
The core of AES encryption is a key, which is like a long password that tells the encryption algorithm how to scramble the data. AES can use three different key sizes: 128-bit, 192-bit, and 256-bit. The larger the key, the stronger the encryption. However, 128-bit AES is already very secure and is commonly used.
The key itself is a randomly generated sequence of bits, and its randomness is what makes AES secure. For instance, a 128-bit key has 2^128 possible combinations, which means a brute-force attack would take an unimaginable amount of time to succeed, even with the most powerful computers.
Key Schedule Process:
- The key goes through an expansion process to create several different round keys.
- Round keys are derived from the original key.
- Each round key is unique and used in every round of encryption to add an extra layer of security.
Step 2: Breaking Data Into Blocks
AES is a block cipher, meaning it encrypts data in fixed-size chunks or blocks. The block size for AES is always 128 bits (16 bytes). If your data is longer than that, AES splits it into multiple 128-bit blocks and encrypts each one separately. If your data is shorter, padding is added to make it fit.
Padding Process:
- Padding is needed because AES requires a full 128-bit block.
- Common padding schemes include PKCS#7.
- Padding adds bytes to the end of data until it fits neatly into the block size.
The blocks are treated as a 4×4 matrix of bytes. This matrix-based structure is what allows AES to carry out its encryption steps systematically. All operations are performed on the rows and columns of this matrix.
Step 3: SubBytes — Substituting Bytes
Once your data is divided into blocks, AES begins with a process called SubBytes. It uses a substitution box (S-box) to replace each byte in the data block with another specific value. The S-box is a predefined, non-linear table that helps achieve confusion.
Key Features of SubBytes:
- The S-box is resistant to linear and differential cryptanalysis.
- Each byte in the block is replaced with its corresponding value from the S-box.
- This step makes the data more unpredictable.
The S-box used in AES is constructed mathematically to be highly resistant to attacks, which is why it’s an essential part of making AES secure.
Step 4: ShiftRows — Rearranging Rows
After substitution, AES performs a ShiftRows step. Here, each row of the 4×4 block of data is shifted to the left by a certain number of positions. Here’s how ShiftRows Works:
- The first row stays the same.
- The second row shifts left by one byte.
- The third row shifts left by two bytes.
- The fourth row shifts left by three bytes.
This step achieves further diffusion, which ensures that bits from the input data affect as many parts of the output as possible. The result is that bytes from the same column are no longer grouped together, making it far more difficult for an attacker to determine the original structure of the data. The goal here is to spread the data across the entire block, making the patterns even more obscure.
Step 5: MixColumns – Mixing Columns
Next, we have the MixColumns step. Each column of the block goes through a mathematical transformation involving Galois Field multiplication. This means that the bytes in each column are combined and multiplied by fixed values using operations defined in a special finite field.
This adds further diffusion, ensuring that a small change in the original data leads to major differences in the encrypted data. By combining bytes from different rows, MixColumns helps spread the influence of each byte throughout the block.
MixColumns is skipped in the final round of AES because, at that point, further mixing would not significantly increase security. Instead, skipping it makes decryption easier and more efficient without compromising the strength of the encryption.
Step 6: AddRoundKey – Using the Key
Every block goes through a step called AddRoundKey. In this step, the block is combined with a part of the encryption key, known as a round key. This is done using a bitwise XOR operation, where each bit in the data block is combined with a bit from the round key.
The XOR operation is crucial because it’s simple but effective at scrambling data. If you have two bits, XOR will output 1 if they are different and 0 if they are the same. This operation is both fast and easy for a computer to perform, making it ideal for encryption processes.
The round key itself is generated using the Key Schedule we discussed earlier. Each round key is unique, and combining it with the data in every round means that without knowing the original key, it’s virtually impossible to decrypt the data. The AddRoundKey step is where the secret ingredient (the key) directly influences the data, which makes AES extremely secure.
Step 7: Rounds – Repeating the Process
The steps above (SubBytes, ShiftRows, MixColumns, AddRoundKey) are repeated multiple times, depending on the key size:
- 128-bit key: 10 rounds
- 192-bit key: 12 rounds
- 256-bit key: 14 rounds
Each round adds more complexity to the data, making it increasingly secure. The more rounds, the more difficult it becomes for someone to reverse-engineer the encrypted data without the correct key. In the final round of encryption, the MixColumns step is omitted to simplify the decryption process while still ensuring the data is secure.
