Obfuscated VPN Servers — Why You Might Need Them in 2025
Many VPNs highlight obfuscation as one of their key selling points, but what is this feature exactly? It’s a technique that VPNs use to bypass detection methods and advanced firewalls, ensuring uninterrupted internet access no matter where you are.
In this article, I’ll explain how obfuscation works in a VPN and why it’s beneficial. I’ll also show how you can use it and why it’s worth considering a VPN that provides this feature. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
Quick Summary: What is Obfuscation?
Put simply, VPN obfuscation is a technique that disguises VPN traffic as regular internet traffic. This is useful because many websites and countries impose VPN blocks, keeping you from surfing the web while protecting your privacy. So, when changing your IP address alone isn’t enough, using obfuscation circumvents these blocks to keep you safe and anonymous.
VPN Obfuscation: Detailed Explanation
While your ISP and others monitoring your connection can’t see what you’re doing when connected to a VPN, they can tell that you’re using one. However, obfuscation keeps your ISP or anyone else from knowing you’re connected to a VPN, as all traffic gets disguised as regular traffic.
Many VPN protocols have a specific signature that gets identified when traffic is inspected. Advanced firewalls or deep packet inspection can spot this signature and filter traffic with it, blocking a VPN from working. For instance, OpenVPN traffic that isn’t using obfuscation can easily get flagged using packet inspection techniques.
However, obfuscation adds a mask to your traffic, concealing VPN activity by making it look as if you’re using the internet regularly, thus helping bypass firewalls and packet inspection.
Obfuscation Methods and Techniques
VPNs use different obfuscation techniques, the following are some of the common ways traffic is obfuscated to bypass detection mechanisms:
- Shadowsocks proxy. Shadowsocks is an encryption protocol that makes encrypted traffic look like regular HTTPS traffic.
- OpenVPN over SSL/TLS. This method encapsulates VPN traffic within an SSL (or TLS) connection, making it look like normal, secure web traffic.
- OpenVPN Scramble. OpenVPN Scramble adds XOR encryption to OpenVPN traffic, making it appear as random data to bypass simple detection mechanisms.
- Obfsproxy. This technique can conceal Tor and OpenVPN traffic by routing it through Pluggable Transports (PTs) that disguise it as innocent traffic.
- WireGuard with Stealth. Applies obfuscation to the WireGuard protocol by tunneling the traffic over TLS.
Pros and Cons of VPN Obfuscation
Of course, there are both pros and cons to using obfuscation. The following table shows some of the primary advantages and disadvantages:
| Pros | Cons |
| Increased privacy and security while using the internet | Reduces connection speed sometimes because of the overhead added to the connection |
| Bypasses firewalls and inspection to ensure internet access in censorship-heavy countries | Requires technical expertise to configure if the VPN doesn’t enable it by default |
| Ensures access to important websites while traveling overseas | Not offered by every VPN provider at the moment |
Obfuscated Servers
Obfuscated servers in a VPN are the ones that implement the above techniques to mask your traffic. Since obfuscation has pros and cons, some VPN providers may keep these servers separate from others to let you choose exactly when to obfuscate your traffic.
Why You Need VPN Obfuscation
VPN obfuscation is crucial for protecting your privacy online. Masking your VPN traffic as regular traffic offers significant benefits, like the following:
- Overcoming censorship. Obfuscation helps you bypass censorship in countries like China, which use technologies like deep packet inspection to impose strict internet restrictions.
- Avoiding detection. By obfuscating your traffic, this feature ensures your ISP can’t see what you’re doing, helping prevent throttling.
- Preventing surveillance. Since obfuscation disguises VPN traffic as regular traffic, it keeps agencies from surveilling you and singling out someone using a VPN.
- Bypassing network restrictions. Using obfuscation helps bypass internet restrictions imposed by strict firewalls, such as those on public WiFi.
When to Avoid VPN Obfuscation
While VPN obfuscation has many benefits, it’s not always best to enable it because it may slow down your internet connection. Using obfuscation isn’t necessary in situations like the following:
- Streaming. You need the fastest possible speeds to ensure lag-free UHD streams, so keeping obfuscation off is the better choice.
