Can a VPN Protect From Man-in-the-Middle Attacks
Your sensitive information is at risk of being stolen by hackers when you use the internet. There are multiple types of cyber attacks that threaten your safety — one of them is Man-in-the-Middle (MITM) attacks.
When you use the internet for anything, being vigilant is important. But using a VPN secures your online activities by default, even when your guard is down or you can’t see the threats.
Of all the top VPNs on the market, I recommend ExpressVPN because it has the best security and privacy features. It ensures none of your online activities, transactions, and communications can be accessed by cybercriminals. Get ExpressVPN for protection against MITM attacks and complete peace of mind. It also comes with a 30-day money-back guarantee. Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Quick Guide: Best VPNs to Protect You From MITM Attacks
- ExpressVPN — #1 VPN for protection against MITM attacks, thanks to advanced security features. Sign-up for ExpressVPN to protect yourself against cyber threats.
- CyberGhost — Automatic protection from digital eavesdroppers when using public WiFi, but it has an expensive short-term plan.
- Private Internet Access — Has MACE to block malware and prevent MITM attacks, but it can’t access some streaming services.
Get ExpressVPN to stay safe online
Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
What is a Man-in-the-Middle Attack?
MITM attacks happen when communication between two parties is secretly intercepted by a third party, usually a hacker. The two parties assume they’re the only ones in the conversation and share sensitive information. Once enough details are gathered, the hacker impersonates one of the two parties and steals money or identity.
These attacks can occur in any form of online communication and they’re becoming more common. They’re also difficult to detect since most people don’t realize they’re a victim until there have been significant losses.
What makes it worse, however, is that MITM attacks are extremely easy to carry out. No special hacking skills are required, and many cheap hacking tools are available.
For example, anyone can set up email addresses closely resembling those belonging to two friends. They can then start a conversation with one of them, pretending to be the other. Since many email systems only display names and not email addresses, the ploy can go on until someone’s conned.
To stay safe, pay attention to any difference in tone or language and check the sender’s email address to confirm. A premium VPN like ExpressVPN can prevent more sophisticated MITM attacks.
Get ExpressVPN for online security
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Types of MITM Attacks
1. Email Hijacking
This MITM attack involves compromising and gaining access to a victim’s email account. The hacker monitors the email communications between the victim and others and attacks when enough valuable information is obtained.
For example, the hacker might learn of a transaction that’s about to take place and spoof the recipient’s details to redirect the money. Meanwhile, the victim assumes they’re paying the recipient when they’re actually sending the money to a hacker.
Email hijacking can also involve phishing scams. The hacker directs victims to a fake login page to reveal their online banking credentials. Some trick victims into installing malware that records their keystrokes and sends it to a remote server the attacker owns. A VPN with anti-malware features like PIA is useful in this instance.
2. Session Hijacking
When you visit a website like your bank or webmail, your device connects with the website’s server. This connection is known as a session, that lasts until you log out or close the site.
One of the most common ways hackers hijack sessions is by stealing browser cookies. Cookies improve your browsing experience by storing bits of data like online activity, login credentials, auto-fill form data, and even your location.
Once hackers have them, they can access your bank account and webmail, provided the cookies contain the information they need.
3. WiFi Eavesdropping
If you connect to public WiFi such as in a coffee shop, you may have noticed several networks with similar names. Often, this is because the coffee shop separates networks for customers and staff. But in some cases, one or more networks belong to a hacker. Hackers can also set up fake WiFi access points for the same purpose.
If you connect to a hacker’s network, you’ll place them between your device and the internet. In these instances, a VPN like CyberGhost can protect your WiFi connections so that your online activities are not visible to the attacker. This includes the login credentials of services you accessed while connected to the WiFi.
Hackers can even modify your data in several ways:
1. Replay Attack
Since the hacker sees all your data, they can repeat your activity online. For example, a client sends you an email requesting payment. If the attacker eavesdrops on this message, they can resend it later. Unless you have a reason to be suspicious, you’ll make the payment again.
2. Altered Content
In this case, the hacker uses the data packet to alter the content of a message for personal gains. If you instruct your financial advisor to hold the funds for an investment, the hacker can change the word ‘hold’ to ‘release’ before the message is delivered to your advisor.
The hacker can also make the content simply disappear altogether. If your advisor is waiting for a message to action a transaction, the hacker can make sure it never arrives.
Get ExpressVPN for online security
5 Steps to Protect Against MITM Attacks
Hackers only exploit a few same things over and over to launch an attack. So, prevention usually involves protecting the 2 types of validations:
- The message came from the person or device it says it came from.