Step 8: The Encrypted Data
After all the rounds are completed, what you have is a scrambled version of your original data that looks like complete gibberish. Without the correct key, decrypting this data is practically impossible.
AES encryption turns your data into a ciphertext that can only be turned back into readable data using the exact same key and the reverse process. The reason AES is so effective is because each step makes the data as different from the original as possible, while still allowing someone with the key to reverse the process.
Decryption: Reversing the Steps
To decrypt the data, AES performs all these steps in reverse order. The process begins with the encrypted data and the key, and it undoes each round step by step, transforming the encrypted data back into its original form. Each reverse step mirrors its encryption counterpart:
- Inverse SubBytes: The substituted values are replaced with their original bytes using an inverse S-box.
- Inverse ShiftRows: The rows are shifted back to their original positions.
- Inverse MixColumns: The columns are transformed back using an inverse mathematical function.
- AddRoundKey: The round key is XORed with the block again to retrieve the original data.
The key must match exactly, down to every single bit; even a slight difference will result in a failed decryption. AES decryption is essentially a carefully planned reversal of the encryption, ensuring that only someone with the correct key can decrypt the data.
What Is the Difference Between…
Symmetric vs. Asymmetric Encryption
In symmetric encryption, the same key is used to both lock (encrypt) and unlock (decrypt) the data. It’s fast, efficient, and great for handling large amounts of data. But there’s a catch—you need a secure way to share the key with others, which can be tricky.
With asymmetric encryption, you have two keys: a public key and a private key. The public key is shared with anyone who wants to send you encrypted data, but only your private key can decrypt it. This makes asymmetric encryption more secure for sharing data, but it’s slower and introduces more latency — it’s better suited for smaller amounts of information.
AES vs. RSA
RSA is an encryption method that uses two keys: a public key to encrypt data and a private key to decrypt it. RSA is slower than AES but is great for securely sharing small pieces of information, like encryption keys or verifying digital signatures. Its keys are much longer (e.g., 2048 bits) to ensure strong security.
AES, on the other hand, uses the same key for encryption and decryption. It’s much faster and better suited for encrypting large amounts of data, like files or entire communications. In many cases, RSA is used to encrypt the AES key, combining the strengths of both methods for maximum security and efficiency.
AES vs. TKIP
TKIP (Temporal Key Integrity Protocol) was developed as a quick fix to improve security on wireless networks that used WEP (Wired Equivalent Privacy). It added features like key mixing and message integrity checks but still relied on RC4 encryption, which is outdated and vulnerable.
AES, in contrast, is far stronger and is now the standard for securing wireless networks through WPA2 and WPA3 protocols. AES not only provides better security but also performs more efficiently, making it the preferred choice for modern WiFi encryption.
Advantages of AES Encryption
AES encryption stands out for its reliability, speed, and versatility. Here’s why it’s trusted worldwide:
- Strong Security — AES uses key sizes of 128, 192, or 256 bits, making it highly resistant to brute-force attacks. Even the lowest level, AES-128, would take an estimated 1 billion billion years to crack using brute force.
- High Performance — AES is incredibly fast at both encrypting and decrypting data, making it perfect for tasks that need quick processing, like secure file transfers or live communications.
- Versatility — You can use AES on almost any device, from tiny smartphones to massive servers. Its efficiency and low memory usage make it adaptable to all kinds of systems.
- Global Standard — AES is trusted worldwide and is used in everything from online banking to personal data protection. Its widespread recognition means it’s reliable and proven.
- Ease of Implementation — AES’s design makes it simple to integrate into software and hardware. Developers can add it to systems without needing overly complex setups or specialized tools.
- Low Resource Consumption — Despite being highly secure, AES doesn’t hog resources. It works smoothly even on devices with limited processing power, like IoT gadgets or older computers.
Does AES Encryption Have Security Flaws?