- Gaming. When playing games like Call of Duty: Warzone with a VPN, it’s best to turn off obfuscation to maintain low pings.
Of course, if you’re very privacy-conscious but still want the best speeds, you could get ExpressVPN. I learned during tests that obfuscation is always enabled on ExpressVPN servers, but it never impacts connection speeds. So, this VPN is the optimal choice if you want the strongest security without compromising speeds.
How to Use VPN Obfuscation
Of the top VPNs, multiple choices provide obfuscation. Apps like ExpressVPN have network-wide obfuscation, meaning obfuscation is enabled by default, and you don’t have to configure anything. However, some VPNs like PIA let you enable it manually, which is convenient if you want to choose when to obfuscate your traffic.
Automatic Obfuscation (ExpressVPN)
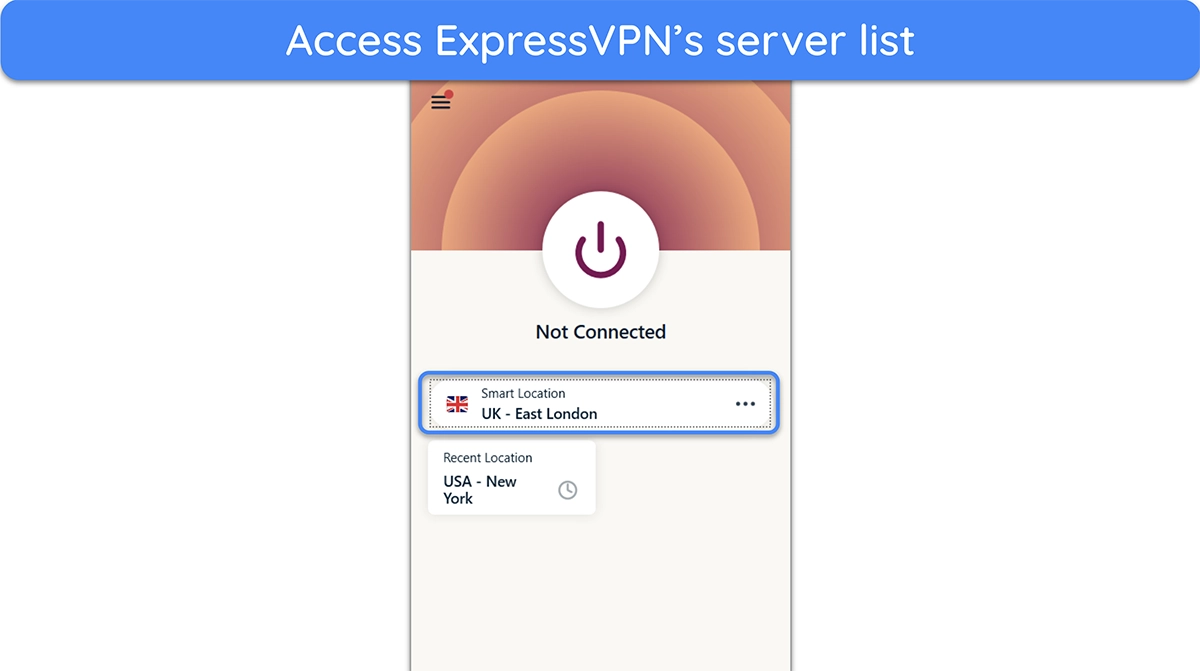
- Open ExpressVPN’s server list. Launch the ExpressVPN app and click on the location option to access its server list.