- The message has not been changed since it left the sender.
In the online world, this message can be any form of data transmitted online, not just complete emails. So, MITM attack preventive measures usually involve:
1. Secure Communication Protocols
Since MITM methods include HTTPS spoofing, it’s not enough to just enable HTTPS on the web pages that require authentication. Configuring HTTP Strict Transport Security (HSTS) mandates the use of SSL across all subdomains. This enables servers to refuse unsecured connections and makes attacks such as SSL stripping impossible.
2. Employing the Right Security Tools
MITM attacks are enabled by security vulnerabilities but tools like firewalls, up-to-date antiviruses and anti-malware help. Multi-factor authentication adds another level of confirmation, such as fingerprint scanning or an OTP sent to a different device.
3. Using Certificate Pinning
When a browser or app communicates with a site or backend service, there’s a certificate to prove its legitimacy. The process uses a public critical infrastructure where different certificates are presented and checked by the client.
Certificate pinning allows browsers and apps to restrict communication to servers with a valid certificate matching an expected value. If it doesn’t match, the connection is terminated immediately.
4. Conducting Latency Examination
When an attacker intercepts and interferes with data during transmission, it takes unusually long for the data to reach its destination. Latency examination detects unexplained delays, recognizes it as a potential attack, and either alerts the user or shuts down the connection.
5. Use a VPN
Of all the methods above, a VPN is still the best way to prevent MITM attacks. Especially when you use it with other security tools such as a firewall, up-to-date antivirus and anti-malware, and multi-factor authentication.
Although HTTPS provides encryption, it’s only between your browser and the web server. When you use a top-quality VPN, it ensures that all your internet traffic is always encrypted end-to-end.
VPNs are designed to hide this private information to prevent MITM attacks:
- Browsing history — Your browsing history provides clues to your internet activities including the searches you make for a purchase, the email client you use, the banks you access, and more. Hackers can steal these details and manipulate the transactions or purchases you make later.
- IP address — Your IP address reveals your location and your online searches. Since a VPN uses one of its own IP addresses when you connect, yours is hidden. This allows you to maintain your online privacy and search the web anonymously. Especially when you’re using a public device that belongs to a library, school, or an employer.
- Devices — Your desktop computer, laptop, tablet, and smartphone are prime targets for cybercriminals when you access the internet, especially on a public WiFi network. A VPN protects the data you send and receive on your devices so hackers won’t be able to hijack them.
Top VPNs to Protect You From MITM Attacks
1. ExpressVPN — #1 VPN Against MITM Attacks With Top Security Features
Key Features:
- 3,300+ servers in over 105 countries
- Military-grade 256-bit encryption, no-log servers, Network Lock kill switch, and DNS leak protection
- Video tutorials, 24/7 live chat, and email support
- Protect up to 8 devices at any one time
- 30-day money-back guarantee on all plans
ExpressVPN is the #1 VPN for protection against MITM attacks because it has the best security and privacy features to hide your data online. Aside from OpenVPN and IKEv2, ExpressVPN has its own Lightway protocol which uses certificates to protect you against MITM attacks. They’re preloaded to your device to authenticate a VPN server and ensure there’s no one else between you and the internet.
Additionally, ExpressVPN has HMAC, which is an authentication code that protects your data from being altered by an attacker while it’s in transit. Other security and privacy features include:
- AES 256-bit military-grade encryption ensures no one can break into your personal information. The Perfect Forward Secrecy system changes the encryption keys regularly so that hackers can’t use them to decrypt your messages.
- IP leak prevention that prevents your IP address and location from being exposed.
- No-log policy and TrustedServer technology guide the RAM-based servers to wipe all data with every reboot so hackers will find nothing.
- Network Lock blocks all internet traffic so your privacy isn’t compromised when your device changes WiFi networks.
Although all VPNs slow down speed due to the additional encryption, ExpressVPN remained super-fast during testing on different servers. It had the highest speed compared to other VPNs, even on long-distance servers. It stayed consistently between 98 to 109Mbps, making it a practical VPN to stop MITM attacks while working, video conferencing, streaming, or gaming online.
No matter what device you own, you’ll likely be able to secure it from MITM attacks as ExpressVPN is compatible with Mac, Windows, Android, iOS, and more. Plus, the VPN allows up to 8 simultaneous connections.