AES is one of the most secure encryption methods available, but no system is entirely without vulnerabilities. Here are some potential attack methods that researchers have studied:
Related-Key Attacks
Related-key attacks analyze how AES behaves when different but closely related keys are used. Researchers have found theoretical vulnerabilities in AES-192 and AES-256 under specific conditions. However, these attacks require highly unrealistic scenarios, so they’re not a real-world threat for properly implemented AES systems.
Side-Channel Attacks
Side-channel attacks don’t target AES itself but instead focus on how the system processes encryption. Attackers monitor things like power usage or electromagnetic signals from the device running AES to guess the secret key. This type of attack depends on weaknesses in the implementation rather than the AES algorithm, and it can be mitigated with proper safeguards.
Known-Key Distinguishing Attacks
Known-key distinguishing attacks involve trying to tell encrypted data apart from random data when the attacker already knows the encryption key. While researchers have tested these attacks on simplified versions of AES, they don’t pose a practical risk to the full algorithm in real-world use.
Key-Recovery Attacks
Key-recovery attacks attempt to find the secret key used in encryption. Techniques like biclique attacks have been studied for AES-128, AES-192, and AES-256, but they’re incredibly resource-intensive. Even with these methods, it would take more computational power than currently available to break AES when it’s implemented correctly.
Quantum Computing Threats
Quantum computers could weaken AES encryption in the future by drastically speeding up key-recovery attacks through methods like Grover’s Algorithm. This algorithm effectively reduces the key size by half, meaning AES-256 would have the equivalent strength of a 128-bit key. Quantum attacks are a potential threat to AES in the future.
How to Use AES Encryption to Protect Yourself Online
One of the easiest ways to encrypt your online activity is by using a Virtual Private Network (VPN). A VPN secures your internet connection by encrypting all data you send and receive, making it unreadable to anyone trying to intercept it. Most VPNs use military-grade AES 256-bit encryption for this protection.
With a VPN, your online activities like browsing, streaming, or shopping are hidden from hackers and snoopers lurking around on public WiFi. It’s also a great way to change your IP address to another location and access global services.
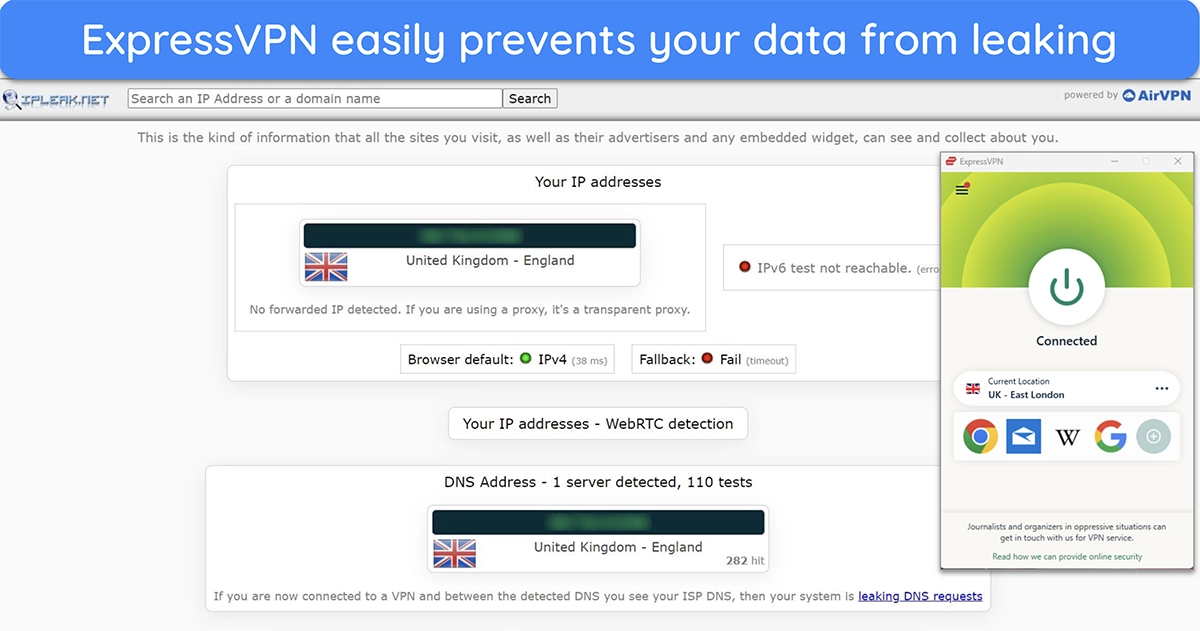
But a VPN isn’t the only way you can protect yourself online; here are some other ways you can use AES (and some ways you probably already do use it):
- Services that use AES encryption — Apps like WhatsApp, Signal, and Google Drive protect your messages and files using AES encryption. Before choosing a service, check if it mentions AES to ensure your data is safe.