![Screenshot showing how to access ExpressVPN's list of servers]()
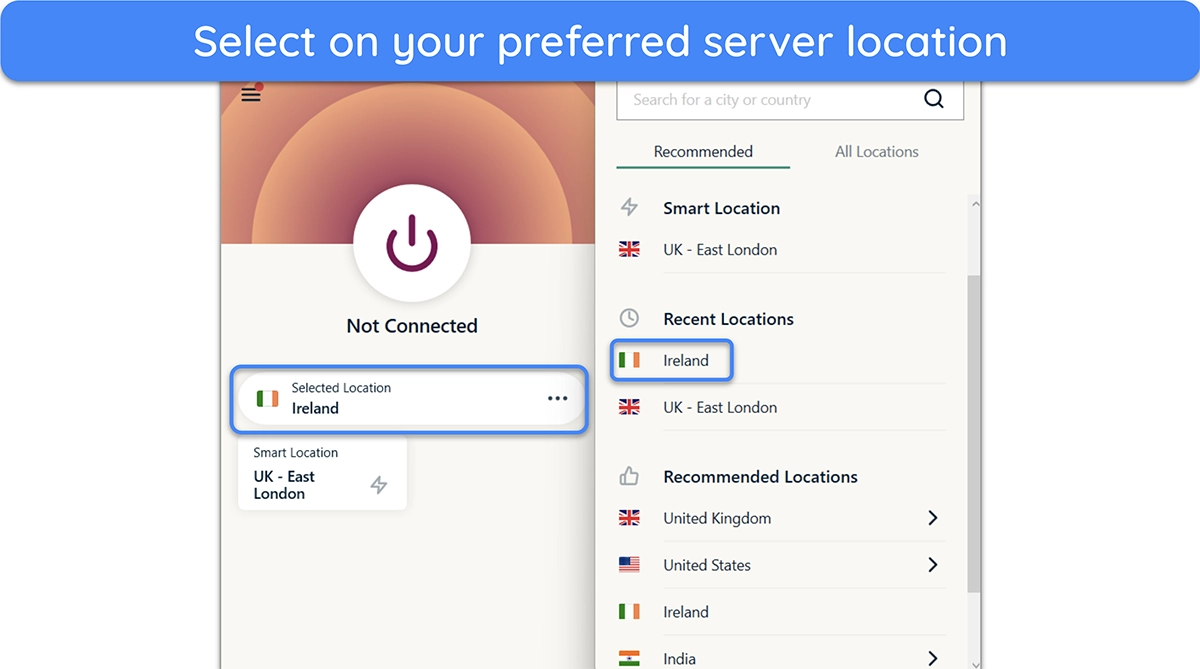
- Choose your server. Click on your preferred server. Picking one close to you will ensure faster speeds.
![Screenshot showing how to choose a preferred ExpressVPN server location]()
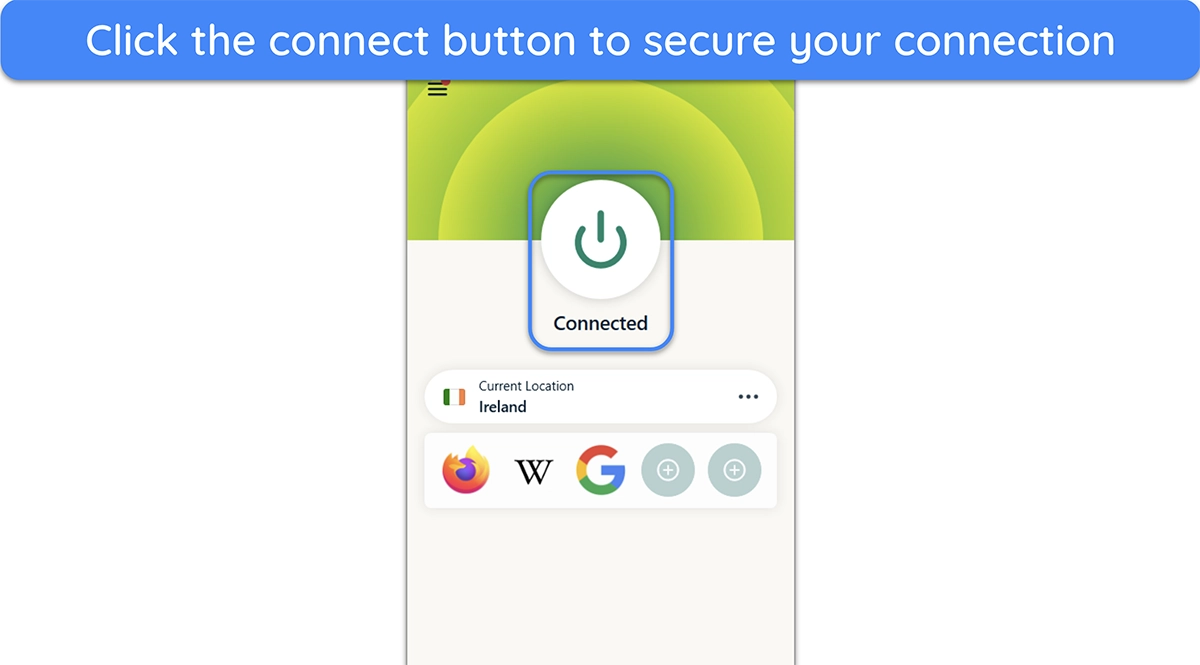
- Connect to ExpressVPN. Click the connect button to connect to ExpressVPN. Obfuscation will work automatically, as ExpressVPN has it enabled across its entire network.