You can expect to pay slightly more for this VPN. However, as it’s the fastest and most secure against all kinds of security attacks, I believe it to be worth the price. You can subscribe to ExpressVPN’s 2-year plan at per month for the best value. It also comes with a 30-day money-back guarantee so you can get a refund if you’re not completely happy.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
ExpressVPN is compatible with: Windows, macOS, Linux, Android, iOS, Chrome, Firefox, Amazon Fire TV, Fire TV Stick, Kindle Fire, Nook HD, and more.
Stay safe online with ExpressVPN
2025 Update! You can subscribe to ExpressVPN for as low as per month with the 2-year offer (save up to %)! This is a limited offer so grab it now before it's gone. See more information on this offer here.
2. CyberGhost — Secure Devices From MITM Attacks When Using Public WiFi
Key Features:
- 9,757+ servers in 100 countries with additional optimized servers
- Stay protected with military-grade 256-bit encryption, a kill switch, and no-log servers
- Online ticket system, 24/7 live chat assistance, and online guides for help
- Allows you to connect 7 devices at the same time
- 45-day money-back guarantee
CyberGhost offers WiFi protection to prevent MITM attacks by making sure your identity is hidden even if you have to work on the road. Since public WiFi has poor security, hackers can spy on your activities and steal data. To stop this, you can set CyberGhost to automatically start a VPN connection every time your device detects a new WiFi network. It ensures you stay protected even when you don’t realize your device is making random connections.
CyberGhost does not need to store any of your private details on its servers as it’s based in Romania, a privacy haven that’s also not part of any Eyes Alliance.
Besides this, CyberGhost also comes with the following security features enabled by default:
- A strict no-log policy that guarantees your internet activity is not kept anywhere.
- DNS leak protection to keep your real location and IP address private.
- A kill switch that protects your privacy when the internet connection is unstable.
- Military-grade 256-bit AES encryption that keeps data secure to prevent MITM attacks.
In the unlikely event that the encryption is compromised, the Perfect Forward Secrecy system makes sure hackers can’t obtain any usable data.
When it comes to connection speeds, my video calls were smooth except when I connected to a long-distance server. The distance the data traveled resulted in slow speeds and a few instances of the frozen screen. Still, if the focus is on preventing MITM attacks while using a local server, CyberGhost is an excellent choice.
You can protect up to 7 devices at the same time with CyberGhost, whether they run on Windows, Android, Mac, iOS, or another operating system. The 2-year plan is per month and comes with a 45-day money-back guarantee. If you try CyberGhost for protection against MITM attacks and it’s not for you, just ask for a refund.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as CyberGhost VPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
CyberGhost is compatible with: Windows, Android, iOS, Mac, Chrome, Firefox, routers, Amazon Fire TV, consoles, and more.
Stay safe online with CyberGhost
2025 Update! You can subscribe to CyberGhost for as low as per month with a 2-year purchase (save up to %)! This is a limited offer so grab it now before it's gone. See more information on this offer here.
3. Private Internet Access (PIA) — Block Malware With MACE to Stop MITM Attacks
Key Features:
- 35,000+ servers in over 91 countries
- Military-grade 256-bit encryption, MACE ad and malware blocker, and an advanced kill switch
- Online guides, 24/7 live chat, and email support for help
- Protect up to unlimited devices simultaneously
- 30-day money-back guarantee
PIA has MACE to block malware, which is often a tool to carry out man-in-the-browser type of attacks. The hacker infects your browser and injects malicious malware into your device to steal sensitive financial information. MACE is also versatile enough to block Google ads, ad trackers, and even suspicious sites to make browsing the internet safer.
Many of PIA’s security and privacy features are customizable. For example,
- You can choose AES 256-bit encryption to prioritize security over speed. Or AES 128-bit encryption when you need a fast connection.
- PIA’s Advanced Kill Switch stops your devices from connecting to the internet until the VPN is launched.
- DNS leak protection ensures your IP address and actual location are always hidden so hackers can’t target you for an attack.
- A no-log policy makes sure cybercriminals won’t find any personal data to steal.
If you have several devices that are always connected to the internet, PIA will allow up to unlimited of them to be secured at the same time. You also don’t have to worry about compatibility issues as PIA has apps for most operating systems like Mac, Windows, iOS, Android, and more.
In terms of speed, PIA doesn’t even come close to ExpressVPN. But at 65-72Mbps, it’s not bad for streaming movies, online gaming, and video calling without delays.
One of the good things about PIA is that it accepts a wide variety of payment modes including cryptocurrencies and gift cards. For the best deal, try PIA’s 2-year plan at per month. It comes with a 30-day money-back guarantee so if it doesn’t meet your expectations, you can ask for a refund.
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
PIA is compatible with: Windows, Android, iOS, Mac, Linux, Chrome, Firefox, consoles, and more.