- Secure your WiFi network — Switch to the WPA3 protocol for your home WiFi, as it uses AES encryption to protect your network. Avoid outdated protocols like WEP or WPA, which are no longer secure.
- Turn on full-disk encryption — Enable full-disk encryption tools like BitLocker (Windows) or FileVault (Mac). These tools protect all the files on your device, keeping them safe if your laptop or phone is lost or stolen.
- Use encrypted cloud services — Choose cloud storage providers like Tresorit or Sync.com, which encrypt your files locally with AES before uploading them. This ensures your data stays secure, even if the provider’s servers are breached.
- Use encrypted messaging apps — Apps like Signal and WhatsApp use AES encryption to secure your conversations. With end-to-end encryption, only you and the recipient can see your messages, not even the app provider.
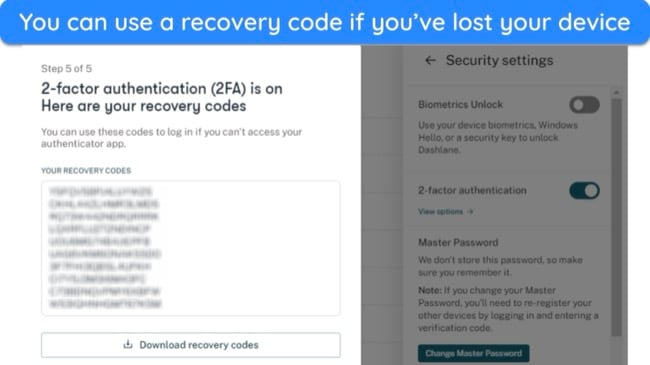
- Use strong passwords and 2FA — Even with AES encryption, weak passwords leave you vulnerable. Use long, unique passwords for every account and enable 2FA. This adds a second layer of security, requiring both your password and a verification code to log in.
![]()
- Avoid old, insecure tools — Stay away from outdated encryption methods like WEP for WiFi or RC4 for secure data. These are easily hackable. Always choose tools and protocols that rely on AES for better protection.
FAQs on AES Encryption
What is AES encryption used for?
Is AES encryption secure?
Yes, AES encryption is highly secure when implemented correctly. Here’s what makes AES so secure. It uses key lengths of 128, 192, or 256 bits, making it resistant to brute-force attacks, as even the smallest key would take billions of years to crack with current technology.
However, quantum computers could pose a future threat. Algorithms like Grover’s can theoretically reduce the effective strength of AES keys by half, but even then, AES-256 would remain secure with the equivalent of a 128-bit key.
How to prevent attacks on AES encryption?
Although AES is highly secure, it’s not invulnerable to attacks. Here are some ways how advanced hackers can exploit it. To prevent attacks on AES encryption, start by using strong, secure keys—256-bit keys offer the best protection. Make sure the encryption is implemented using trusted protocols like WPA3 for WiFi or TLS for online communication.
Using one of the top VPNs in 2025 is the easiest way to secure yourself online. Most VPNs use AES encryption to secure your internet traffic, protecting it from hackers and prying eyes. Combine this with regular software updates and safe key storage to keep your data fully protected.
Get a Reliable VPN That Uses AES Encryption to Protect You Online
AES encryption is the backbone of modern digital security. It protects your data in ways you often don’t see but rely on daily, from messaging apps to online banking. Understanding how it works helps you make smarter choices, like using services and tools that prioritize strong encryption.
For you, this means taking control of your online safety by integrating AES-secured practices. Use encrypted services, secure your WiFi, and consider tools like VPNs and Tor to keep your data private. With proper implementation, AES ensures your personal information stays safe from the wrong hands.
Best VPNs That Use AES Encryption
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.





Leave a Comment
Cancel