![Screenshot showing how to connect to ExpressVPN]()
Manual Obfuscation (PIA)
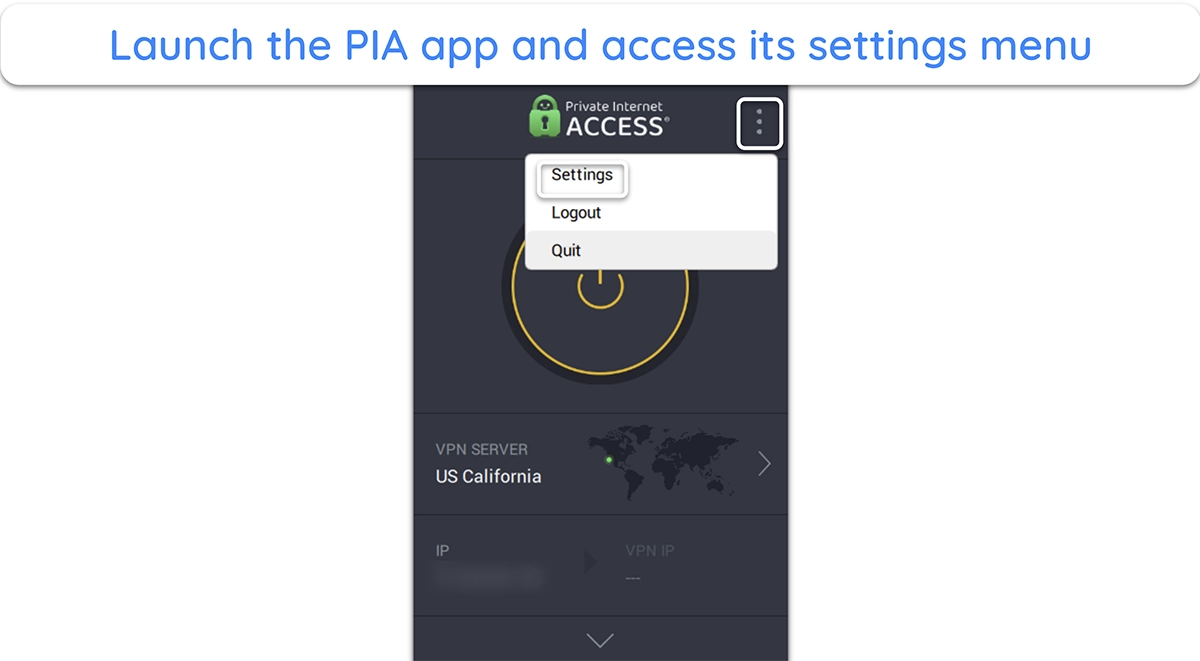
- Access PIA’s settings. Open the PIA app, click the 3 dots at the top-right, and open the settings menu.