FAQ: Protecting Against MITM Attacks With a VPN
Are man-in-the-middle attacks common?
They may not be as common as other cyber crimes, but estimates indicate 35% of cyber threats in past years were MITM attacks. There are many types of MITM attacks and when carried out carefully, they can lead to massive losses.
One MITM attack rerouted $1 million from a Chinese venture capital firm meant for an Israeli startup to hackers. The operation involved eavesdropping, fake email domains, and impersonation of parties involved to divert the transaction. The hackers also canceled a face-to-face meeting to avoid any form of verification.
Can you detect man-in-the-middle attacks?
If you aren’t actively monitoring your communications for the interception, MITM attacks can go unnoticed until it’s too late. The best way to prevent data interception is by encrypting it. The best VPNs for protection against MITM attacks can help achieve this.
Some tell-tale signs of eavesdropping include:
- frequent disconnection or connections to unfamiliar locations.
- repeated and unexpected disruption of a particular service. Attackers forcefully disconnect your session to intercept authentication information when you try to reconnect.
- website links that vary from the actual website for example, when a device repeatedly tries to connect to ‘g00gle.com’ instead of ‘google.com’.
Will a VPN protect me from other cyber attacks?
Yes. Cyber attacks occur in many forms but here are just a few others that VPNs can help prevent:
- Distributed Denial of Service (DDoS) attacks — DDoS forces people (often gamers) offline. It floods a network with unwanted requests and traffic until a site can’t handle the influx, preventing legitimate traffic from coming through. VPNs are one of the best tactics to prevent DDoS attacks because it hides IP addresses, making it much harder to target you. However, if a hacker already knows your computer’s IP address or a DDoS attack is already in progress, there isn’t much a VPN can do.
- Identity theft — This is when cybercriminals pilfer your personal data and employ it to impersonate you or engage in illicit activities on your behalf. They have the ability to seize control of your financial account, initiate the opening of new accounts, submit tax returns in your identity, forge a fresh passport, or even make real estate transactions, all in your name. A VPN can help prevent identity theft by creating an encrypted tunnel for the data you send and receive online to keep them safe from cyber thieves.
- Cryptojacking — Cryptojacking involves secretly installing jacking software to your device to force cryptocurrency mining for someone else. Since it leeches on your device’s processing power, it becomes slower and consumes more energy. VPNs like ExpressVPN can give you the ability to mask your IP address and prevent others from targeting your devices.
Can I use a free VPN against man-in-the-middle attacks?
I don’t recommend using a free VPN to prevent MITM attacks since even the best free VPNs have limited security features. Others have limited bandwidth and servers that result in overcrowding and slow speeds. The worst free VPNs contain malware that makes it easier for cybercriminals to hack you. Or they secretly sell your data, risking your security and privacy.
A better way to protect yourself online is by taking advantage of a money-back guarantee of a premium VPN like CyberGhost. You can use it for free and then ask for a refund within 45 days.
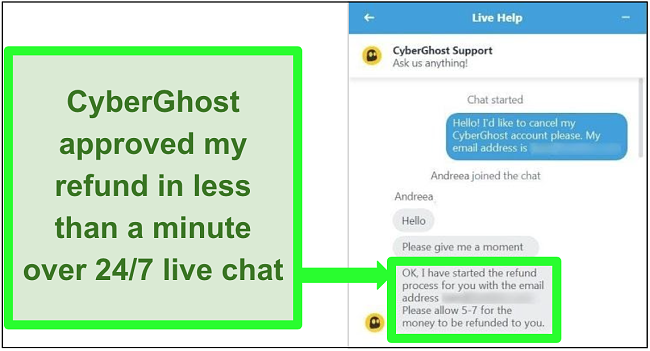
Get CyberGhost for extra online safety
Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as CyberGhost VPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Protect Against Man-in-the-Middle Attacks With a VPN
It’s good to be vigilant when you’re using the internet. Validating an email instruction related to payment, clearing browser cache, and avoiding suspicious WiFi networks can make sure you don’t become a MITM attack victim.
However, no matter how careful you are, your internet traffic and activities are exposed to hackers if you don’t use a VPN. As long as your real IP address is visible, hackers can launch any type of attack on you.
Get ExpressVPN for advanced security features to ensure everything you do online is hidden from cybercriminals. It also comes with a 30-day money-back guarantee.
Get ExpressVPN to stop MITM attacks
Summary: The Top VPNs to Protect Against MITM Attacks in 2025
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.








Leave a Comment
Cancel