![Screenshot showing how to access PIA's settings menu]()
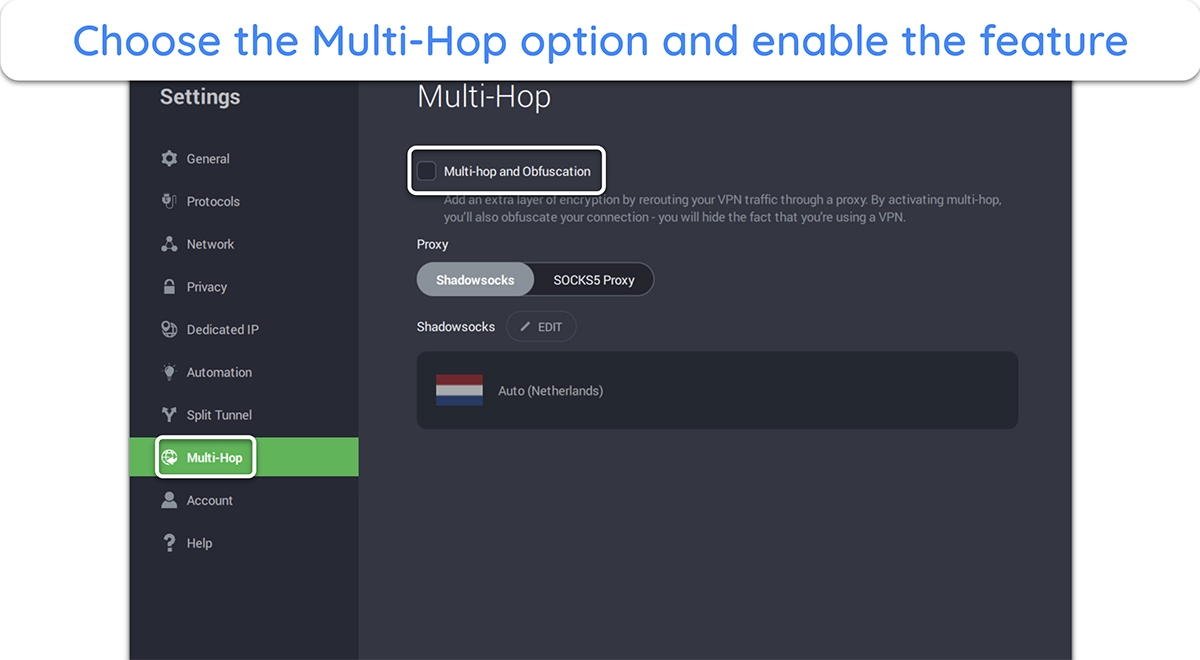
- Enable Multi-Hop and obfuscation. Select Multi-Hop from the left-hand menu and enable this feature by clicking the checkbox.
![Screenshot showing how to enable the Multi-Hop and obfuscation settings in PIA]()
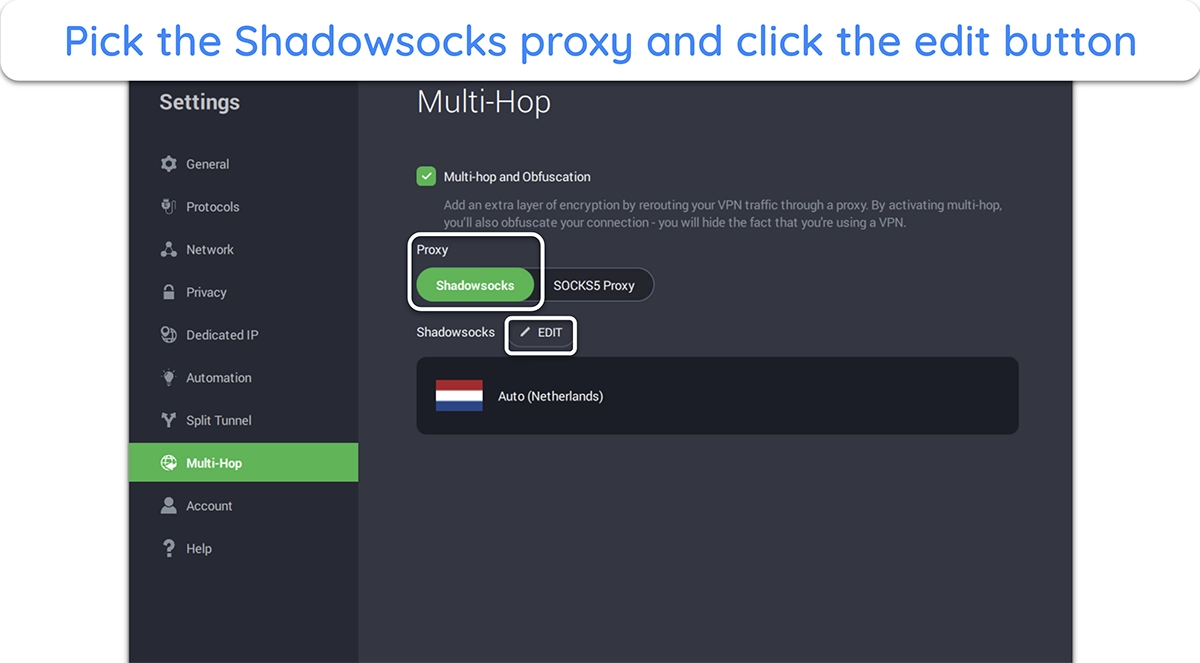
- Choose the Shadowsocks proxy. Select the Shadowsocks proxy once this feature is enabled, and click the edit button to pick a server.
![Screenshot showing how to use the Shadowsocks proxy for obfuscation in PIA]()
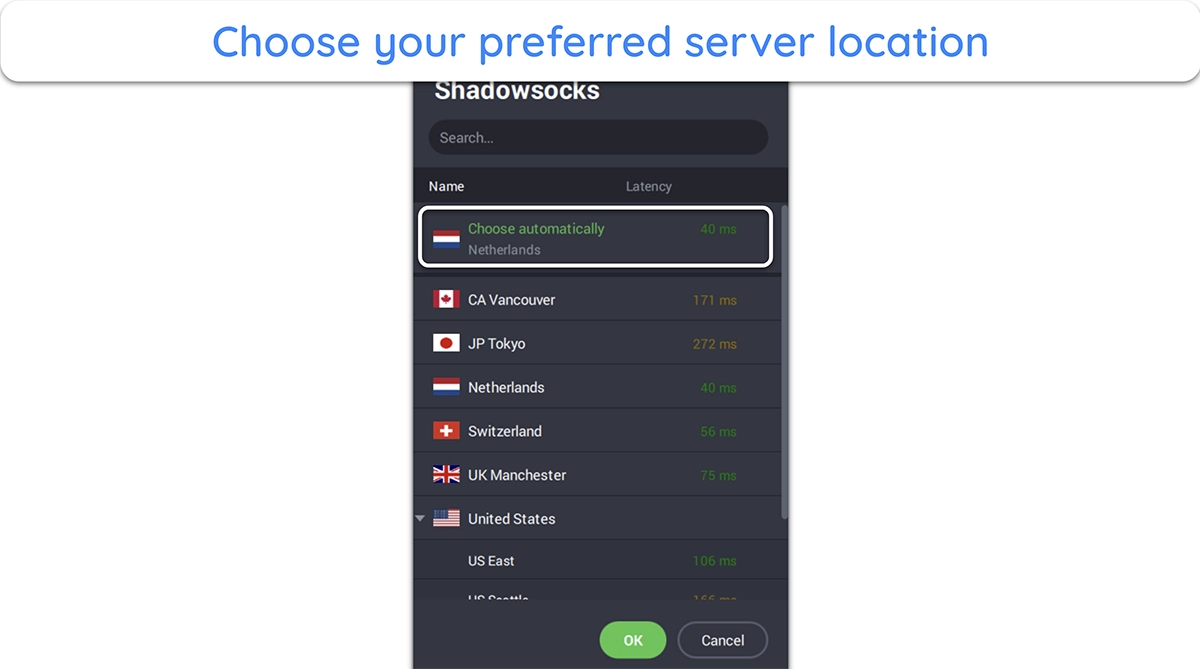
- Choose a server. Pick the Shadowsocks-supported server through which you want to route your traffic.
![Screenshot showing how to choose a preferred server to use with Shadowsocks and Multi-Hop in PIA]()
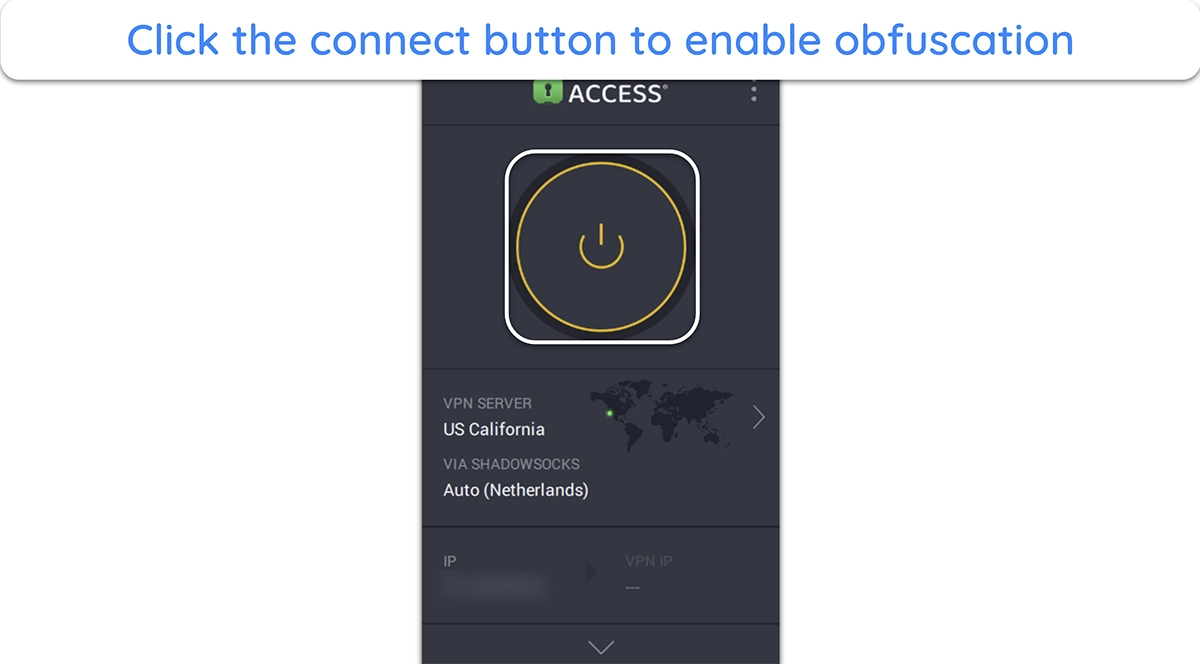
- Connect to PIA. Click the connect button to connect to PIA and enable obfuscation via the Shadowsocks proxy.
![Screenshot showing how to connect to PIA after enabling obfuscation]()
FAQs on Obfuscation
Is there a free VPN with obfuscation features?
Are obfuscated VPN servers slower?
Is VPN obfuscation legal?
What is the best obfuscation method?
Use Obfuscation to Stay Safe and Anonymous Online
Since there are so many advanced VPN detection technologies and firewalls worldwide, it’s clear that getting a VPN with obfuscation is critical nowadays. Otherwise, you risk compromising your privacy when using the internet. Plus, it’s possible that you might not have access to critical websites when visiting a censorship-heavy country.
Thankfully, there are several effective VPNs that offer obfuscation and ensure uninterrupted internet access no matter where you are. If you want to guarantee your safety and anonymity online, it’s worth using one of these to protect your connection.






Leave a Comment
Cancel